R0E530640MCU00 User’s Manual 5. Debugging Functions
REJ10J1733-0100 Rev.1.00 Apr. 01, 2008
Page 197 of 229
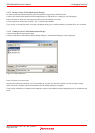
(3) Methods for setting protection
There are following two methods of specification:
- Automatic setting by section information in a download module
- Specifying the access attribute of any area individually
(4) Detection method
An access protect violation is detected by the emulator’s internal resources (blocks 1–16).
The blocks are automatically allocated by the emulator’s exclusive algorithm.
CAUTION
Since the emulator’s internal resources are limited, not all blocks can be access protected. In that case, reduce the amount of
used blocks by “removing blocks” before setting protection again.
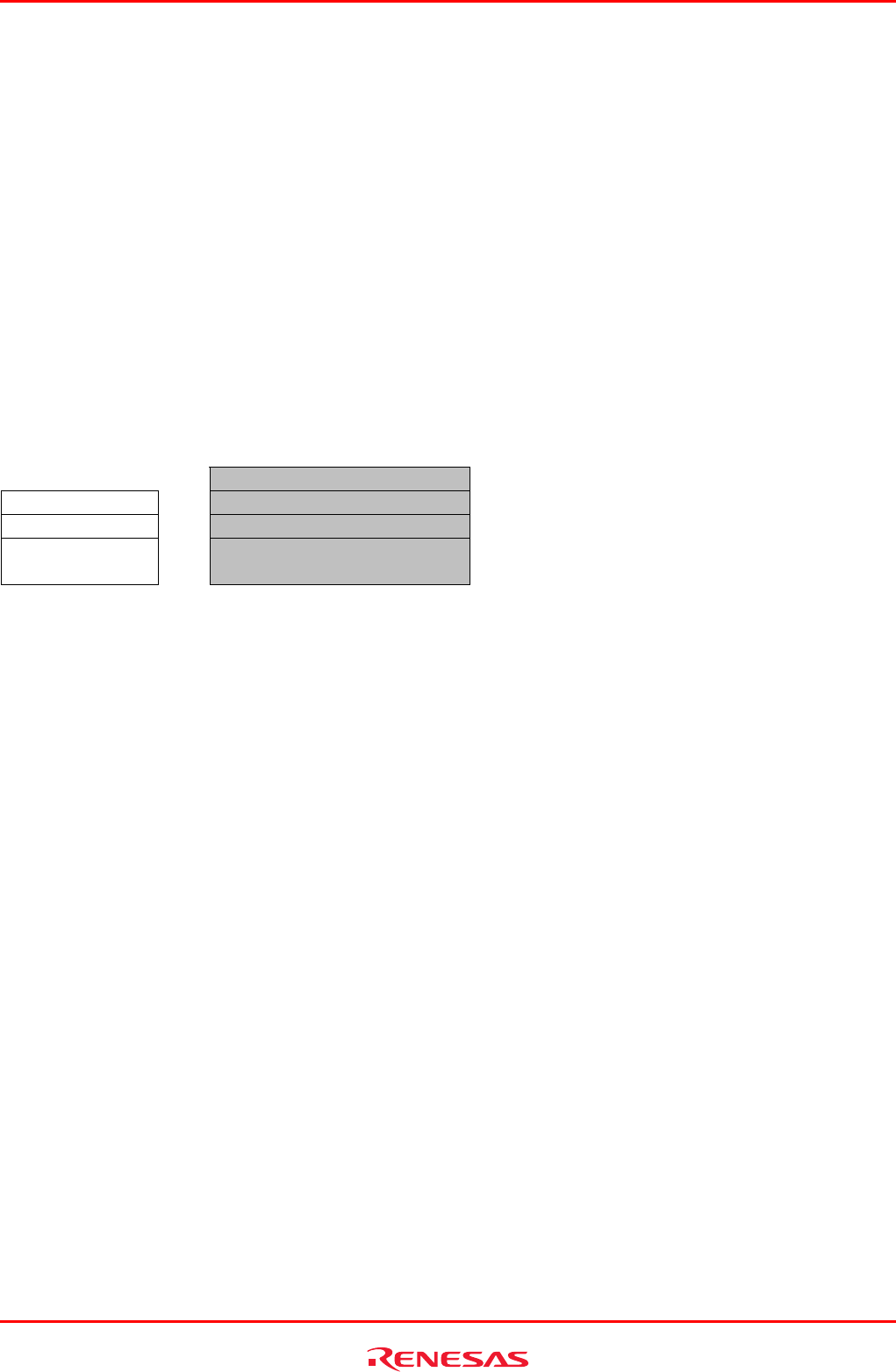
Access attribute
Read/Write
Write access -> Read Only -> Detected
Read access -> Write Only -> Detected
Read access -> Disable -> Detected
Write access
Figure 5.137 NG patterns of detection methods
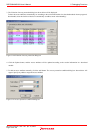
(5) Actions taken when an access protect violation is detected
The following actions can be set:
- Display a warning
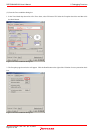
Selecting the Access Protect Violation check box on the Exception Warning page of the Configuration properties dialog box,
you can display a warning in the Status window and in a status bar balloon.
- Make the detection of an access protect violation a condition of a hardware breakpoint
- Make the detection of an access protect violation a condition of a trace point