SonicWALL VPN Page 213
Example of IKE Configuration for Two SonicWALLs
The following example illustrates the steps necessary to create an IKE VPN tunnel between a
SonicWALL PRO 200 and a SonicWALL TELE3.
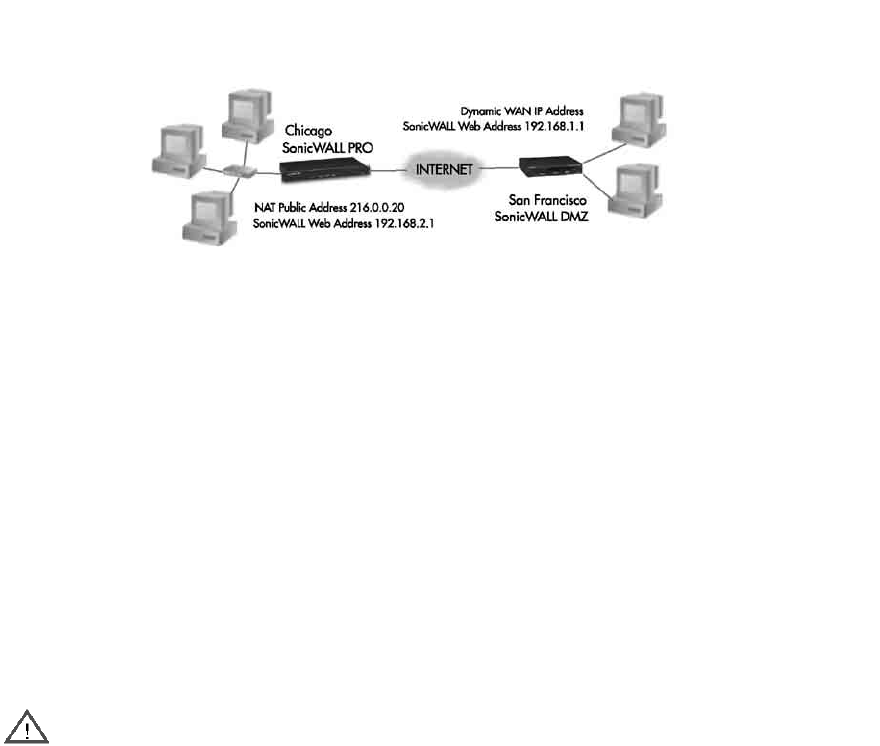
A company wants to use VPN to link two offices together, one in Chicago and the other in San
Francisco. To do this, the SonicWALL PRO 200 in Chicago and the SonicWALL TELE3 in San
Francisco must have corresponding Security Associations.
Configuring a SonicWALL PRO 200 in Chicago
1. Enter the SonicWALL PRO 200 Unique Firewall Identifier in the VPN Summary window. In this
example, it is "Chicago Office”.
2. Create a new Security Association by selecting -Add New SA- from the Security Association
menu in the VPN Configure window.
3. Select IKE using pre-shared secret from the IPSec Keying Mode menu.
4. Because the SonicWALL TELE3 does not have a permanent WAN IP address, the SonicWALL
PRO 200 must authenticate the VPN session by matching the Name of the SA with the TELE3
Unique Firewall Identifier. Enter the TELE3 Unique Firewall Identifier in the Name field, in this
example, "San Francisco Office."
5. Enter the WAN IP address of the remote SonicWALL in the IPSec Gateway Address field. In this
example, the San Francisco SonicWALL TELE3 has a dynamic IP address, therefore enter
"0.0.0.0" in the IPSec Gateway Address field
Alert Only one of the two IPSec gateways can have a dynamic IP address when using SonicWALL
VPN.
6. Select Main Mode from the Exchange menu.
7. Select Group 1 from the Phase 1 DH Group menu.
8. Enter "28800" in the SA Life time (secs) field to renegotiate IKE encryption and authentication
keys every 8 hours.
9. Select 3DES & SHA1 from the Phase 1 DH Group menu.
