5-5
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 5 Configuring Twice NAT (ASA 8.3 and Later)
Configuring Twice NAT
• If you enable extended PAT for a dynamic PAT rule, then you cannot also use an address in the PAT
pool as the PAT address in a separate static NAT with port translation rule. For example, if the PAT
pool includes 10.1.1.1, then you cannot create a static NAT-with-port-translation rule using 10.1.1.1
as the PAT address.
• Extended PAT can consume a large amount of memory because NAT pools are created for each
unique destination, which in turn uses up memory. This may lead to memory exhaustion quickly
even with less number of connections.
• If you use a PAT pool and specify an interface for fallback, you cannot specify extended PAT.
• For VoIP deployments that use ICE or TURN, do not use extended PAT. ICE and TURN rely on the
PAT binding to be the same for all destinations.
For round robin for a PAT pool:
• (8.4(3) and later, not including 8.5(1) or 8.6(1)) If a host has an existing connection, then subsequent
connections from that host will use the same PAT IP address if ports are available. Note: This
“stickiness” does not survive a failover. If the ASA fails over, then subsequent connections from a
host may not use the initial IP address.
• (8.4(2), 8.5(1), and 8.6(1)) If a host has an existing connection, then subsequent connections from
that host will likely use different PAT addresses for each connection because of the round robin
allocation. In this case, you may have problems when accessing two websites that exchange
information about the host, for example an e-commerce site and a payment site. When these sites
see two different IP addresses for what is supposed to be a single host, the transaction may fail.
• Round robin, especially when combined with extended PAT, can consume a large amount of
memory. Because NAT pools are created for every mapped protocol/IP address/port range, round
robin results in a large number of concurrent NAT pools, which use memory. Extended PAT results
in an even larger number of concurrent NAT pools.
Detailed Steps
To configure dynamic NAT, perform the following steps:
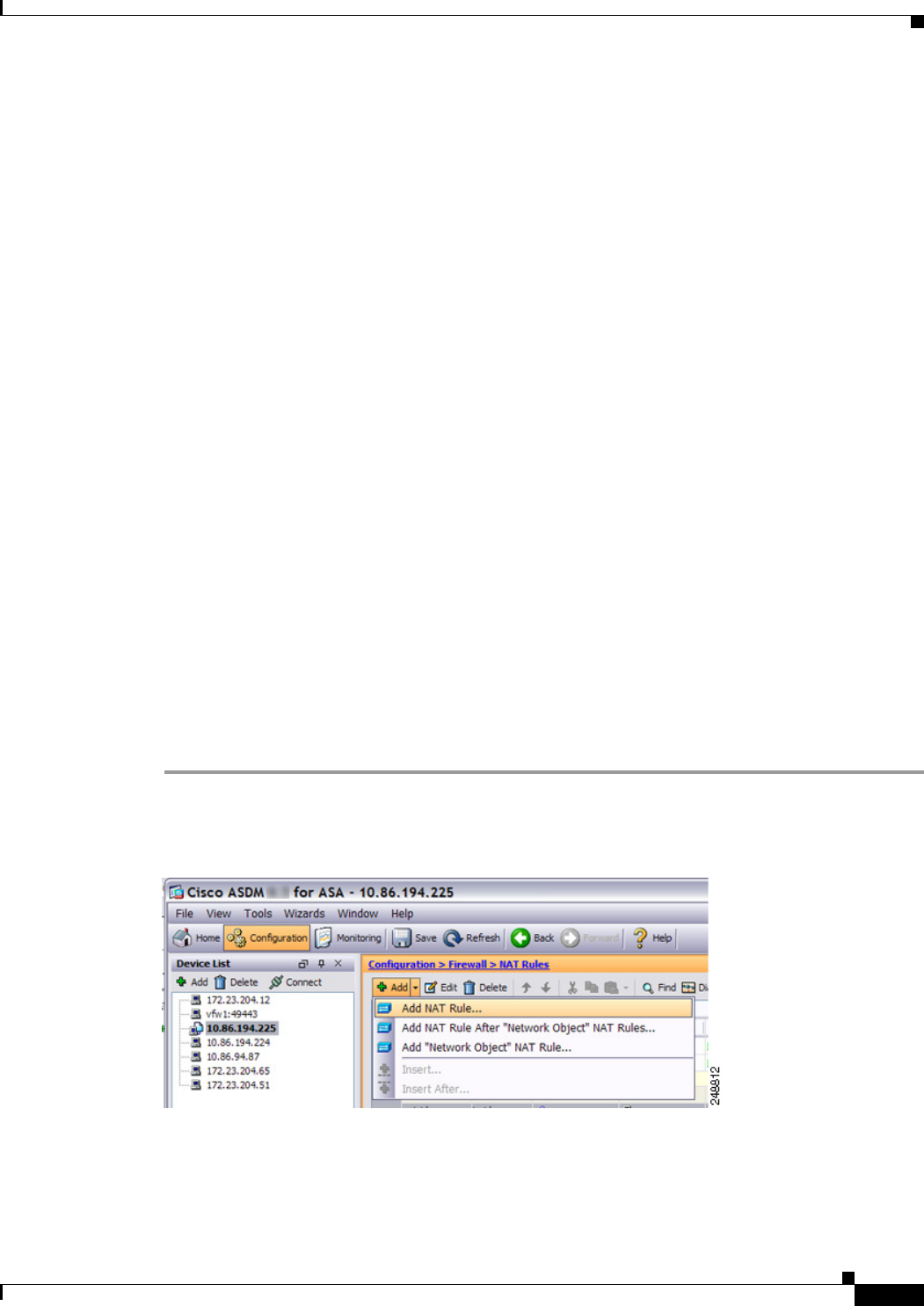
Step 1 Choose Configuration > Firewall > NAT Rules, and then click Add.
If you want to add this rule to section 3 after the network object rules, then click the down arrow next to
Add, and choose Add NAT Rule After Network Object NAT Rules.
The Add NAT Rule dialog box appears.