MAGNUM 6K SWITCHES, MNS-6K USER GUIDE
108
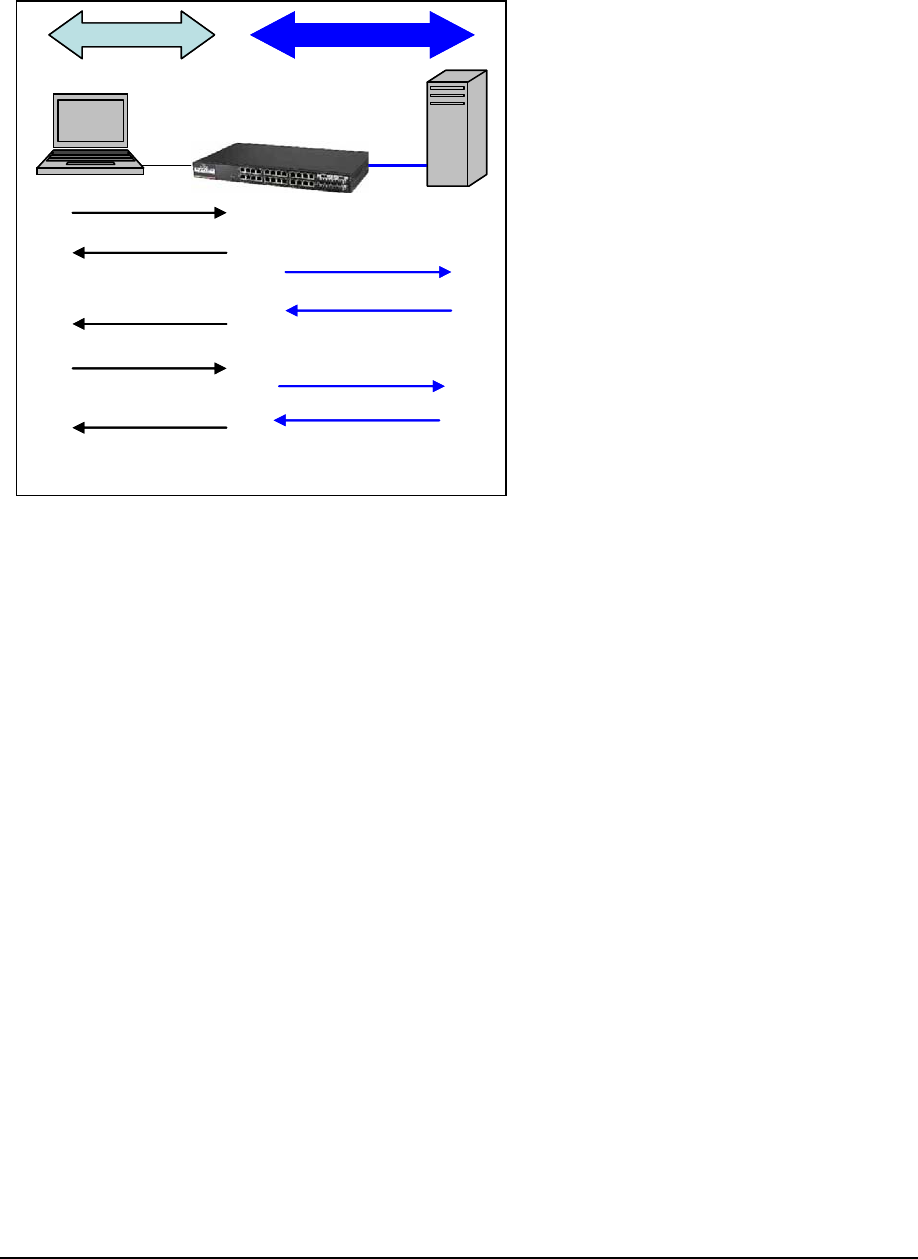
FIGURE 69 – 802.1x authentication details
1. The supplicant (laptop/host) is initially blocked from accessing the network. The
supplicant wanting to access these services starts with an EAPOL-Start frame
2. The authenticator (Magnum 6K switch), upon receiving an EAPOL-start frame, sends a
response with an EAP-Request/Identity frame back to the supplicant. This will inform
the supplicant to provide its identity
3. The supplicant then sends back its own identification using an EAP-Response/Identity
frame to the authenticator (Magnum 6K switch.) The authenticator then relays this to the
authentication server by encapsulating the EAP frame on a RADIUS-Access-Request
packet
4. The RADIUS server will then send the authenticator a RADIUS-Access-Challenge packet
5. The authenticator (Magnum 6K switch) will relay this challenge to the supplicant using an
EAP-Request frame. This will request the supplicant to pass its credentials for
authentication
6. The supplicant will send its credentials using an EAP-Response packet
7. The authenticator will relay using a RADIUS-Access-Request packet
8. If the supplicant’s credentials are valid, RADIUS-Access-Accept packet is sent to the
authenticator
9. The authenticator will then relay this on as an EAP-Success and provides access to the
network
10. If the supplicant does not have the necessary credentials, a RADIUS-Access-Deny packet
is sent back and relayed to the supplicant as an EAP-Failure frame. The access to the
network continues to be blocked
802.1x
Switch
EAPOL
EAP over RADIUS
X
Port Connected
Access Blocked
EAP Request Id
Y
Z
RADIUS Access Request
[
RADIUS Access Challenge
EAP Request
\
EAP Response
]
^
RADIUS Access Request
RADIUS Access Accept
EAP Success
`
_
Access Allowed
802.1x
Switch
EAPOL
EAP over RADIUS
X
Port Connected
Access Blocked
EAP Request Id
Y
Z
RADIUS Access Request
[
RADIUS Access Challenge
EAP Request
\
EAP Response
]
^
RADIUS Access Request
RADIUS Access Accept
EAP Success
`
_
Access Allowed


















