Egress Firewall Rules in an Advanced Zone
187
2. In the left navigation, choose Network.
3. In Select view, choose Guest networks, then click the Guest network you want.
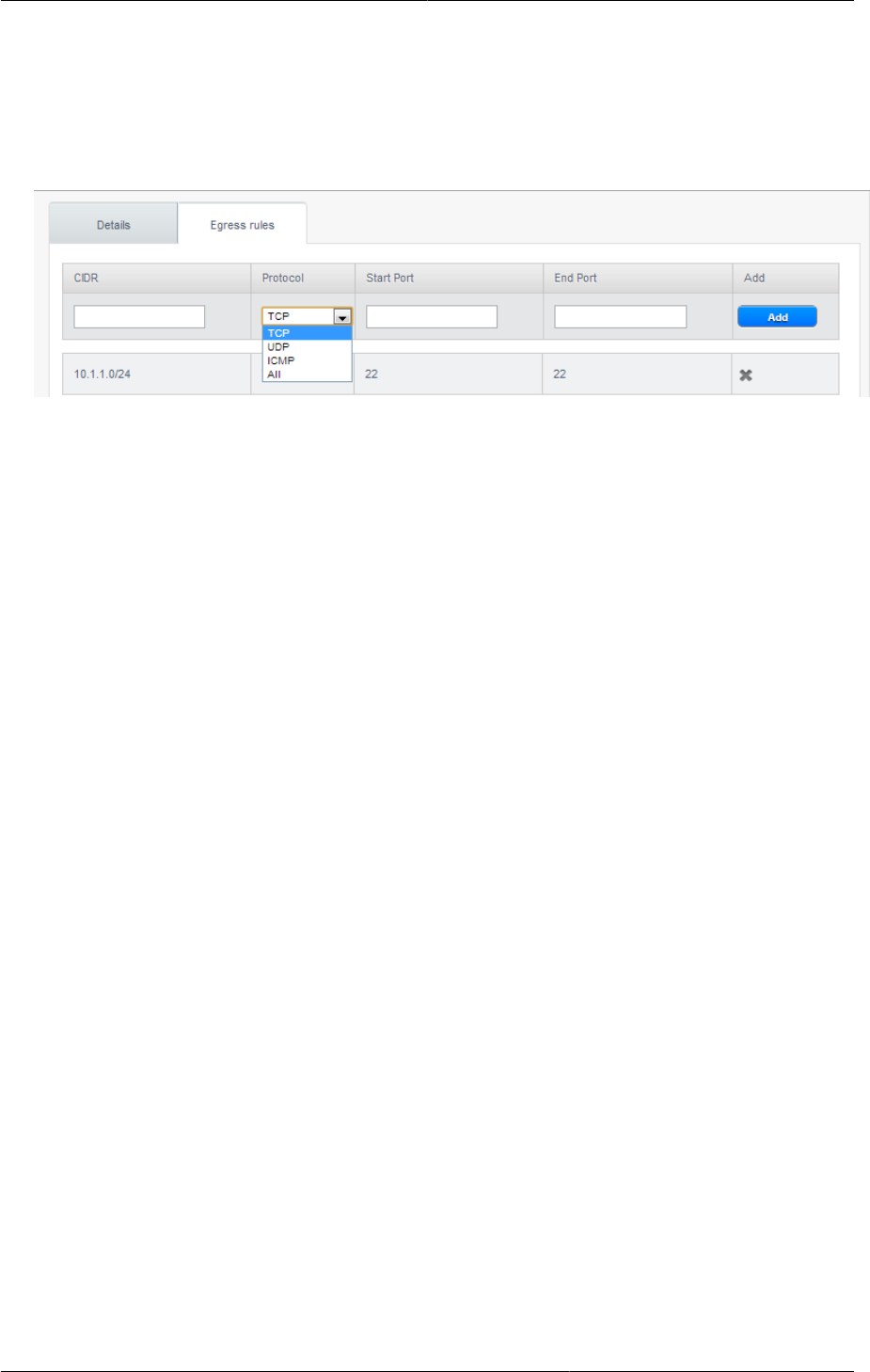
4. To add an egress rule, click the Egress rules tab and fill out the following fields to specify what
type of traffic is allowed to be sent out of VM instances in this guest network:
• CIDR: (Add by CIDR only) To send traffic only to the IP addresses within a particular address
block, enter a CIDR or a comma-separated list of CIDRs. The CIDR is the base IP address of
the destination. For example, 192.168.0.0/22. To allow all CIDRs, set to 0.0.0.0/0.
• Protocol: The networking protocol that VMs uses to send outgoing traffic. The TCP and UDP
protocols are typically used for data exchange and end-user communications. The ICMP
protocol is typically used to send error messages or network monitoring data.
• Start Port, End Port: (TCP, UDP only) A range of listening ports that are the destination for the
outgoing traffic. If you are opening a single port, use the same number in both fields.
• ICMP Type, ICMP Code: (ICMP only) The type of message and error code that are sent.
5. Click Add.
16.21.1.3. Configuring the Default Egress Policy
The default egress policy for Isolated guest network is configured by using Network offering. Use the
create network offering option to determine whether the default policy should be block or allow all the
traffic to the public network from a guest network. Use this network offering to create the network. If no
policy is specified, by default all the traffic is allowed from the guest network that you create by using
this network offering.
You have two options: Allow and Deny.
Allow
If you select Allow for a network offering, by default egress traffic is allowed. However, when an egress
rule is configured for a guest network, rules are applied to block the specified traffic and rest are
allowed. If no egress rules are configured for the network, egress traffic is accepted.
Deny
If you select Deny for a network offering, by default egress traffic for the guest network is blocked.
However, when an egress rules is configured for a guest network, rules are applied to allow the
specified traffic. While implementing a guest network, CloudPlatform adds the firewall egress rule
specific to the default egress policy for the guest network.
This feature is supported only on virtual router and Juniper SRX.
1. Create a network offering with your desirable default egress policy: