Chapter 7: User Management
123
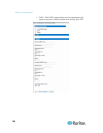
Authentication Settings
Authentication is the process of verifying that a user is who he says he
is. Once a user is authenticated, the user's group is used to determine
his system and port permissions. The user's assigned privileges
determine what type of access is allowed. This is called authorization.
When the KSX II is configured for remote authentication, the external
authentication server is used primarily for the purposes of authentication,
not authorization.
From the Authentication Settings page you can configure the type of
authentication used for access to your KSX II.
Note: When remote authentication (LDAP/LDAPS or RADIUS) is
selected, if the user is not found, the local authentication database will
also be checked.
To configure authentication:
1. Choose User Management > Authentication Settings. The
Authentication Settings page opens.
2. Choose the option for the authentication protocol you want to use
(Local Authentication, LDAP/LDAPS, or RADIUS). Choosing the
LDAP option enables the remaining LDAP fields; selecting the
RADIUS option enables the remaining RADIUS fields.
3. If you choose Local Authentication, proceed to step 6.
4. If you choose LDAP/LDAPS, read the section entitled Implementing
LDAP Remote Authentication (see "Implementing LDAP/LDAPS
Remote Authentication" on page 124) for information about
completing the fields in the LDAP section of the Authentication
Settings page.
5. If you choose RADIUS, read the section entitled Implementing
RADIUS Remote Authentication (on page 128) for information
about completing the fields in the RADIUS section of the
Authentication Settings page.
6. Click OK to save.
To return to factory defaults:
Click the Reset to Defaults button.