6-5
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 6 Configuring NAT (ASA 8.2 and Earlier)
NAT Overview
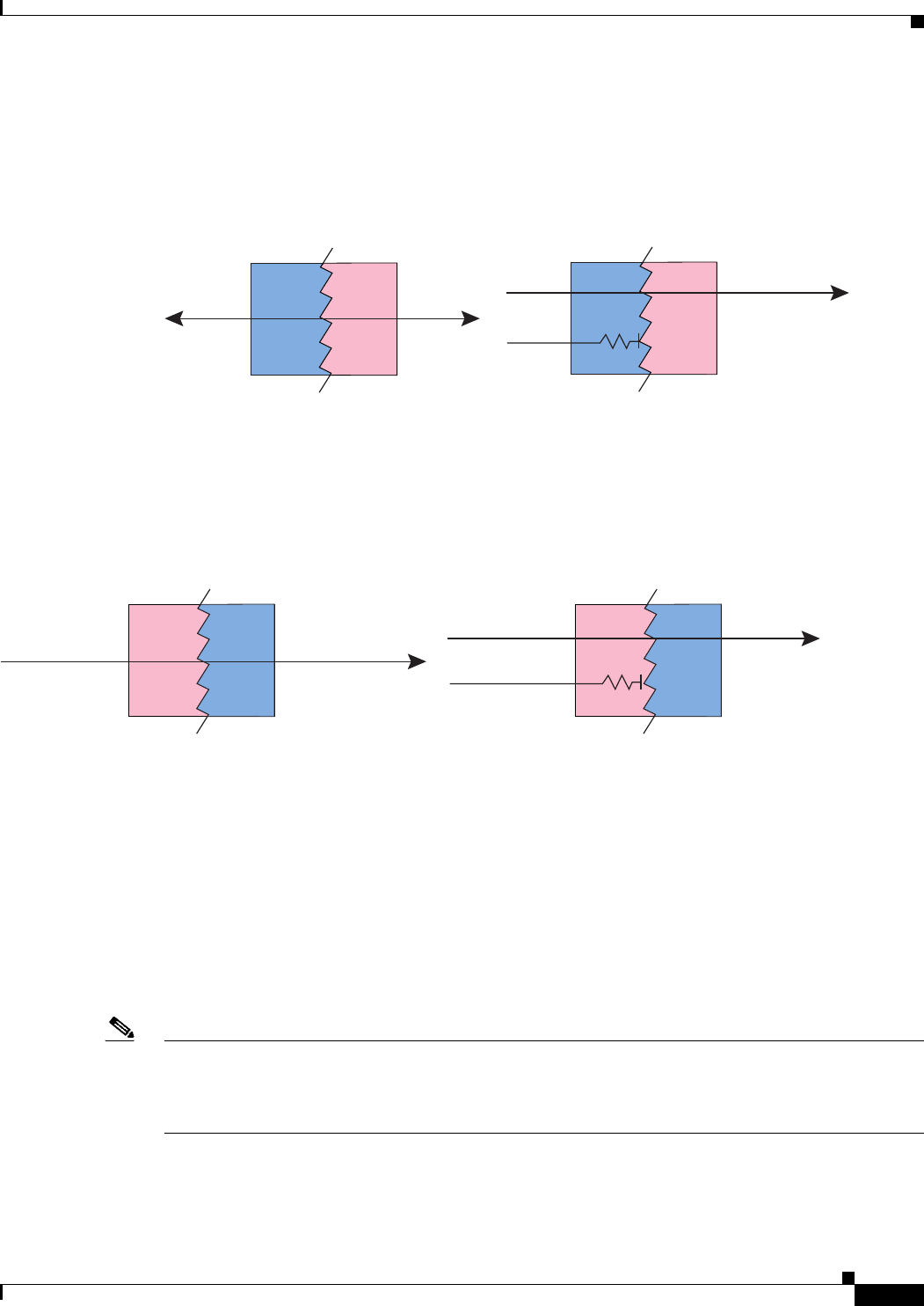
Interfaces at the same security level are not required to use NAT to communicate. However, if you
configure dynamic NAT or PAT on a same security interface, then all traffic from the interface to a same
security interface or an outside interface must match a NAT rule, as shown in Figure 6-4.
Figure 6-4 NAT Control and Same Security Traffic
Similarly, if you enable outside dynamic NAT or PAT, then all outside traffic must match a NAT rule
when it accesses an inside interface (see Figure 6-5).
Figure 6-5 NAT Control and Inbound Traffic
Static NAT does not cause these restrictions.
By default, NAT control is disabled; therefore, you do not need to perform NAT on any networks unless
you want to do so. If you upgraded from an earlier version of software, however, NAT control might be
enabled on your system. Even with NAT control disabled, you need to perform NAT on any addresses
for which you configure dynamic NAT. See the “Dynamic NAT Implementation” section on page 6-17
for more information about how dynamic NAT is applied.
If you want the added security of NAT control but do not want to translate inside addresses in some cases,
you can apply a NAT exemption or identity NAT rule on those addresses. (See the “Using NAT
Exemption” section on page 6-33 for more information).
To configure NAT control, see the “Configuring NAT Control” section on page 6-16.
Note In multiple context mode, the packet classifier might rely on the NAT configuration to assign packets to
contexts if you do not enable unique MAC addresses for shared interfaces. See the “How the ASA
Classifies Packets” section on page 8-3 in the general operations configuration guide for more
information about the relationship between the classifier and NAT.
10.1.1.1
Dyn. NAT
No NAT
209.165.201.1
Level 50 Level 50
or
Outside
10.1.2.1
Security
Appliance
10.1.1.1 10.1.1.1
No NAT
Level 50 Level 50
Security
Appliance
132215
209.165.202.129
No NAT
209.165.202.129
Outside Inside
Security
Appliance
209.165.202.129
209.165.200.240
Dyn. NAT
10.1.1.50
Outside Inside
Security
Appliance
No NAT
132213


















