3-32
Cisco ASA Series Firewall ASDM Configuration Guide
Chapter 3 Information About NAT (ASA 8.3 and Later)
DNS and NAT
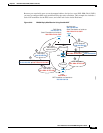
Figure 3-26 shows a DNS server that is accessible from the outside interface. A server, ftp.cisco.com, is
on the inside interface. You configure the ASA to statically translate the ftp.cisco.com real address
(10.1.3.14) to a mapped address (209.165.201.10) that is visible on the outside network. In this case, you
want to enable DNS reply modification on this static rule so that inside users who have access to
ftp.cisco.com using the real address receive the real address from the DNS server, and not the mapped
address. When an inside host sends a DNS request for the address of ftp.cisco.com, the DNS server
replies with the mapped address (209.165.201.10). The ASA refers to the static rule for the inside server
and translates the address inside the DNS reply to 10.1.3.14. If you do not enable DNS reply
modification, then the inside host attempts to send traffic to 209.165.201.10 instead of accessing
ftp.cisco.com directly.
Figure 3-26 DNS Reply Modification, DNS Server on Outside
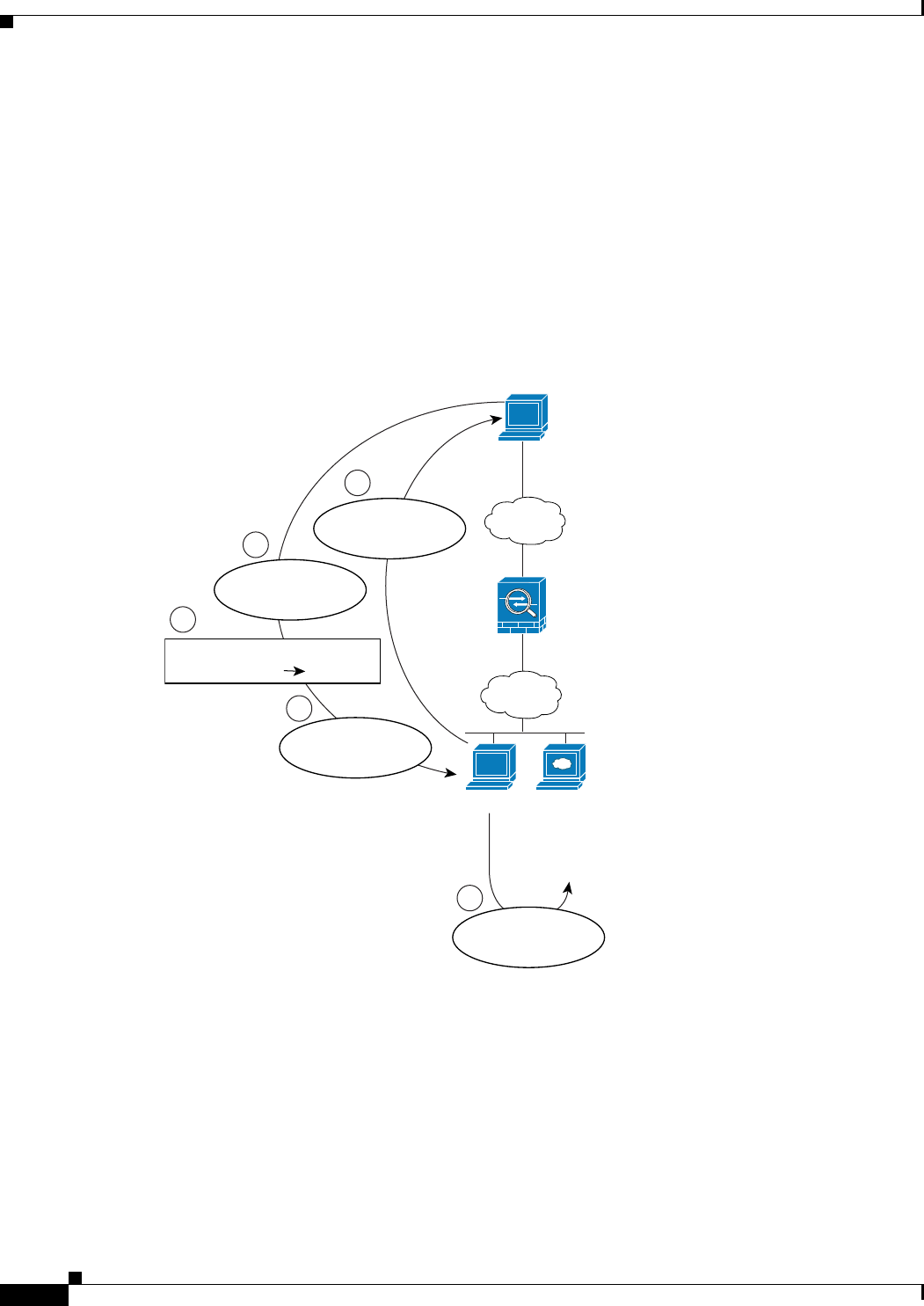
Figure 3-27 shows a user on the inside network requesting the IP address for ftp.cisco.com, which is on
the DMZ network, from an outside DNS server. The DNS server replies with the mapped address
(209.165.201.10) according to the static rule between outside and DMZ even though the user is not on
the DMZ network. The ASA translates the address inside the DNS reply to 10.1.3.14. If the user needs
to access ftp.cisco.com using the real address, then no further configuration is required. If there is also
DNS Server
Outside
Inside
User
130021
1
2
3
4
5
DNS Reply Modification
209.165.201.10 10.1.3.14
DNS Reply
209.165.201.10
DNS Reply
10.1.3.14
DNS Query
ftp.cisco.com?
FTP Request
10.1.3.14
Security
Appliance
ftp.cisco.com
10.1.3.14
Static Translation
on Outside to:
209.165.201.10