68-6
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 68 Configuring IKE, Load Balancing, and NAC
Creating IKE Policies
–
Hash—Shows the hash algorithm.
–
D-H Group—Shows the Diffie-Hellman group.
–
Authentication—Shows the authentication method.
–
Lifetime (secs)—Shows the SA lifetime in seconds.
• Add/Edit/Delete—Click to add, edit, or delete an IKEv1 policy.
• IKEv2 Policies—Displays parameter settings for each configured IKEv2 policy.
–
Priority #—Shows the priority of the policy.
–
Encryption—Shows the encryption method.
–
Integrity Hash—Shows the hash algorithm.
–
PRF Hash—Shows the pseudo random function (PRF) hash algorithm.
–
D-H Group—Shows the Diffie-Hellman group.
–
Lifetime (secs)—Shows the SA lifetime in seconds.
• Add/Edit/Delete—Click to add, edit, or delete an IKEv2 policy.
Modes
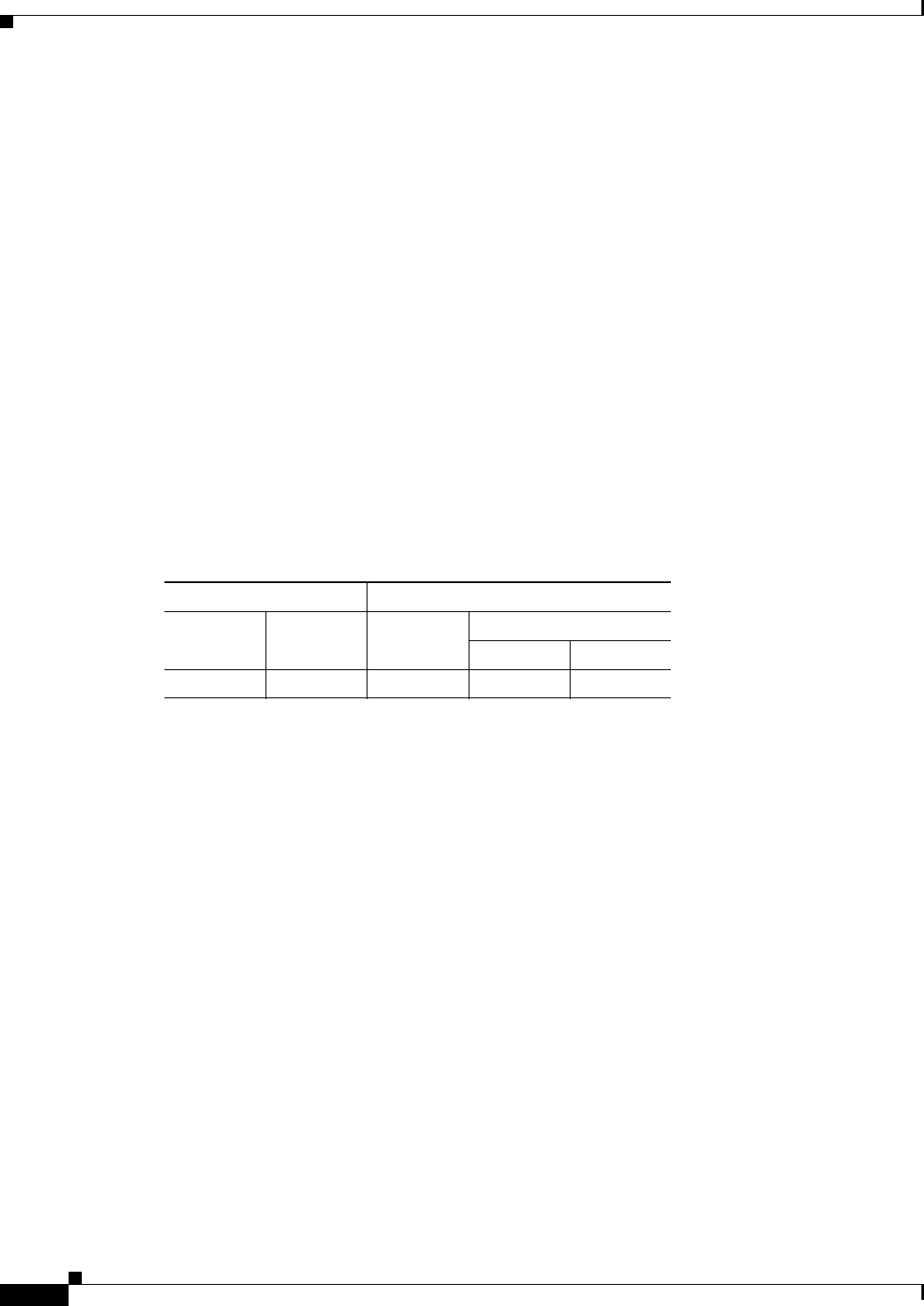
The following table shows the modes in which this feature is available:
Add/Edit IKEv1 Policy
Fields
Priority #—Type a number to set a priority for the IKE policy. The range is 1 to 65535 , with 1 the
highest priority.
Encryption—Choose an encryption method. This is a symmetric encryption method that protects data
transmitted between two IPsec peers.The choices follow:
Firewall Mode Security Context
Routed Transparent Single
Multiple
Context System
• — • ——
des 56-bit DES-CBC. Less secure but faster than the alternatives. The default.
3des 168-bit Triple DES.
aes 128-bit AES.
aes-192 192-bit AES.
aes-256 256-bit AES.


















