110
In This Chapter
User Groups .......................................................................................... 110
Users ..................................................................................................... 119
Authentication Settings .......................................................................... 122
Changing a Password ........................................................................... 134
User Groups
The KX II stores an internal list of all user and group names to determine
access authorization and permissions. This information is stored
internally in an encrypted format. There are several forms of
authentication and this one is known as local authentication. All users
have to be authenticated. If the KX II is configured for LDAP/LDAPS or
RADIUS, that authentication is processed first, followed by local
authentication.
Every KX II is delivered with three default user groups. These groups
cannot be deleted:
User
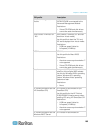
Description
Admin
Users that are members of this group have full
administrative privileges. The original, factory-default
user is a member of this group and has the complete
set of system privileges. In addition, the Admin user
must be a member of the Admin group.
Unknown
This is the default group for users who are
authenticated externally using LDAP/LDAPS or
RADIUS or who are unknown to the system. If the
external LDAP/LDAPS or RADIUS server does not
identify a valid user group, the Unknown group is
used. In addition, any newly created user is
automatically put in this group until assigned to
another group.
Individual
Group
An individual group is essentially a “group” of one.
That is, the specific user is in its own group, not
affiliated with other real groups. Individual groups can
be identified by the “@” in the Group Name. The
individual group allows a user account to have the
same rights as a group.
Up to 254 user groups can be created in the KX II. Up to 254 user
groups can be created in the KX II.
Chapter 7
User Management