72 COMMANDCENTER NOC ADMINISTRATOR GUIDE
3. Click add to have the targets added, or excluded, from the scan.
4. Click save settings to save all addresses entered and return to the previous page.
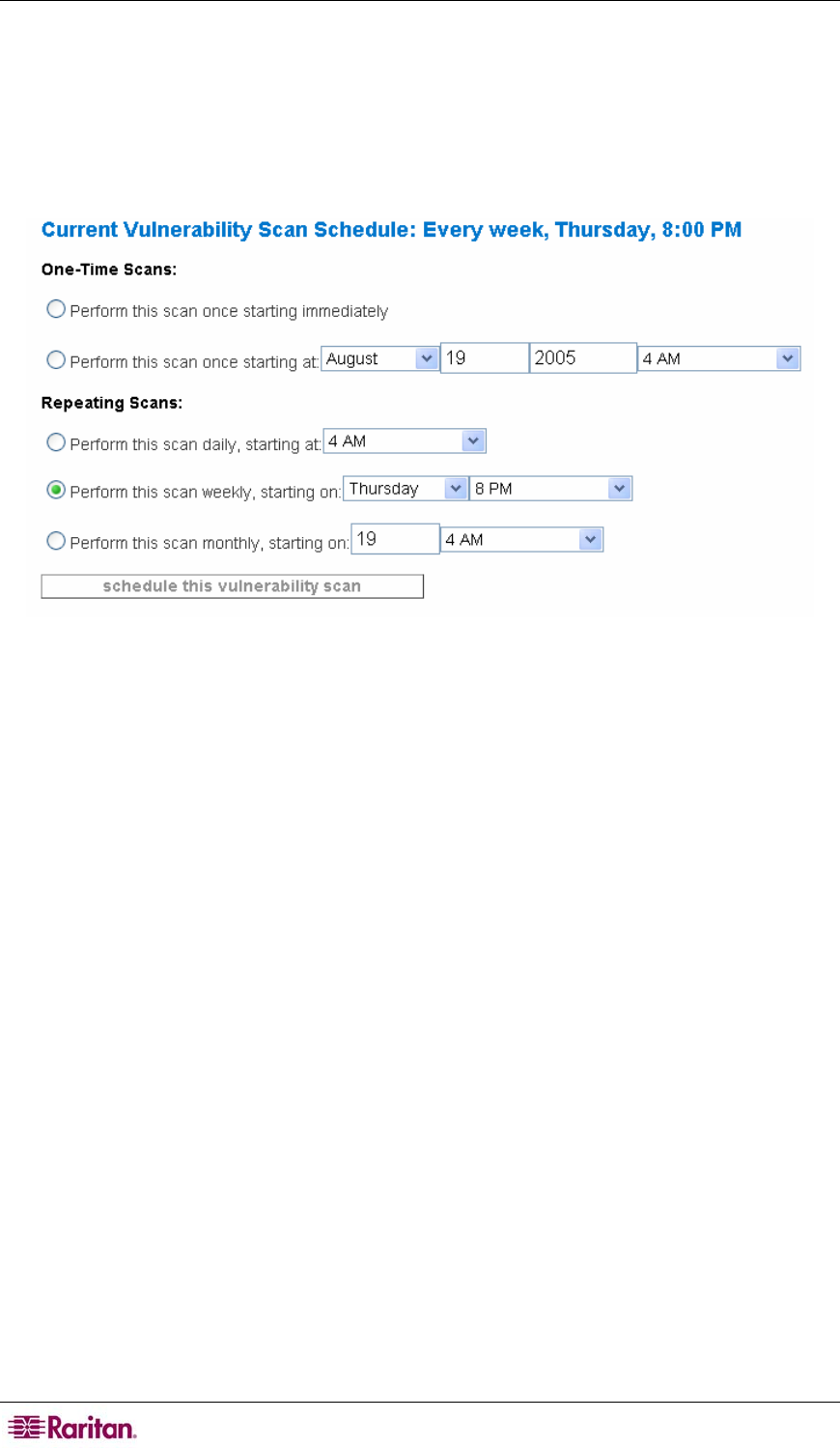
5. Scroll to the bottom of the page and create a scanning schedule. Vulnerability scanning can
be scheduled to occur when it won't adversely impact your network. This will allow you to
perform the more intensive vulnerability scanning without impacting your network
availability. Recurring scans can also be configured, allowing you to maintain your network
security.
Figure 87 Create a Vulnerability Scanning Schedule
6. Select one of the options to perform a one-time scan of the devices that were specified or set
up a scan that repeats according to the frequency you specify.
7. Click schedule this vulnerability scan.


















