38 WiFi Networks
Do not save settings
If you select this option, you can connect to the network this time, but no settings will be saved
and no profile created.
Accessing a Closed Network
To access a closed network with Sprint SmartView, you must set up a network profile for that
network. Follow these steps:
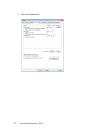
1. Select Profiles from the Tools menu. The Network Profiles window will be displayed.
2. Select Add New Profile from the Settings menu. A list of network profile types appears.
3. Select WiFi.
4. Click Add. The first page of properties for the new profile appears.
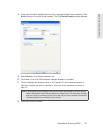
5. Enter the name of the network you want to add in the SSID field. The network name is
case-sensitive and must be entered exactly as provided by the network administrator.
6. Check This is a non-broadcasted network (Closed) to identify this as a closed network.
7. Complete the remaining fields on this page as instructed by the network administrator.
8. Click Next to continue to the General page.
9. Configure the fields on the General page as desired.
10. Click Finish to exit.
Introduction to WiFi Encryption
Unlike a wired local network, a wireless network cannot easily be protected from potential
intruders by physical barriers such as walls. Since radio signals travel through physical objects,
a potential intruder merely need listen with the right equipment to see the traffic traveling across
a wireless network. For this reason, public wireless networks often employ encryption to protect
their users.
To access an encrypted network you will need the Encryption Key used by the network you
wish to access.
Encryption Keys
An encryption key is a code key used to encrypt data exchanged between an encrypted
network and Sprint SmartView. You cannot exchange data with an encrypted network without
having the appropriate encryption key.
There are two ways to obtain an encryption key:
● Obtain a key from the administrator of the WiFi network you are trying to access.
● Configure 802.1x Authentication according to the instructions of the network's
administrator. A key will be provided automatically as part of the login process.