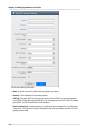
Setting Up a Site-to-Site VPN Connection
195
Note
The IKE peers (VPN end points) authenticate each other by computing and sending a
keyed hash of data that includes the Preshared key. If the receiving peer is able to create
the same hash independently by using its Preshared key, it knows that both peers must
share the same secret, thus authenticating the customer gateway.
• IKE Encryption: The Internet Key Exchange (IKE) policy for phase-1. The supported encryption
algorithms are AES128, AES192, AES256, and 3DES. Authentication is accomplished through
the Preshared Keys.
Note
The phase-1 is the first phase in the IKE process. In this initial negotiation phase, the two
VPN endpoints agree on the methods to be used to provide security for the underlying IP
traffic. The phase-1 authenticates the two VPN gateways to each other, by confirming that
the remote gateway has a matching Preshared Key.
• IKE Hash: The IKE hash for phase-1. The supported hash algorithms are SHA1 and MD5.
• IKE DH: A public-key cryptography protocol which allows two parties to establish a shared
secret over an insecure communications channel. The 1536-bit Diffie-Hellman group is used
within IKE to establish session keys. The supported options are None, Group-5 (1536-bit) and
Group-2 (1024-bit).
• ESP Encryption: Encapsulating Security Payload (ESP) algorithm within phase-2. The
supported encryption algorithms are AES128, AES192, AES256, and 3DES.
Note
The phase-2 is the second phase in the IKE process. The purpose of IKE phase-2 is to
negotiate IPSec security associations (SA) to set up the IPSec tunnel. In phase-2, new
keying material is extracted from the Diffie-Hellman key exchange in phase-1, to provide
session keys to use in protecting the VPN data flow.
• ESP Hash: Encapsulating Security Payload (ESP) hash for phase-2. Supported hash
algorithms are SHA1 and MD5.
• Perfect Forward Secrecy: Perfect Forward Secrecy (or PFS) is the property that ensures that
a session key derived from a set of long-term public and private keys will not be compromised.
This property enforces a new Diffie-Hellman key exchange. It provides the keying material
that has greater key material life and thereby greater resistance to cryptographic attacks. The
available options are None, Group-5 (1536-bit) and Group-2 (1024-bit). The security of the key
exchanges increase as the DH groups grow larger, as does the time of the exchanges.