RuggedRouter® User Guide
The fourth group (lines 30-39) describe connection describe VPN connections (here
“openswantest”). The first line is particularly useful since it indicates the connection
addresses, subnets and that the connection is active (“erouted”). If there are no
entries, then the VPN hasn't been established at all. If there are entries, but no
STATE_QUICK_R2 (IPsec SA established) lines then the IPSec parameters are
configured, but the tunnel hasn't been established. This can be normal, tunnels become
active once the Phase 1 and Phase 2 security associations are created, and this usually
only occurs after traffic is flowing. The associations then get torn down after a timeout
period.
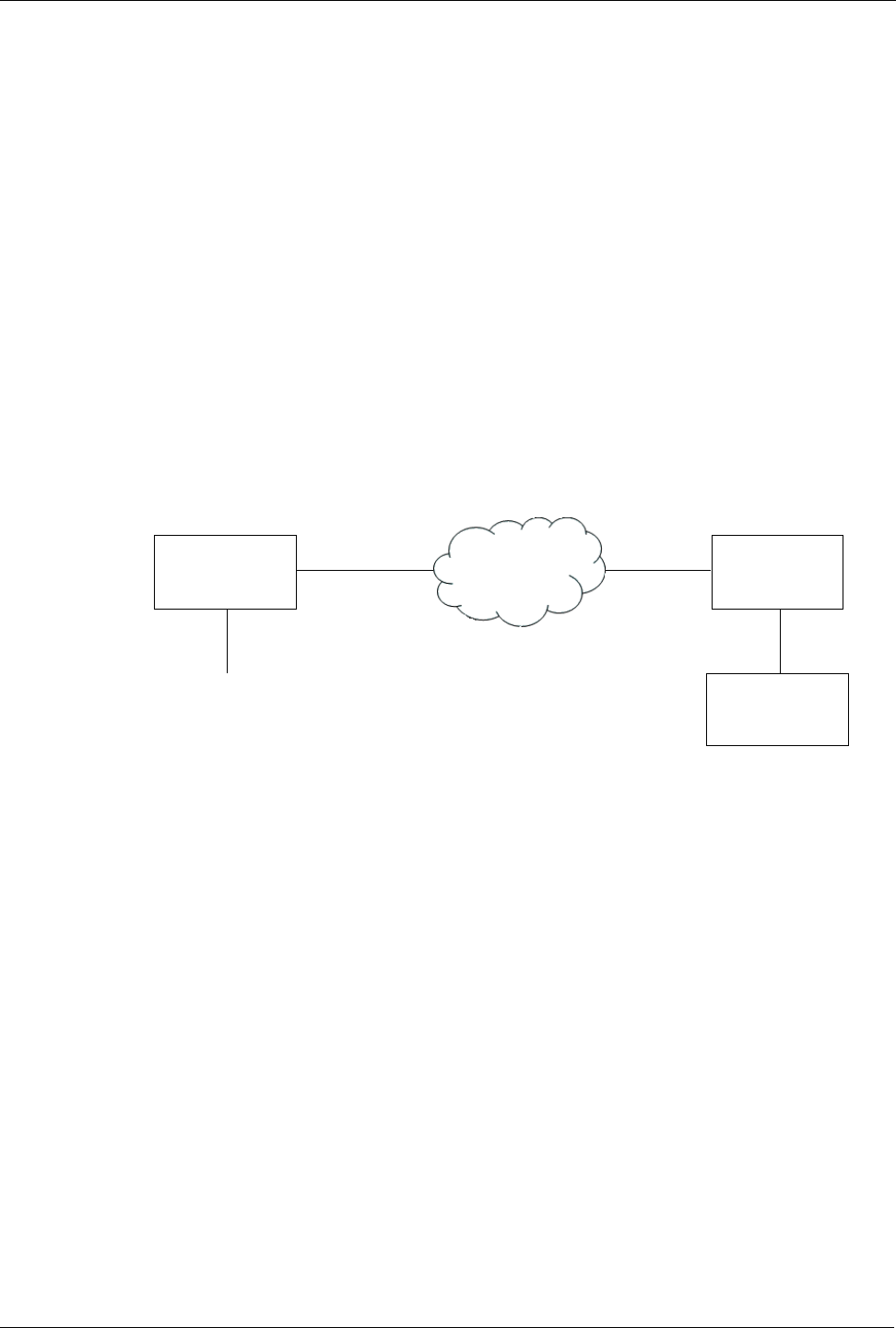
IPSec X.509 Roaming Client Example
This example details how to set up IPSec connections using X.509 certificates on the
router. The router will provide an IPSec gateway to a number of remote clients that
connect via an Internet connection. Each of the clients will fetch an IP address locally
from a DHCP server, and it is assumed (but not required) that network address
translation will be applied at the client end. Each of the clients should “appear” on the
local network on a specific IP address. In this example the clients are laptop PCs.
Select A Certificate Authority
Begin by constructing the required certificates. You may construct the certificates
using a RuggedRouter or a third party tool. The device that is used to build the
certificates is known as the certificate authority. There are advantages and
disadvantages to using the router itself as the authority. It is convenient to use if it is
the only router in the network and many clients will be connecting to it. On the other
hand, if the router holds the certificate authority and is compromised, all certificates
must be constructed again.
Ensure that the the Certificate Authority generates certificates with a reasonable life
and generates keys of at least 1024 bits in length.
148 RuggedCom
Figure 129: End To End Backup Example
Remote
Gateway
Router
192.168.17.3
(10.0.1.1)
eth1
Internet
Laptop
(IPSec Client)
w1ppp
vpn@xyz.com
Local Network
(10.0.0.0/8)


















