189
In This Chapter
Security Settings .................................................................................... 189
Configuring IP Access Control .............................................................. 199
SSL Certificates ..................................................................................... 201
Security Banner ..................................................................................... 203
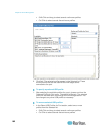
Security Settings
From the Security Settings page, you can specify login limitations, user
blocking, password rules, and encryption and share settings.
Raritan SSL certificates are used for public and private key exchanges,
and provide an additional level of security. Raritan web server certificates
are self-signed. Java applet certificates are signed by a VeriSign
certificate. Encryption guarantees that your information is safe from
eavesdropping and these certificates ensure that you can trust that the
entity is Raritan, Inc.
To configure the security settings:
1. Choose Security > Security Settings. The Security Settings page
opens.
2. Update the Login Limitations (on page 190) settings as
appropriate.
3. Update the Strong Passwords (on page 192) settings as
appropriate.
4. Update the User Blocking (on page 193) settings as appropriate.
5. Update the Encryption & Share settings as appropriate.
6. Click OK.
Chapter 9
Security Management