. . . Disabling the host keyboard and mouse and blanking its screen
87
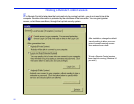
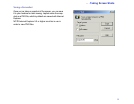
You grant locking permission by changing the security setup
on the host computer: Click the Security button on the Link
-
Bar. You then have a choice:
• Set up a Log-in List by specifying Log-in List (Protected
System) and adding one or more entries. In each entry,
check any of the three boxes under Locking Permis
-
sions. The permissions apply only to guests whom you
provide with the appropriate log-in name and password.
For more information about setting up a Log-in List, see
”Allowing incoming connections.
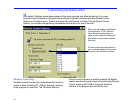
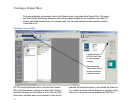
• If security is not an issue, open the system to any
LapLink user by clicking Anybody (Public System).
Click the Public Privileges button. On the General tab,
check the Remote Control box, and then check any of
the three boxes under Locking Permissions. The per
-
missions apply to all guests.
Locking the host from the guest
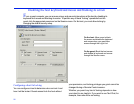
With the permission of the host computer, you can:
Blank the host screen The host’s screen is darkened,
preventing your work from being viewed at the host.
• Disable the host mouse The host’s mouse is locked,
preventing anyone at the host from using the mouse to
interrupt your work.
• Disable the host keyboard The host’s keyboard is
locked, preventing anyone at the host from using the
keyboard to interrupt your work.
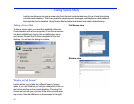
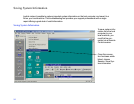
To lock the host during a Remote Control session:
• On the Session menu, click any of these commands to
place a check mark beside the command: Blank Host
Screen, Lock Host Mouse, or Lock Host Keyboard.
• To disable locking, click the command again to clear the
check mark.
TIP If a command is dimmed, it is not available: either the
host cannot perform the action, or the security setup of the
host computer does not allow it. Support for screen blank
-
ing is determined by test performed after the installation of
LapLink Gold Corporate, and after any changes to the
Windows display settings.
TIP The Session menu is available only when you are
connected to another computer.
TIP Through the Address Book, you can request the
kinds of locking you want to take effect as soon as you
open a Remote Control session. Your requests will be
honored as long as they are allowed by the host. For infor
-
mation on using the Address Book to make connections,
see
”Using the Address Book.