B-20
Cisco ASA 5500 Series Configuration Guide using ASDM
Appendix B Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
[29] Retrieved Attributes:
[29] department: value = Group-Policy-1
[29] mapped to IETF-Radius-Class: value = Group-Policy-1
Enforcing Static IP Address Assignment for AnyConnect Tunnels
In this example, configure the AnyConnect client user Web1 to receive a static IP address. then enter the
address in the Assign Static IP Address field of the Dialin tab on the AD LDAP server. This field uses
the msRADIUSFramedIPAddress attribute. Create an attribute map that maps this attribute to the Cisco
attribute IETF-Radius-Framed-IP-Address.
During authentication, the ASA retrieves the value of msRADIUSFramedIPAddress from the server,
maps the value to the Cisco attribute IETF-Radius-Framed-IP-Address, and provides the static address
to User1.
The following example applies to full-tunnel clients, including the IPsec client and the SSL VPN clients
(AnyConnect client 2.x and the SSL VPN client).
To configure the user attributes on the AD/LDAP server, perform the following steps:
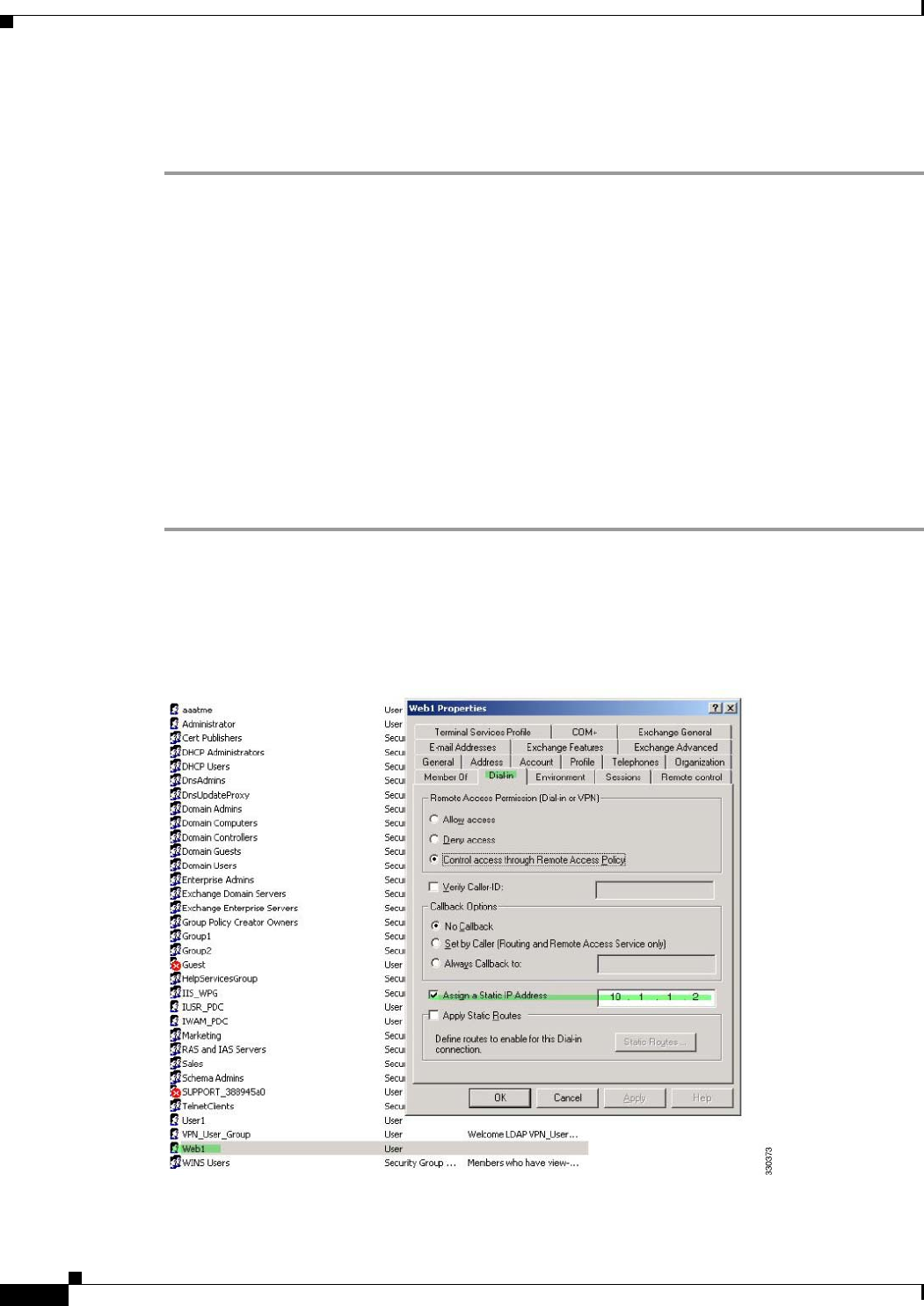
Step 1 Right-click the username.
The Properties dialog box appears (see Figure B-6).
Step 2 Click the Dialin tab, check the Assign Static IP Address check box, and enter an IP address of 10.1.1.2.
Figure B-6 Assign Static IP Address
Step 3
Create an attribute map for the LDAP configuration shown in Step 1.