̈ Chapter 14: Virtual Private Networks—VPN LANCOM Reference Manual LCOS 3.50
295
Virtual Private Networks—
VPN
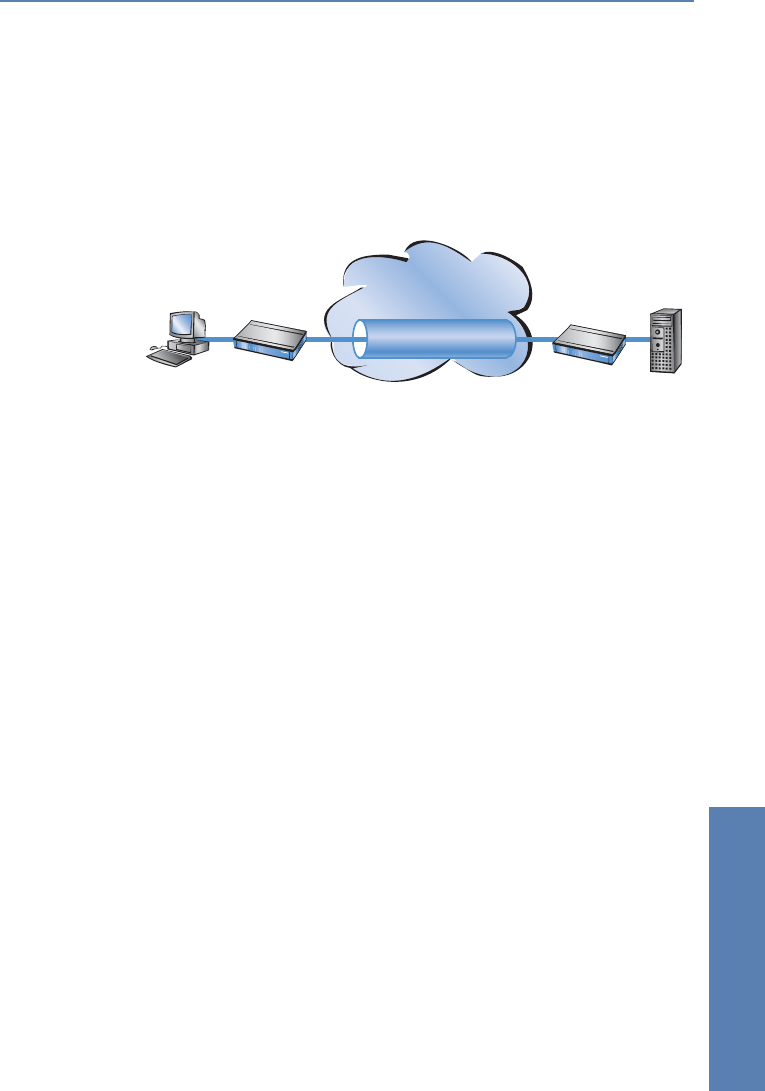
the Internet. With the proper technology, third parties can monitor and even
record data traffic. As the packets are encrypted by VPN, the actual content of
the packets is inaccessible. Experts compare this state to a tunnel: it's open at
either end, but perfectly shielded in between. Secure connections within
public IP networks are thus also referred to as "tunnels".
.
The goal of modern network structures has thus been achieved: secure
connections via the largest and most low-cost public IP network: the Internet.
14.2 LANCOM VPN: an overview
14.2.1 VPN example application
VPN connections are used in many different fields of application. In most
cases, a variety of communications technologies is used for transferring both
data and audio, and VPN unites these systems into an integrated network. The
Internet
VPN tunnel


















