WFS709TP ProSafe Smart Wireless Switch Software Administration Manual
12-4 Configuring Wireless Intrusion Protection
v1.0, June 2007
Configuring Rogue AP Detection
Follow the steps below to configure the network to detect insecure APs and to classify them as
rogue and interfering respectively as defined in the section above.
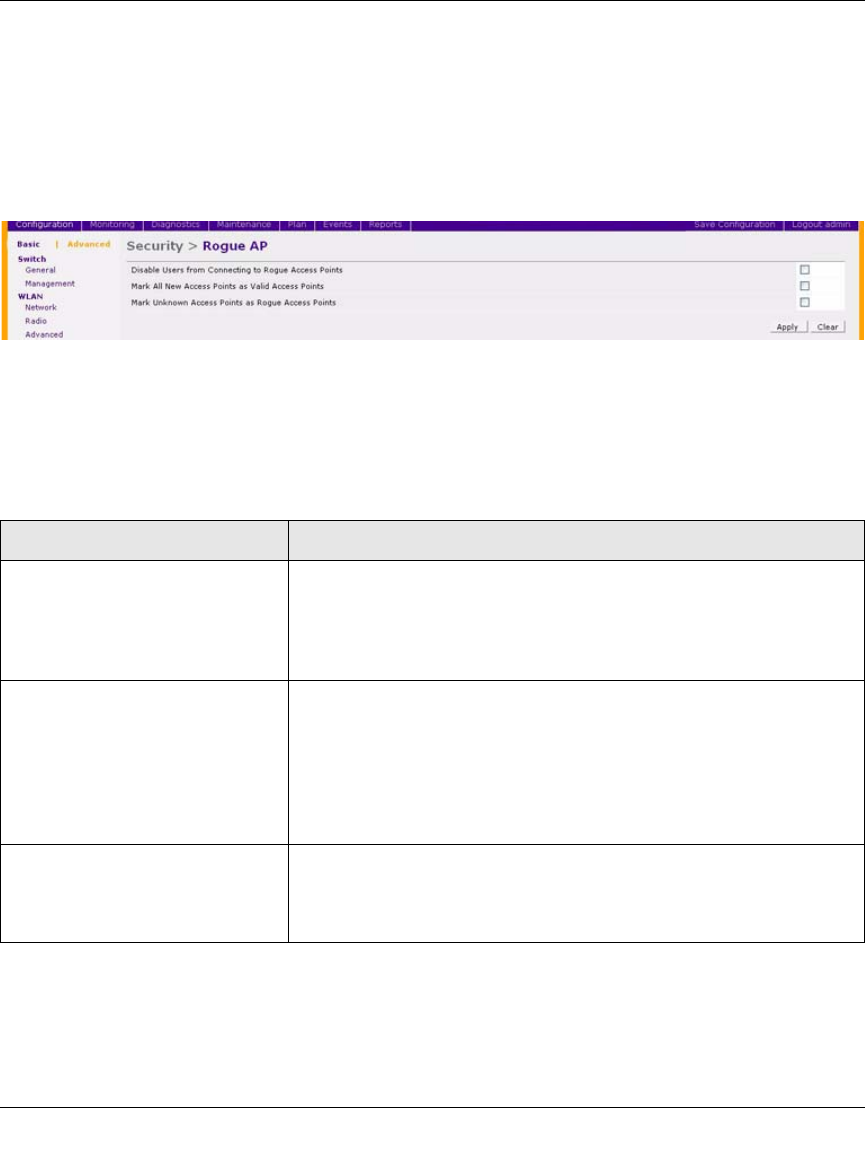
Navigate to the Configuration > Advanced > Security > Rogue AP page on the browser interface
of the master WFS709TP (Figure 12-3).
Table 12-1 explains the fields for this configuration and what it means to select each of them.
Figure 12-3
Table 12-1. AP Classifications
FIeld Description
Disable Users from Connecting to
Rogue Access Points
By default, rogue APs are only detected, but are not automatically
disabled. Enable this option to automatically shut down rogue APs.
When this option is enabled, clients attempting to associate to a rogue
AP will be disconnected from the rogue AP through a denial of service
attack.
Mark All New Access Points as
Valid Access Points
When installing a WFS709TP in an environment with an existing third-
party wireless network, it is necessary to manually classify existing
enterprise APs as valid—a time-consuming process if a large number
of APs are installed. Enable this option to mark all detected APs as
valid. Leave this option enabled until all enterprise APs have been
detected and classified as valid. After this process has completed,
disable this option and re-classify any unknown APs as interfering.
Mark Unknown Access Points as
Rogue Access Points
In an environment where no interfering APs should exist—for example,
a building far away from any other buildings or an RF-shielded
building—enable this option to turn off the classification process. Any
AP detected that is not classified as valid will be marked as rogue.
