35-18
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 35 Configuring NAT (ASA 8.2 and Earlier)
Using Dynamic NAT
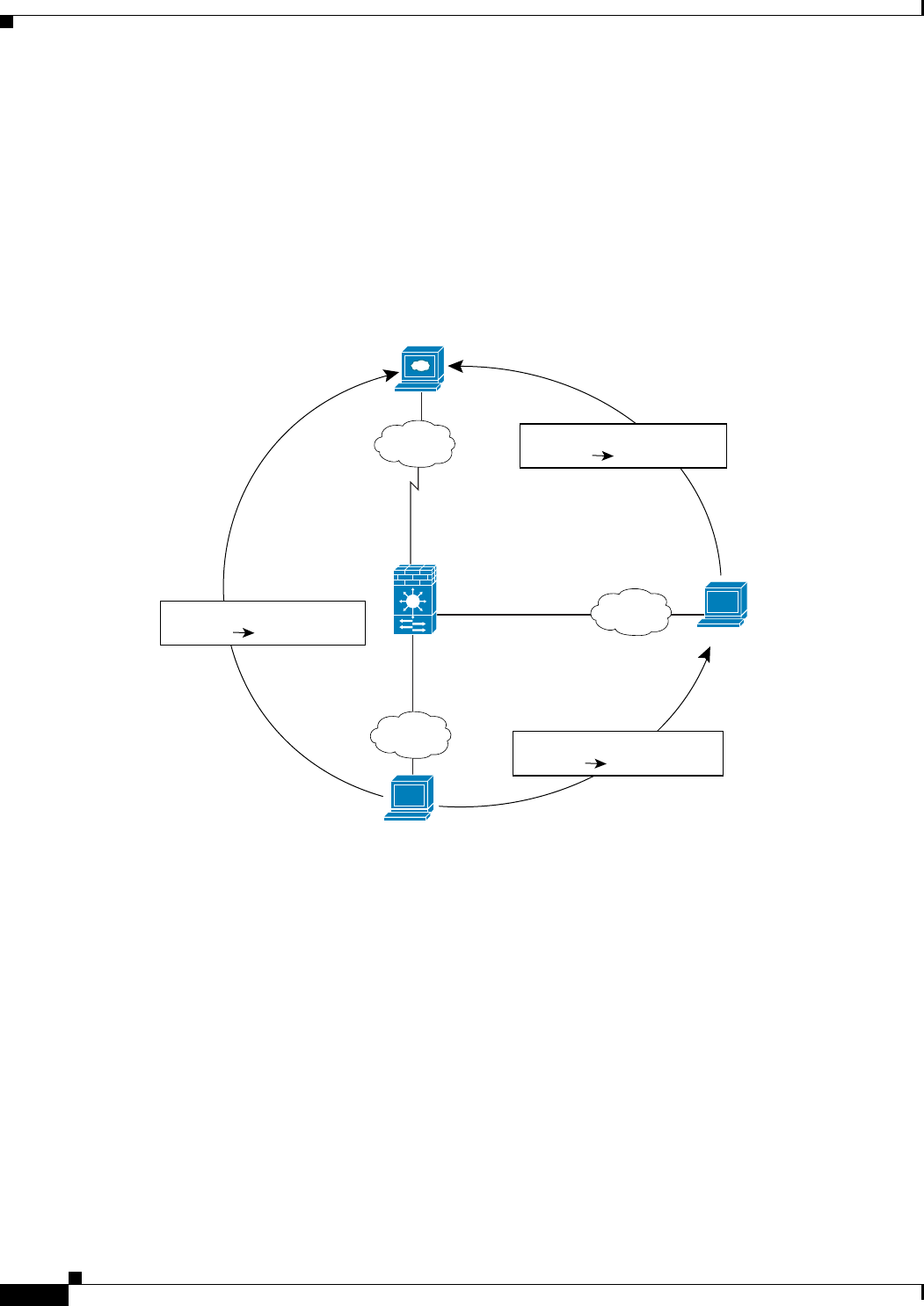
Global Pools on Different Interfaces with the Same Pool ID
You can create a global pool for each interface using the same pool ID. If you create a global pool for
the Outside and DMZ interfaces on ID 1, then a single NAT rule associated with ID 1 identifies traffic
to be translated when going to both the Outside and the DMZ interfaces. Similarly, if you create a NAT
rule for the DMZ interface on ID 1, then all global pools on ID 1 are also used for DMZ traffic. (See
Figure 35-15).
Figure 35-15 NAT Rules and Global Pools using the Same ID on Multiple Interfaces
Multiple NAT Rules with Different Global Pools on the Same Interface
You can identify different sets of real addresses to have different mapped addresses. For example, on the
Inside interface, you can have two NAT rules on two different pool IDs. On the Outside interface, you
configure two global pools for these two IDs. Then, when traffic from Inside network A exits the Outside
interface, the IP addresses are translated to pool 1 addresses; while traffic from Inside network B are
translated to pool 2 addresses (see Figure 35-16). If you use policy NAT, you can specify the same real
addresses for multiple NAT rules, as long as the destination addresses and ports are unique in each access
list.
Web Server:
www.cisco.com
Outside
DMZ
Inside
Global 1: 209.165.201.3-
209.165.201.10
NAT 1: 10.1.2.0/24
NAT 1: 10.1.1.0/24
Global 1: 10.1.1.23
10.1.1.15
10.1.2.27
132926
Translation
209.165.201.310.1.2.27
Translation
209.165.201.410.1.1.15
Translation
10.1.1.23:202410.1.2.27


















