50 COMMANDCENTER NOC ADMINISTRATOR GUIDE
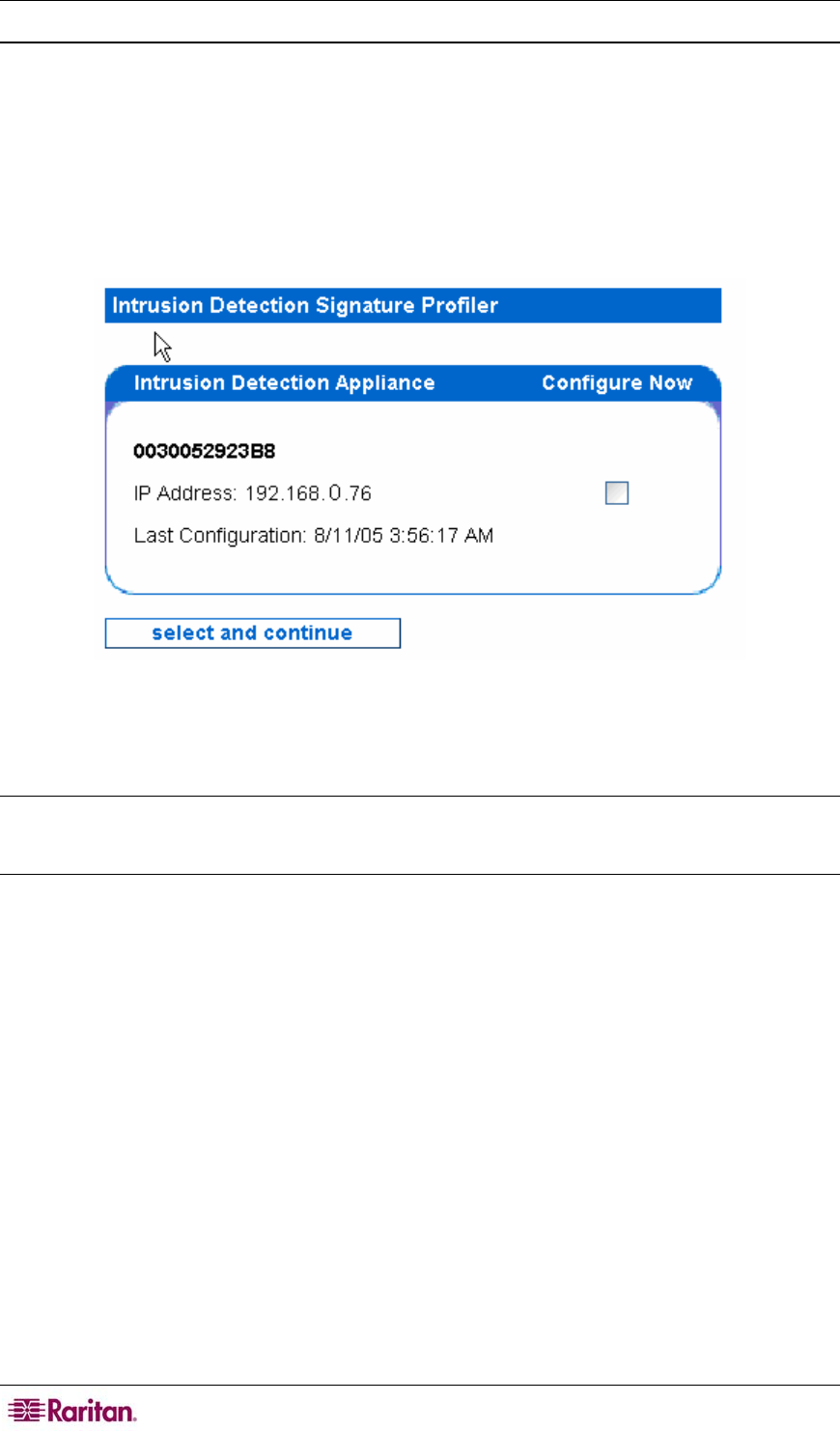
Select Intrusion Detection Appliance(s)
All of the Intrusion Detection appliances that can communicate with the system hosting this Web
Console are listed in the Intrusion Detection Appliance box. The Last Configuration field
indicates the last time that the detection scheme for the Intrusion Detection was changed or the
last time that a security patch was used to update the signatures on the Intrusion Detection.
Enabling automatic updates provides up-to-date signatures – see
System Software & Signature
Updates in
Chapter 2: General and Advanced Administration for additional information.
If an Intrusion Detection appliance is listed as Not Configured, you must use the Signature
Profiler to configure its signatures so that it can begin relaying events.
Figure 63 Selecting Intrusion Detection Appliances for Signature Profiler
4. To configure one or more Intrusion Detection appliances with identical configurations, check
the boxes under the Configure Now heading.
Note: The CC-NOC 100 and CC-NOC 250 only supports a single network segment connected to
the traffic sniffing port. To monitor additional network segments, configuring a CC-NOC 2500N
with multiple CC-NOC 2500S appliances is necessary.
5. Click Select and continue when you have made your selection.
6. Choose the appliance that you wish to configure by clicking Configure next to it.
