RuggedRouter® User Guide
This menu allows you to add, delete and configure network interfaces. Add a new
interface by selecting the “Add a new network interface” link or by clicking on the
add-above or add-below images in the Add field. Reorder the interfaces by clicking
on the arrows under the Move field.
Clicking on a link under the Interface field will allow you to edit or delete the
interface. Note that if you delete an interface you should remove any rules that
reference it.
You may also make changes by manually editing the interfaces file.
Note: If you use a WAN interface in the firewall, the interface will be referred to by its
name. Some WAN changes (such as changing the number of channels used by a T1/E1
logical interface) will change the name. Ensure that the entries in this menu reflect the
correct interface names.
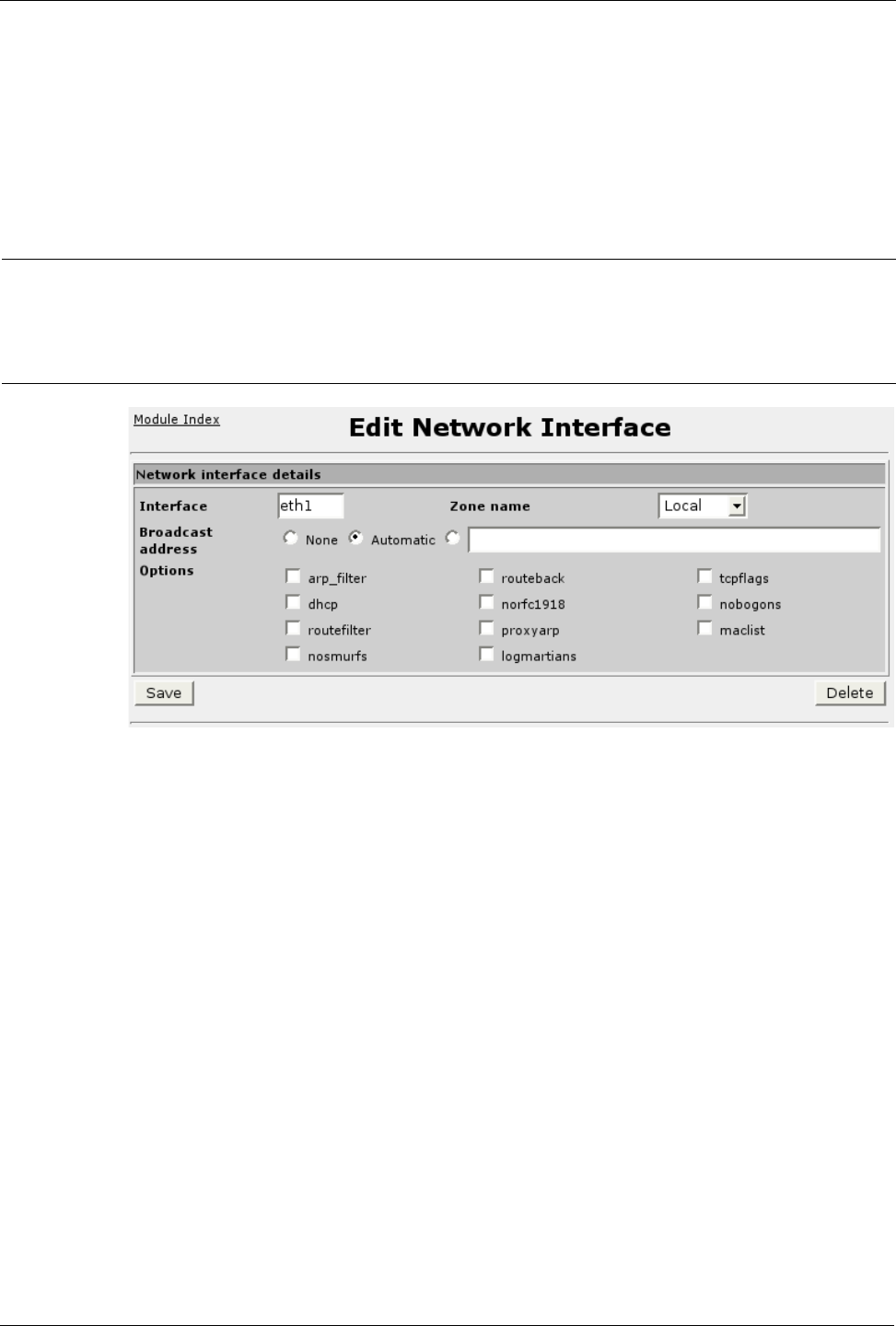
Figure 102: Editing a Firewall Network Interfaces
The dhcp option should be selected if interface is assigned an IP address via DHCP or
is used by a DHCP server running on the firewall. The firewall will be configured to
allow DHCP traffic to and from the interface even when the firewall is stopped. You
may also wish to use this option if you have a static IP but you are on a LAN segment
that has a lot of laptops that use DHCP and you select the norfc1918 option (see
below).
The arp_filter option causes this interface to only answer ARP “who-has” requests
from hosts that are routed out of that interface. Setting this option facilitates testing of
your firewall where multiple firewall interfaces are connected to the same
HUB/Switch (all interfaces connected to the single HUB/Switch should have this
option specified). Note that using such a configuration is strongly recommended
against.
The routeback option causes Shorewall to set up handling for routing packets that
arrive on this interface back out the same interface.
The tcpflags option causes Shorewall to make sanity checks on the header flags in
TCP packets arriving on this interface. Checks include Null flags, SYN+FIN,
SYN+RST and FIN+URG+PSH; these flag combinations are typically used for
“silent” port scans. Packets failing these checks are logged according to the
TCP_FLAGS_LOG_LEVEL option in /etc/shorewall/shorewall.conf and are disposed
of according to the TCP_FLAGS_DISPOSITION option.
122 RuggedCom


















