6-2
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 6 Configuring NAT (ASA 8.2 and Earlier)
NAT Overview
general operations configuration guide for more information about security levels. See the “NAT
Control” section on page 6-4 for more information about NAT control.
Note In this document, all types of translation are referred to as NAT. When describing NAT, the terms inside
and outside represent the security relationship between any two interfaces. The higher security level is
inside and the lower security level is outside. For example, interface 1 is at 60 and interface 2 is at 50;
therefore, interface 1 is “inside” and interface 2 is “outside.”
Some of the benefits of NAT are as follows:
• You can use private addresses on your inside networks. Private addresses are not routable on the
Internet.
• NAT hides the real addresses from other networks, so attackers cannot learn the real address of a
host.
• You can resolve IP routing problems such as overlapping addresses.
See Table 10-1 on page 10-4 for information about protocols that do not support NAT.
NAT in Routed Mode
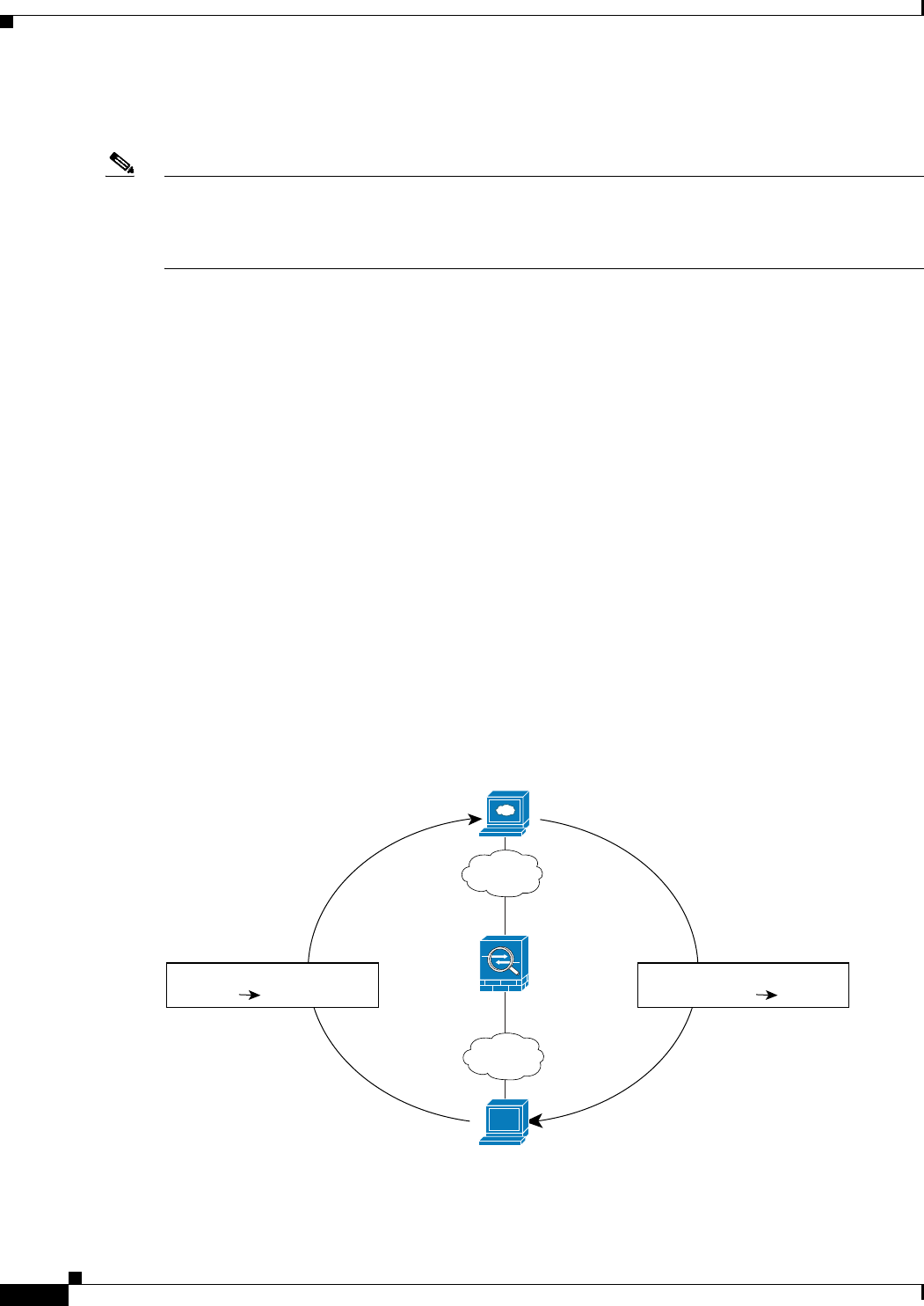
Figure 6-1 shows a typical NAT example in routed mode, with a private network on the inside. When the
inside host at 10.1.1.27 sends a packet to a web server, the real source address, 10.1.1.27, of the packet
is changed to a mapped address, 209.165.201.10. When the server responds, it sends the response to the
mapped address, 209.165.201.10, and the security appliance receives the packet. The security appliance
then changes the translation of the mapped address, 209.165.201.10 back to the real address, 10.1.1.1.27
before sending it to the host.
Figure 6-1 NAT Example: Routed Mode
Web Server
www.cisco.com
Outside
Inside
209.165.201.2
10.1.2.1
10.1.2.27
130023
Translation
209.165.201.1010.1.2.27
Originating
Packet
Undo Translation
209.165.201.10 10.1.2.27
Responding
Packet
Security
Appliance


















