Using the Policy WizardUsing the 8950 AAA Policy Assistant in Server
Management Tool
............................................................................................................................................................................................................................................................
365-360-001R6.0
Issue 1, December 2008
9-11
............................................................................................................................................................................................................................................................
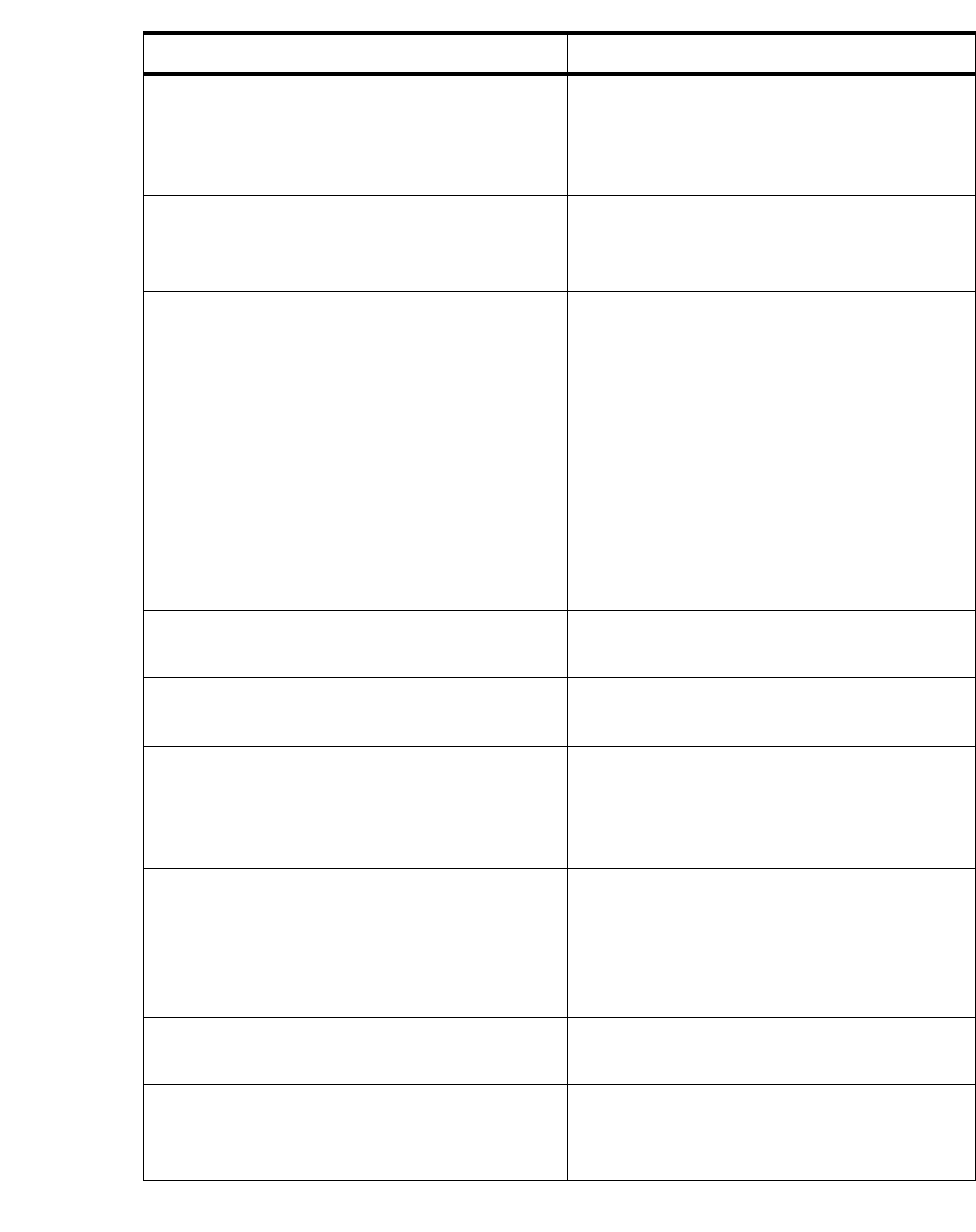
Windows Security Access Manager Uses Windows NT or Security Access
Manager (SAM) to verify the password in
the user request. This option is only
supported on Microsoft Windows platforms.
UNIX System Uses UNIX system functions to verify the
password in the user request. This option is
only supported on a UNIX platform.
UNIX Password File Reads the password in the user’s entry
directly from a UNIX password or shadow
file. The password read from the file is used
to authenticate the request in place of any
password that is in the user profile.
The UNIX/Linux password can be one of the
following formats: UNIX Crypt, MD5, SHA,
or SSHA. Although primarily used on UNIX
platforms, this option can be used to read
users from a UNIX password style file on
any platform.
RSA ACE/Server (SecurID) Uses an RSA Ace Server to verify the one
time password from a SecurID token.
Secure Computing SafeWord Server Uses the SafeWord Server from Secure
Computing to verify the one time password.
LDAP Directory Connects to an LDAP Server using the User-
Name and password from the request. If the
LDAP connection is successful, the user is
authenticated.
Microsoft Active Directory Connects to a Microsoft Active Directory
Server using the User-Name and password
from the request. If the Active Directory
connection is successful, the user is
authenticated.
Automatic Authentications These options skip the password check and
either automatically accept or reject all users.
Accept All Request The password is not checked. However, other
checks defined in this policy, including
session limits, are still enforced.
Table 9-1 Authentication Types
Option Description


















