Chapter 16. Managing Networks and Traffic
154
• Account, Security Group. (Add by Account only) To accept only traffic from another security
group, enter the CloudPlatform account and name of a security group that has already been
defined in that account. To allow traffic between VMs within the security group you are editing
now, enter its name (that is, the same name you chose in step 3).
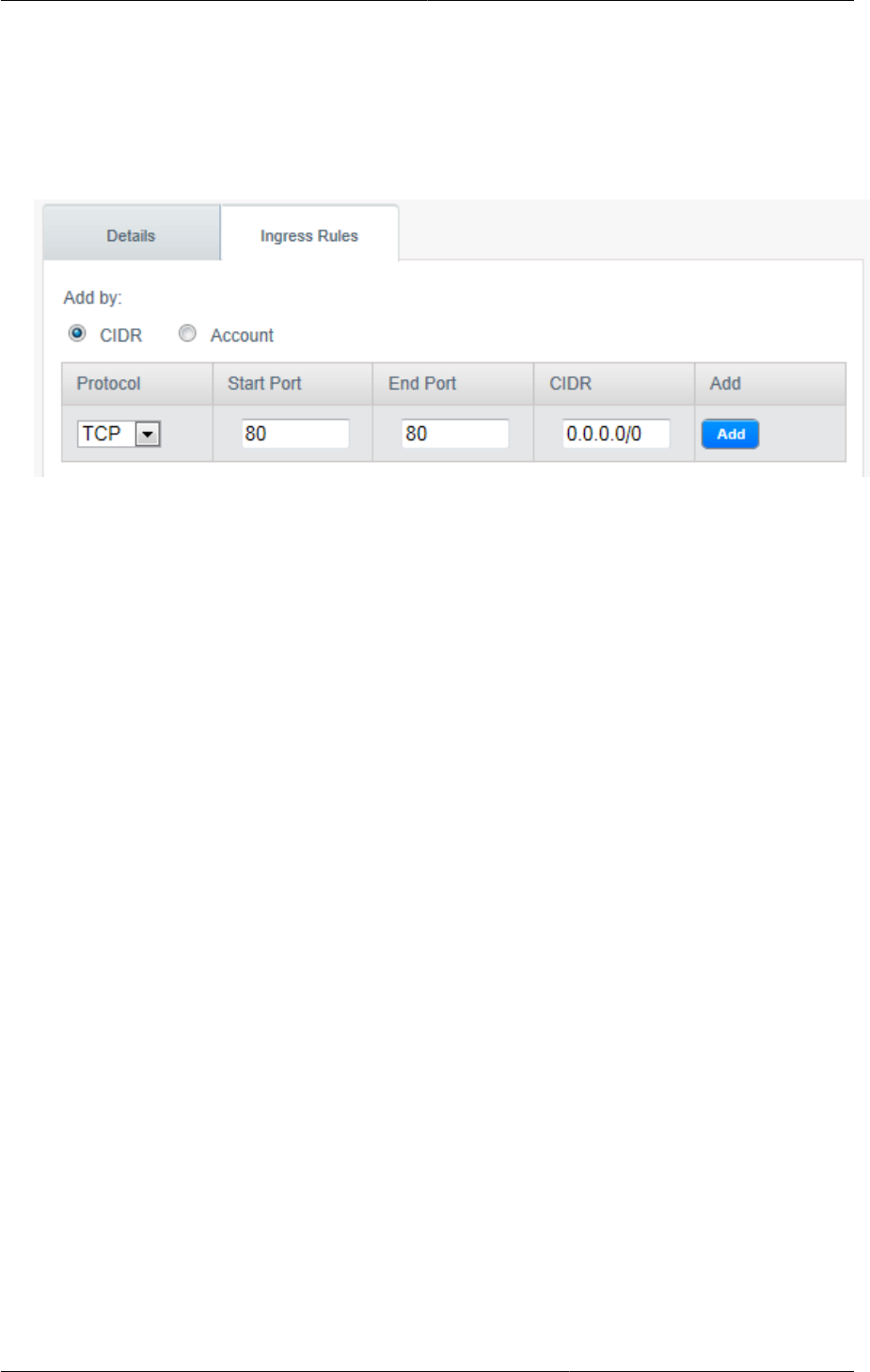
The following example allows inbound HTTP access from anywhere:
5. To add an egress rule, click the Egress Rules tab and fill out the following fields to specify what
type of traffic is allowed to be sent out of VM instances in this security group. If no egress rules are
specified, then all traffic will be allowed out. Once egress rules are specified, the following types
of traffic are allowed out: traffic specified in egress rules; queries to DNS and DHCP servers; and
responses to any traffic that has been allowed in through an ingress rule
• Add by CIDR/Account. Indicate whether the destination of the traffic will be defined by IP
address (CIDR) or an existing security group in a CloudPlatform account (Account). Choose
Account if you want to allow outgoing traffic to all VMs in another security group.
• Protocol. The networking protocol that VMs will use to send outgoing traffic. TCP and UDP are
typically used for data exchange and end-user communications. ICMP is typically used to send
error messages or network monitoring data.
• Start Port, End Port. (TCP, UDP only) A range of listening ports that are the destination for the
outgoing traffic. If you are opening a single port, use the same number in both fields.
• ICMP Type, ICMP Code. (ICMP only) The type of message and error code that will be sent
• CIDR. (Add by CIDR only) To send traffic only to IP addresses within a particular address block,
enter a CIDR or a comma-separated list of CIDRs. The CIDR is the base IP address of the
destination. For example, 192.168.0.0/22. To allow all CIDRs, set to 0.0.0.0/0.
• Account, Security Group. (Add by Account only) To allow traffic to be sent to another security
group, enter the CloudPlatform account and name of a security group that has already been
defined in that account. To allow traffic between VMs within the security group you are editing
now, enter its name (that is, the same name you chose in step 3).
6. Click Add.
16.7. External Firewalls and Load Balancers
CloudPlatform is capable of replacing its Virtual Router with an external Juniper SRX or Cisco ASA
1000v Cloud Firewall device and an optional external Citrix NetScaler or BigIP F5 load balancer for
gateway and load balancing services. In this case, the VMs use the SRX or ASA as their gateway.