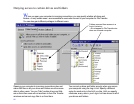
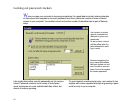
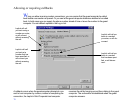
. . .
63
4 Setting up
security for
incoming
connections
64 Allowing incoming connections
66 Denying access to certain drives and folders
68 Locking out password crackers
70 Allowing or requiring callbacks
72 Protecting your security settings with a password
74 Encrypting information over incoming connections