Network Access Rules Page 135
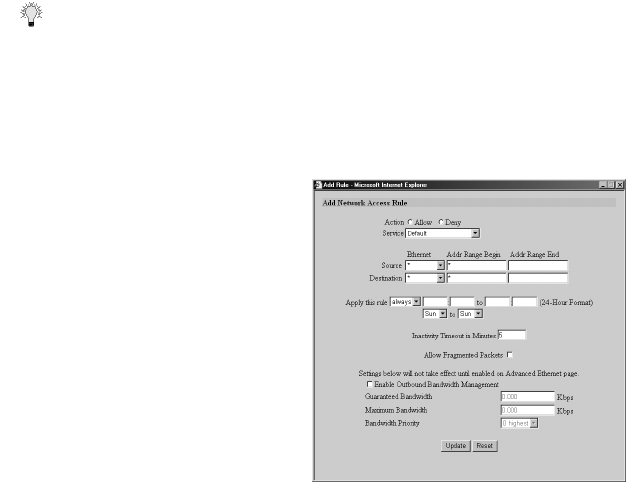
9. Do not select the Allow Fragmented Packets check box. Large IP packets are often divided into
fragments before they are routed over the Internet and then reassembled at a destination host.
Because hackers exploit IP fragmentation in Denial of Service attacks, the SonicWALL blocks
fragmented packets by default. You can override the default configuration to allow fragmented
packets over PPTP or IPSec.
10. Enable Bandwidth Management, and enter the Guaranteed Bandwidth in Kbps.
11. Enter the maximum amount of bandwidth available to the Rule at any time in the Maximum
Bandwidth field. Assign a priority from 0 (highest) to 7 (lowest).
12. Click Update. Once the SonicWALL has been updated, the new rule appears in the list of Current
Network Access Rules.
Tip Although custom rules can be created that allow inbound IP traffic, the SonicWALL does not
disable protection from Denial of Service attacks, such as the SYN Flood and Ping of Death attacks.
For example, to configure the SonicWALL to allow Internet traffic to your Web server with an IP
address of 208.5.5.5 (Standard mode), create the following rule:
1. Verify that HTTP has been added as a Service as outlined previously.
2. Click the Rules tab, and click Add New Rule....
3. Select Allow, then Web (HTTP) from the Service menu.
4. Select WAN from the Ethernet Source menu, and leave the Addr Range Begin and Addr Range
End as they appear.
5. Select LAN from the Ethernet Destination menu, and enter in the IP address of the Web server,
208.5.5.5 in the Addr Range Begin field. No IP address is added in the Addr Range End since
the destination is not a range of IP addresses.
6. Select always from the Apply this rule menu.
7. Enter a value (in minutes) in the Activity Timeout in Minutes field.
8. Do not select the Allow Fragmented Packets check box.
