CHAPTER 5: CONFIGURING VULNERABILITY SCANNING 71
Scan Level 4
Scan Level 4 performs all checks of previous levels and also attempts exploits that are known to
be directly harmful to target systems. These include vulnerabilities that can alter data on the target
or bring down services or the operating system by using denial-of-service techniques. It is
absolutely
not advisable to use this scan against mission-critical targets, regardless of OS or
services that are running.
At each Scan Level, there is the potential for damage including data loss, network communication
loss, hardware damage, loss of network integrity, or exposure of information to unauthorized
parties.
Warning: Vulnerability scanning at any level has the potential to be harmful to target machines.
Scan Levels 3 and 4 carry out real intrusion attempts against targets and can have negative effects
on the target machines to the point of data loss and denial of services. Use these scan levels with
extreme caution. You may want to schedule these scans to run off-hours.
Specify IP Addresses and Schedule the Scan
After agreeing to the Warning, you now need to identify the targets of the scan. Only the admin
user can configure vulnerability scanning.
To build a scan:
1. After clicking I Agree to the warning, click edit settings at the bottom of the page.
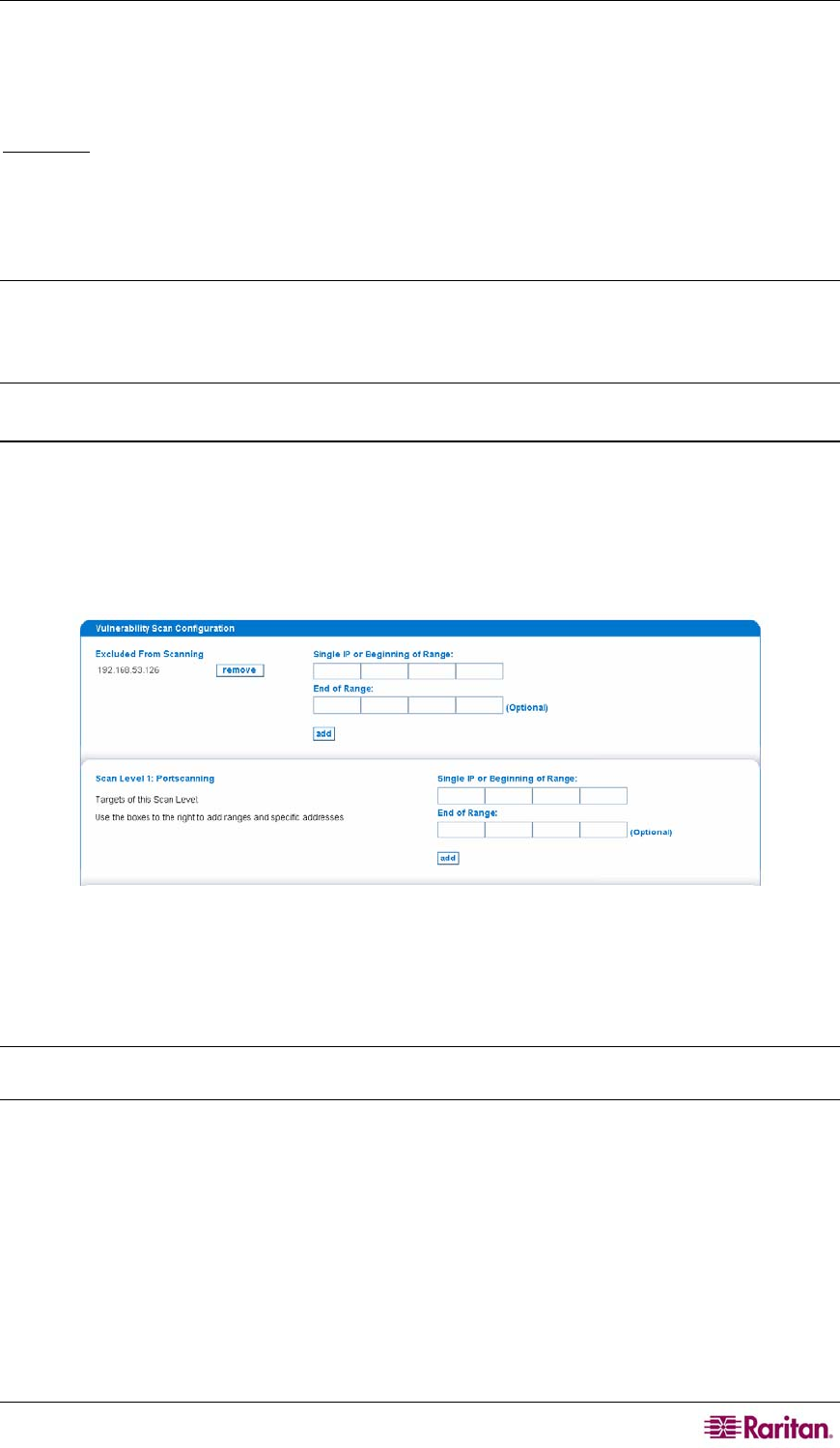
Figure 86 Type IP Addresses for Vulnerability Scanning
2. Add the appropriate IP addresses to the levels you want to scan. You can add either specific
IP addresses, by filling in the Single IP or Beginning of Range field, or a range of IP
addresses, by filling in the End of Range field.
Note: The Excluded from Scanning box lets you exclude IP addresses from any type of scanning.
The IP ranges specified in this box override all other scanning settings.
