19-3
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 19 Configuring Cisco Mobility Advantage
Information about the Cisco Mobility Advantage Proxy Feature
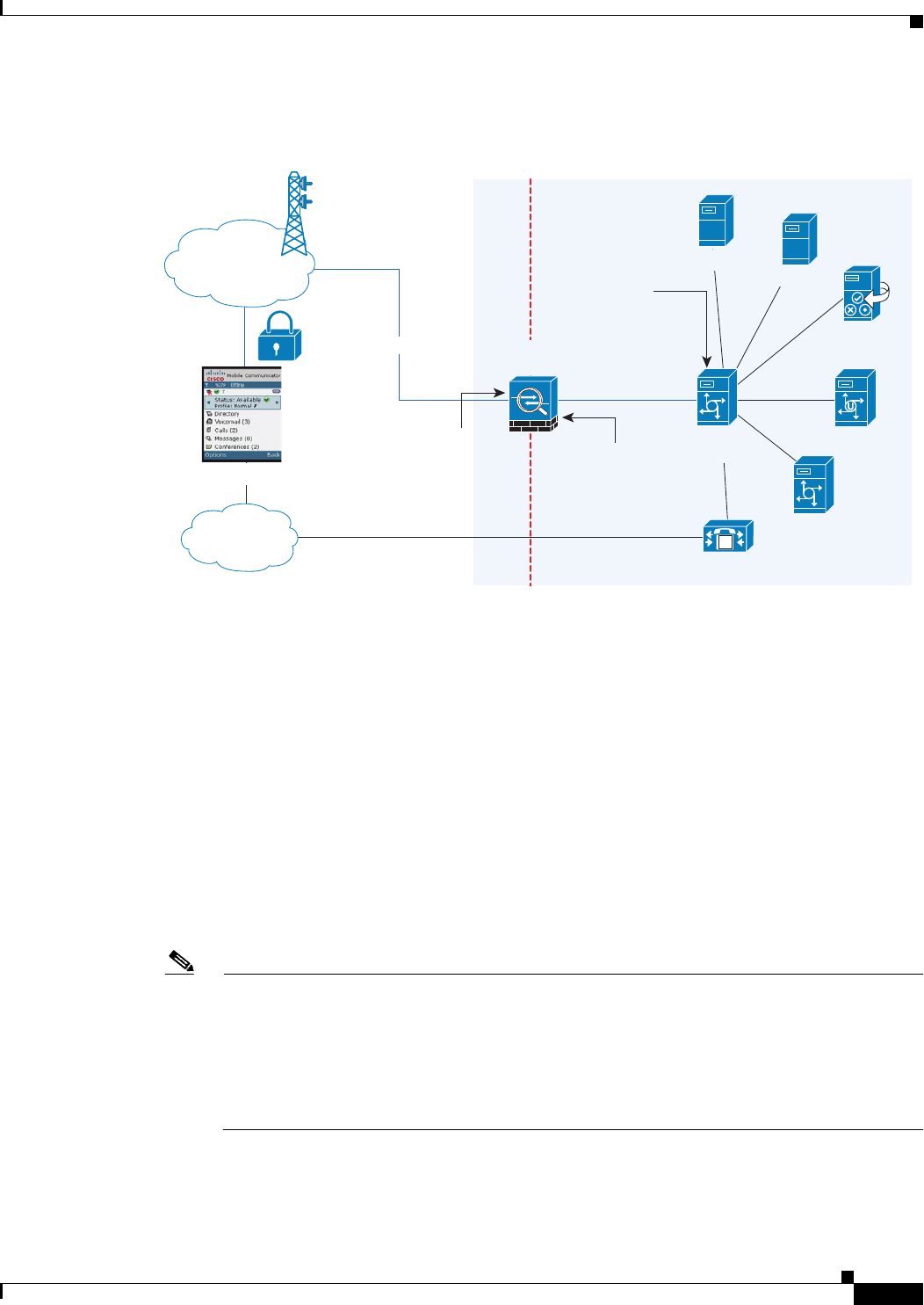
Figure 19-2 The TLS proxy for the Cisco Mobility Advantage solution does not support client
authentication because the Cisco UMA client cannot present a certificate.
Security
Appliance as Firewall with Mobility Advantage Proxy and MMP Inspection
In Figure 19-2, the ASA performs static NAT by translating the Cisco UMA server 10.1.1.2 IP address
to 192.0.2.140.
Figure 19-3 shows deployment scenario 2, where the ASA functions as the TLS proxy only and does not
function as the corporate firewall. In this scenario, the ASA and the corporate firewall are performing
NAT. The corporate firewall will not be able to predict which client from the Internet needs to connect
to the corporate Cisco UMA server. Therefore, to support this deployment, you can take the following
actions:
• Set up a NAT rule for inbound traffic that translates the destination IP address 192.0.2.41 to
172.16.27.41.
• Set up an interface PAT rule for inbound traffic translating the source IP address of every packet so
that the corporate firewall does not need to open up a wildcard pinhole. The Cisco UMA server
receives packets with the source IP address 192.0.12.183.
See Chapter 4, “Configuring Network Object NAT (ASA 8.3 and Later)” and Chapter 5,
“Configuring Twice NAT (ASA 8.3 and Later)” for information.
Note This interface PAT rule converges the Cisco UMA client IP addresses on the outside interface of
the ASA into a single IP address on the inside interface by using different source ports.
Performing this action is often referred as “outside PAT”. “Outside PAT” is not recommended
when TLS proxy for Cisco Mobility Advantage is enabled on the same interface of the ASA with
phone proxy, Cisco Unified Presence, or any other features involving application inspection.
“Outside PAT” is not supported completely by application inspection when embedded address
translation is needed.
271641
ASA with
TLS Proxy
Cisco UMA
Server
Mobile Data
Network (GPRS
Data Channel)
PSTN
MP
Conference
Voice mail
Cisco Unified
Presence
M
Cisco UCM
Exchange
Active Directory
Enterprise Services
Firewall
MMP/SSL/TLS
Voice Channel
MMP/SSL/TLS
Cisco UMC Client
Network:
10.1.1.0/24
IP Address:
10.1.1.2
Port: 5443
Network:
10.1.1.0/24
IP Address:
10.1.1.1
Hostname:
cuma.example.com
Network: 192.0.2.0/24
IP Address: 192.0.2.140
Port: 5443


















