Chapter 24 IPSec VPN
ISG50 User’s Guide
374
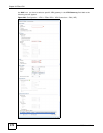
Policy
Enforcement
Clear this to allow traffic with source and destination IP addresses that do not
match the local and remote policy to use the VPN tunnel. Leave this cleared
for free access between the local and remote networks.
Selecting this restricts who can use the VPN tunnel. The ISG50 drops traffic
with source and destination IP addresses that do not match the local and
remote policy.
Phase 2 Settings
SA Life Time Type the maximum number of seconds the IPSec SA can last. Shorter life
times provide better security. The ISG50 automatically negotiates a new IPSec
SA before the current one expires, if there are users who are accessing
remote resources.
Active Protocol Select which protocol you want to use in the IPSec SA. Choices are:
AH (RFC 2402) - provides integrity, authentication, sequence integrity (replay
resistance), and non-repudiation but not encryption. If you select AH, you
must select an Authentication algorithm.
ESP (RFC 2406) - provides encryption and the same services offered by AH,
but its authentication is weaker. If you select ESP, you must select an
Encryption algorithm and Authentication algorithm.
Both AH and ESP increase processing requirements and latency (delay).
The ISG50 and remote IPSec router must use the same active protocol.
Encapsulation Select which type of encapsulation the IPSec SA uses. Choices are
Tunnel - this mode encrypts the IP header information and the data.
Transport - this mode only encrypts the data.
The ISG50 and remote IPSec router must use the same encapsulation.
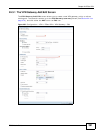
Proposal
Add Click this to create a new entry.
Edit Select an entry and click this to be able to modify it.
Remove Select an entry and click this to delete it.
# This field is a sequential value, and it is not associated with a specific
proposal. The sequence of proposals should not affect performance
significantly.
Encryption This field is applicable when the Active Protocol is ESP. Select which key size
and encryption algorithm to use in the IPSec SA. Choices are:
NULL - no encryption key or algorithm
DES - a 56-bit key with the DES encryption algorithm
3DES - a 168-bit key with the DES encryption algorithm
AES128 - a 128-bit key with the AES encryption algorithm
AES192 - a 192-bit key with the AES encryption algorithm
AES256 - a 256-bit key with the AES encryption algorithm
The ISG50 and the remote IPSec router must both have at least one proposal
that uses use the same encryption and the same key.
Longer keys are more secure, but require more processing power, resulting in
increased latency and decreased throughput.
Table 123 Configuration > VPN > IPSec VPN > VPN Connection > Edit (continued)
LABEL DESCRIPTION