142 Fortinet Inc.
Addresses Firewall configuration
Default firewall configuration
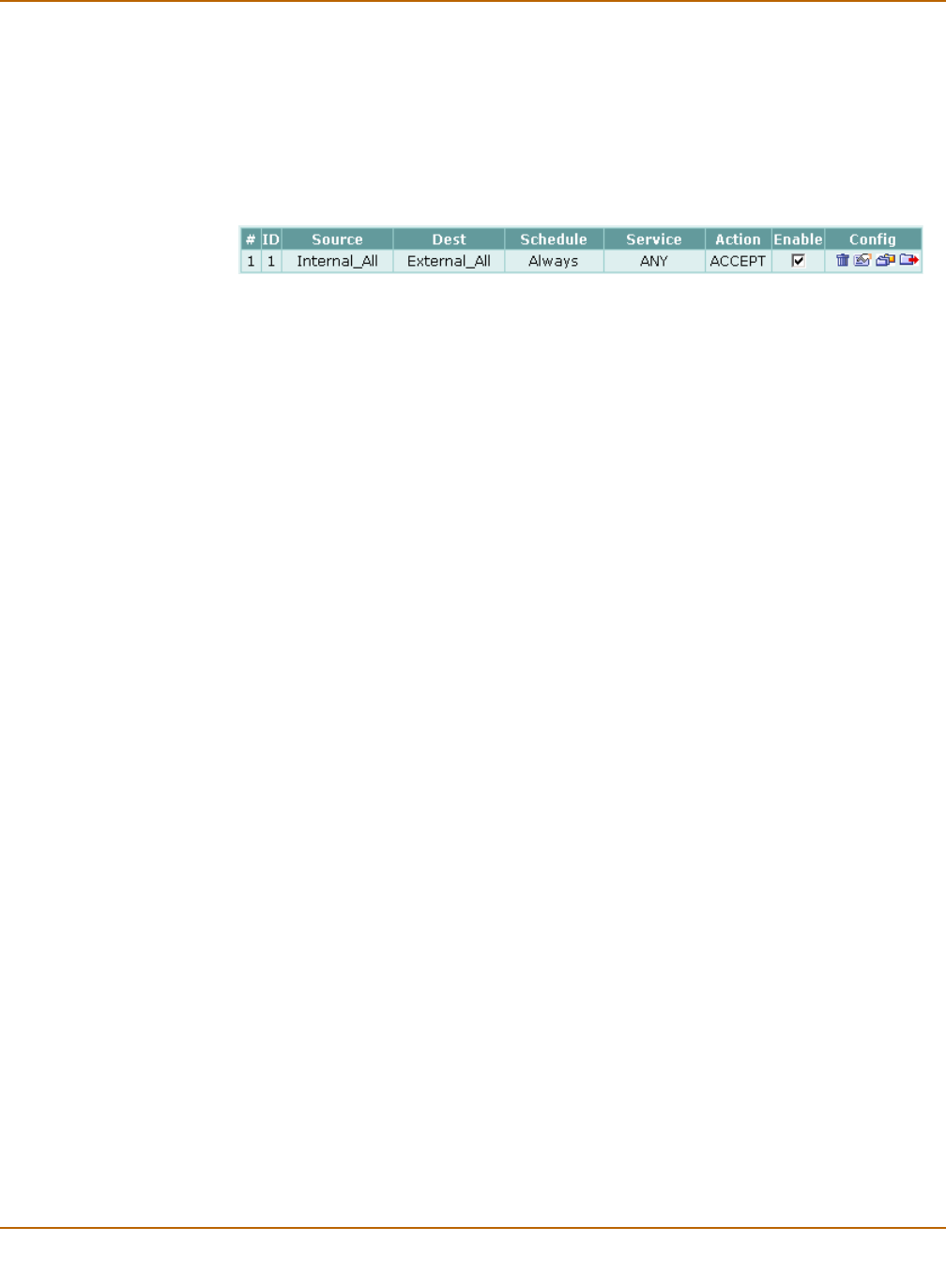
By default, the users on your internal network can connect through the FortiGate unit
to the Internet. The firewall blocks all other connections. The firewall is configured with
a default policy that matches any connection request received from the internal
network and instructs the firewall to forward the connection to the Internet.
Figure 4: Default firewall policy
• Addresses
• Services
• Schedules
• Content profiles
Addresses
Add policies to control connections between FortiGate interfaces and between the
networks connected to these interfaces. To add policies between interfaces, the
interfaces must include addresses. By default the FortiGate unit is configured with the
following firewall addresses:
• Internal_All, added to the internal interface, this address matches all addresses on
the internal network.
• External_All, added to the external interface, this address matches all addresses
on the external network.
• DMZ_All, added to the DMZ interface, this address matches all addresses on the
DMZ network.
The firewall uses these addresses to match the source and destination addresses of
packets received by the firewall. The default policy matches all connections from the
internal network because it includes the Internal_All address. The default policy also
matches all connections to the external network because it includes the External_All
address.
You can add more addresses to each interface to improve the control you have over
connections through the firewall. For more information about firewall addresses, see
“Addresses” on page 150.
You can also add firewall policies that perform network address translation (NAT). To
use NAT to translate destination addresses, you must add virtual IPs. Virtual IPs map
addresses on one network to a translated address on another network. For more
information about Virtual IPs, see “Virtual IPs” on page 160.


















