ProSecure Unified Threat Management (UTM) Appliance Reference Manual
Firewall Protection 5-45
v1.0, January 2010
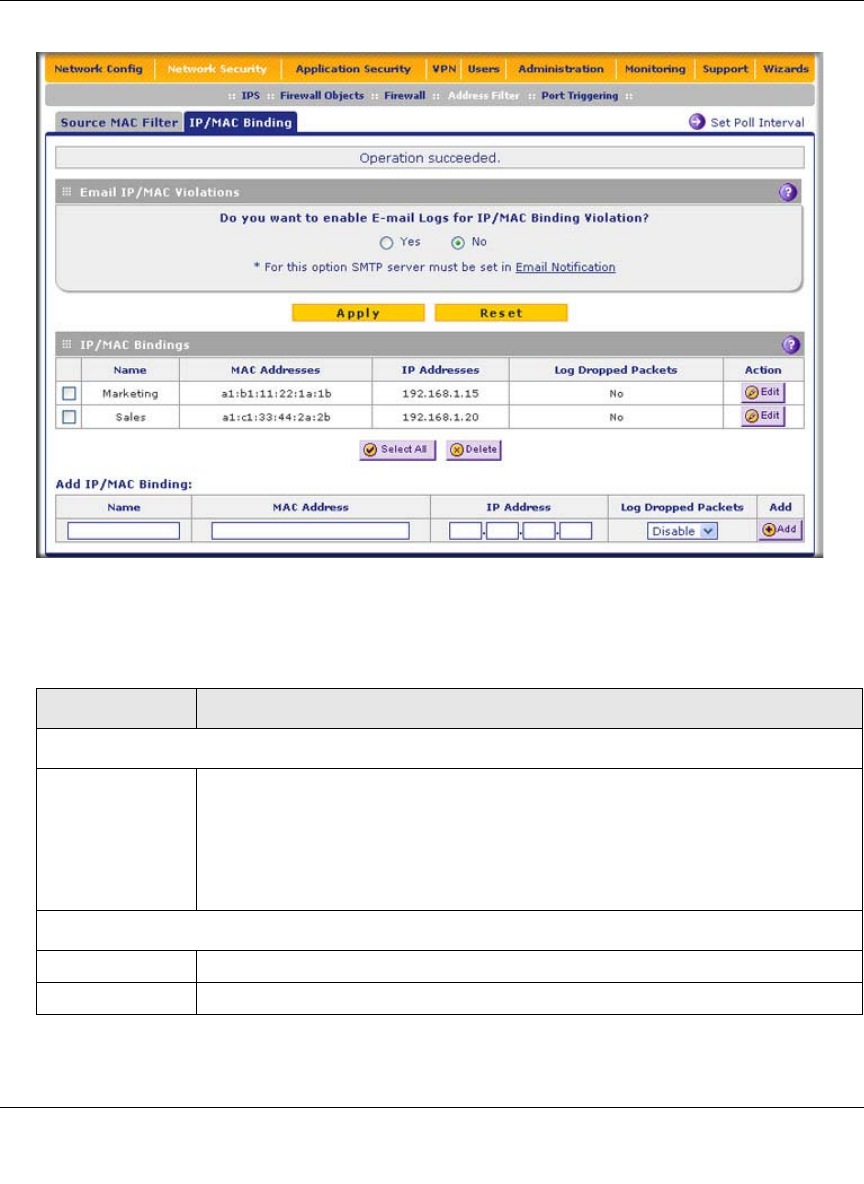
3. Enter the settings as explained in Table 5-9.
Figure 5-27
Table 5-9. IP/MAC Binding Settings
Setting Description (or Subfield and Description)
Email IP/MAC Violations
Do you want to
enable E-mail
Logs for IP/MAC
Binding Violation?
Select one of the following radio buttons:
• Yes. IP/MAC binding violations are e-mailed.
• No. IP/MAC binding violations are not e-mailed.
Note: Click the Firewall Logs & E-mail page hyperlink to ensure that e-mailing of
logs is enabled on the Email and Syslog screen (see “Configuring Logging, Alerts,
and Event Notifications” on page 11-5).
IP/MAC Bindings
Name A descriptive name of the binding for identification and management purposes.
MAC Address The MAC address of the PC or device that is bound to the IP address.


















