54-4
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 54 Configuring Cisco Mobility Advantage
Information about the Cisco Mobility Advantage Proxy Feature
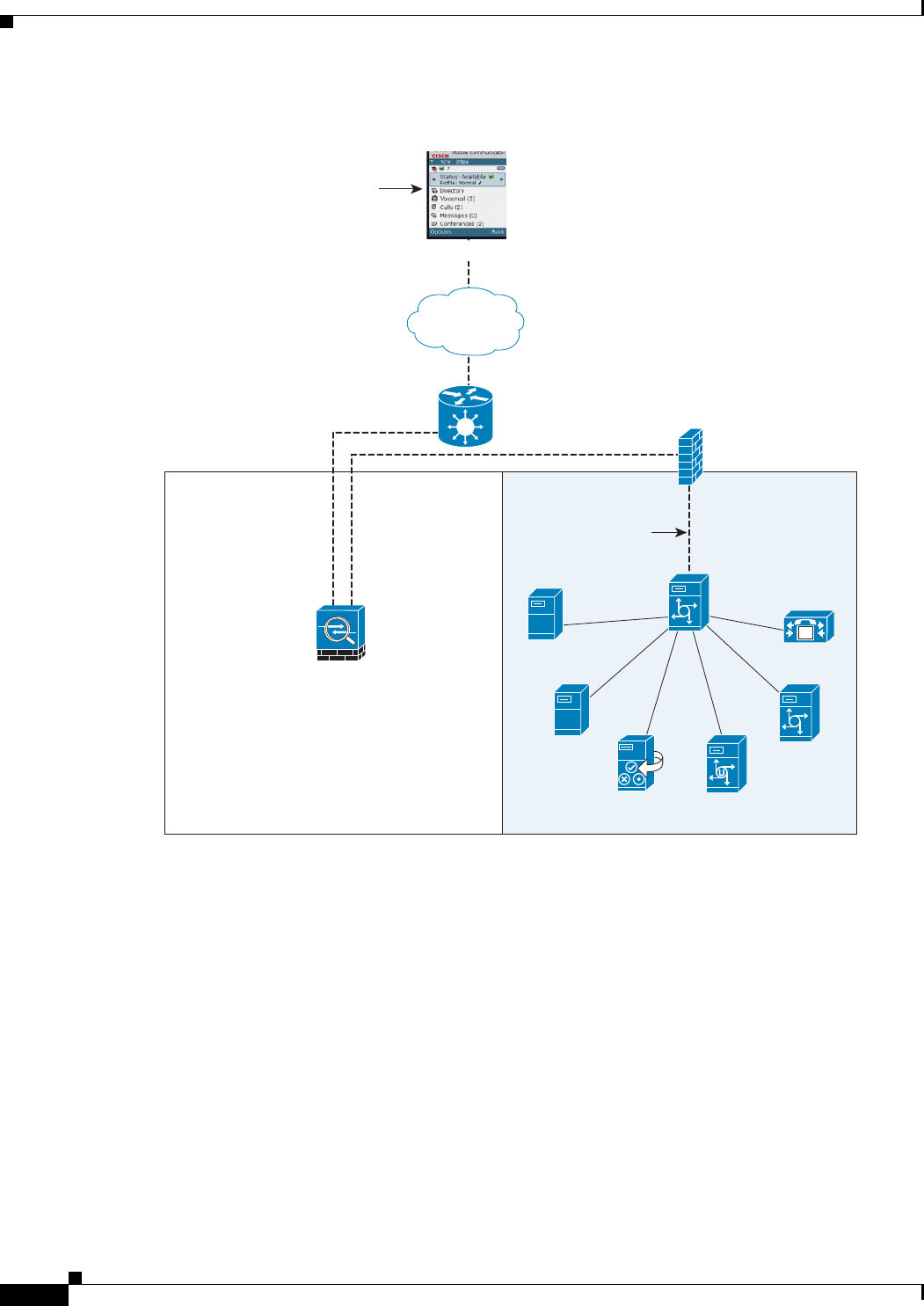
Figure 54-3 Cisco UMC/Cisco UMA Architecture – Scenario 2: Security Appliance as Mobility
Advantage Proxy Only
Mobility Advantage Proxy Using NAT/PAT
In both scenarios (Figure 54-2 and Figure 54-3), NAT can be used to hide the private address of the Cisco
UMA servers.
In scenario 2 (Figure 54-3), PAT can be used to converge all client traffic into one source IP, so that the
firewall does not have to open up a wildcard pinhole for inbound traffic.
Trust Relationships for Cisco UMA Deployments
To establish a trust relationship between the Cisco UMC client and the ASA, the ASA uses the Cisco
UMA server certificate and keypair or the ASA obtains a certificate with the Cisco UMA server FQDN
(certificate impersonation). Between the ASA and the Cisco UMA server, the ASA and Cisco UMA
server use self-signed certificates or certificates issued by a local certificate authority.
271642
ASA with
TLS Proxy
IP Address:
172.16.27.41
(DMZ routable)
DMZ
MP
Conference
Voice mail
Cisco Unified
Presence
M
Cisco UCM
Exchange
Active
Directory
Internal Network
Corporate
Firewall
Enterprise Network
eth0
Internet
Cisco UMC Client
Cisco UMA
Client connects to
cuma.example.com
(192.0.2.41)
insideoutside
192.0.2.41/24 192.0.2.182/24
ISP
Gateway


















