WR3000 4-Port Wireless DSL/Cable Router
®
89
11.4.2 Types of DoS Attacks - Continued
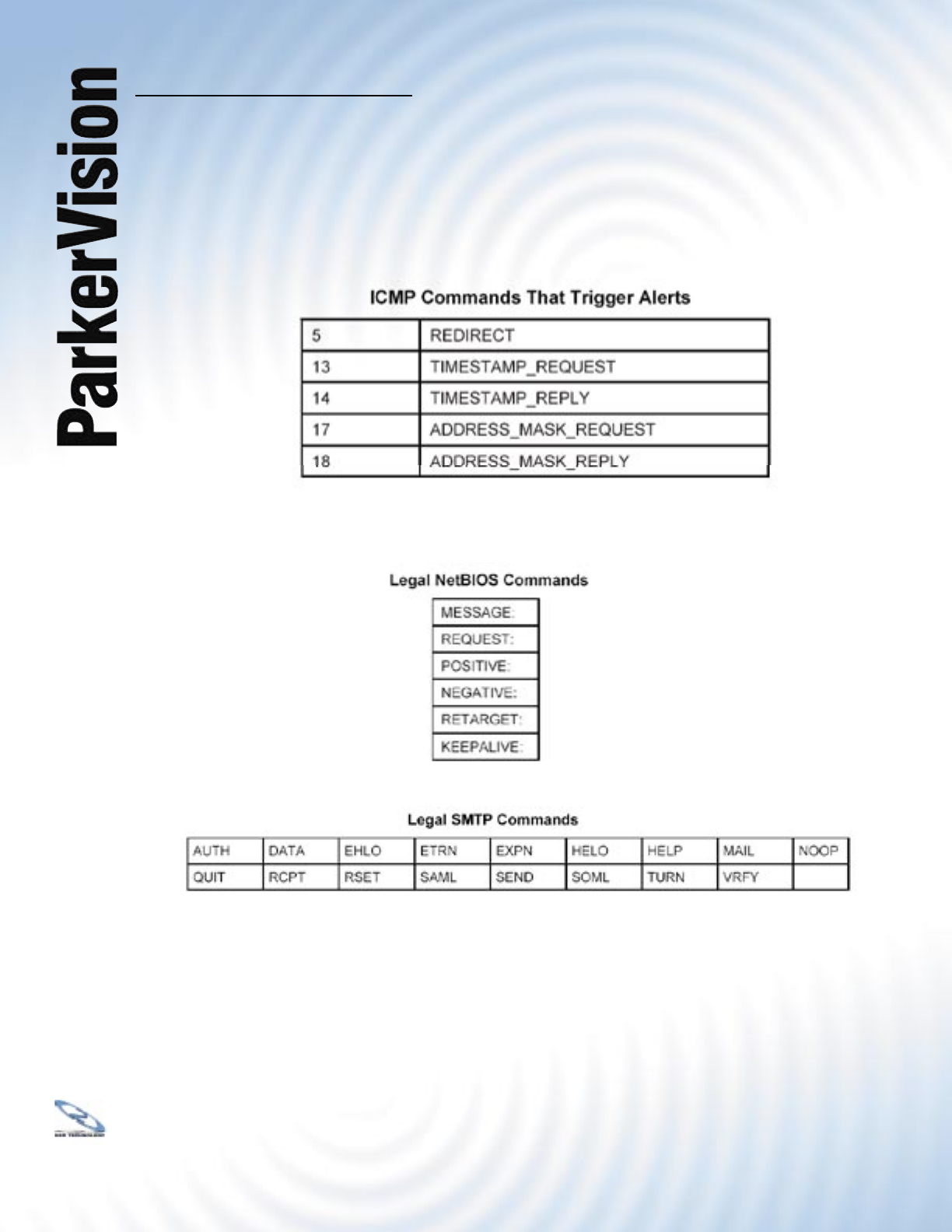
ICMP Vulnerability
ICMP is an error-reporting protocol that works in concert with IP. The following ICMP types
trigger an alert:
Illegal Commands (NetBIOS and SMTP)
The only legal NetBIOS commands are the following - all others are illegal.
All SMTP commands are illegal except for those displayed in the following table.
Traceroute
Traceroute is a utility used to determine the path a packet takes between two endpoints.
Sometimes when a packet fi lter fi rewall is confi gured incorrectly an attacker can traceroute the
fi rewall gaining knowledge of the network topology inside the fi rewall.
4. Often, many DoS attacks also employ a technique known as “IP Spoofi ng” as part of
their attack. IP Spoofi ng may be used to break into systems, to hide the hacker’s identity, or
to magnify the effect of the DoS attack. IP Spoofi ng is a technique used to gain unauthorized
access to computers by tricking a router or fi rewall into thinking that the communications are
coming from within the trusted network. To engage in IP spoofi ng, a hacker must modify the
packet headers so that it appears that the packets originate from a trusted host and should
be allowed through the router or fi rewall. The WR3000 Wireless Router blocks all IP Spoofi ng
attempts.


















