ProSecure Unified Threat Management (UTM) Appliance Reference Manual
11-34 Monitoring System Access and Performance
v1.0, January 2010
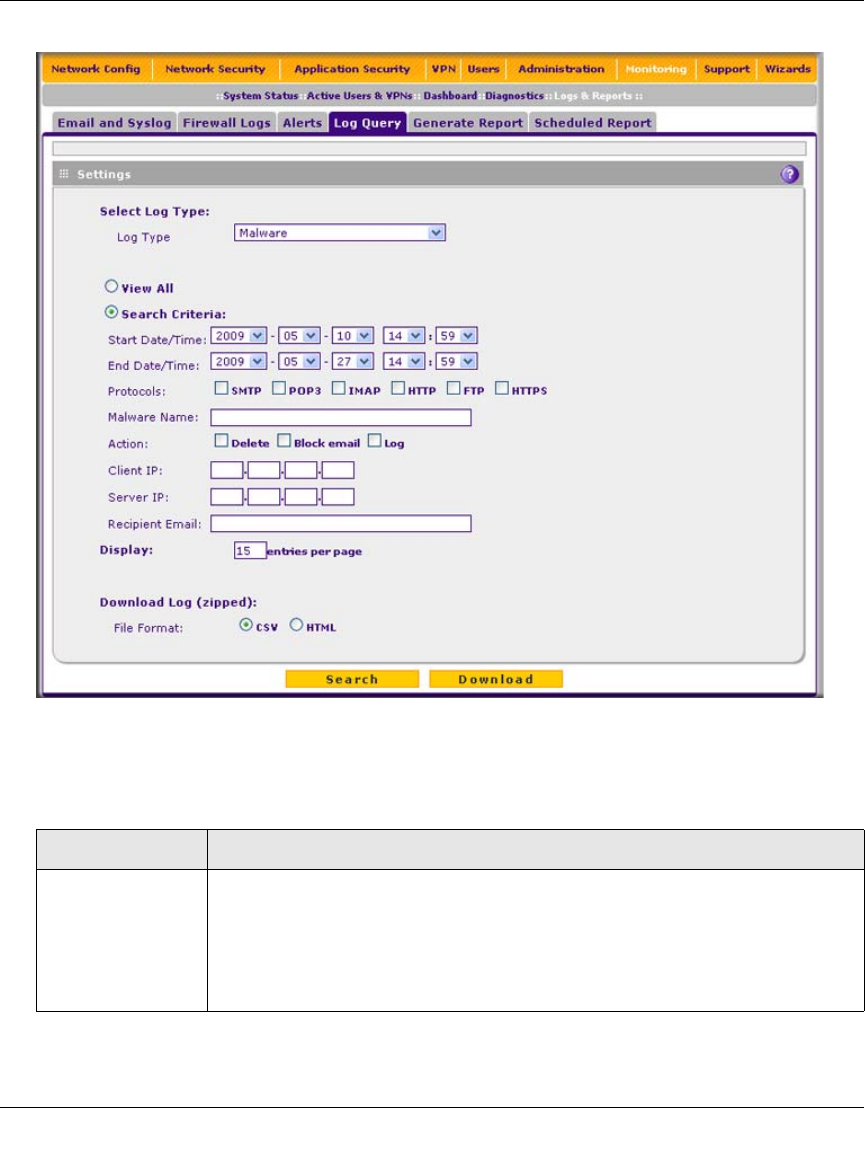
3. Enter the settings as explained in Table 11-15.
Figure 11-23
Table 11-15. Logs Query Settings
Setting Description (or Subfield and Description)
Log Type Select one of the following log types from the pull-down menu:
• Traffic. All scanned incoming and outgoing traffic.
• Spam. All intercepted spam.
• System. The system event logs that you have specified in the System Logs
Options section at the top of the screen. However, by default, many more types
of events are logged in the system logs.


















