Chapter 24 IPSec VPN
ISG50 User’s Guide
382
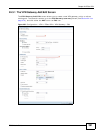
Each field is described in the following table.
Table 126 Configuration > VPN > IPSec VPN > VPN Gateway > Edit
LABEL DESCRIPTION
Show Advance
Settings / Hide
Advance Settings
Click this button to display a greater or lesser number of configuration fields.
General Settings
VPN Gateway
Name
Type the name used to identify this VPN gateway. You may use 1-31
alphanumeric characters, underscores(
_), or dashes (-), but the first
character cannot be a number. This value is case-sensitive.
Gateway Settings
My Address Select how the IP address of the ISG50 in the IKE SA is defined.
If you select Interface, select the Ethernet interface, VLAN interface, virtual
Ethernet interface, virtual VLAN interface or PPPoE/PPTP interface. The IP
address of the ISG50 in the IKE SA is the IP address of the interface.
If you select Domain Name / IP, enter the domain name or the IP address
of the ISG50. The IP address of the ISG50 in the IKE SA is the specified IP
address or the IP address corresponding to the domain name. 0.0.0.0 is
invalid.
Peer Gateway
Address
Select how the IP address of the remote IPSec router in the IKE SA is
defined.
Select Static Address to enter the domain name or the IP address of the
remote IPSec router. You can provide a second IP address or domain name
for the ISG50 to try if it cannot establish an IKE SA with the first one.
Select Dynamic Address if the remote IPSec router has a dynamic IP
address (and does not use DDNS).
Authentication
Note: The ISG50 and remote IPSec router must use the same authentication
method to establish the IKE SA.
Pre-Shared Key Select this to have the ISG50 and remote IPSec router use a pre-shared key
(password) to identify each other when they negotiate the IKE SA. Type the
pre-shared key in the field to the right. The pre-shared key can be
• 8 - 32 alphanumeric characters or ,;|`~!@#$%^&*()_+\{}':./<>=-".
• 8 - 32 pairs of hexadecimal (0-9, A-F) characters, preceded by “0x”.
If you want to enter the key in hexadecimal, type “0x” at the beginning of the
key. For example, "0x0123456789ABCDEF" is in hexadecimal format; in
“0123456789ABCDEF” is in ASCII format. If you use hexadecimal, you must
enter twice as many characters since you need to enter pairs.
The ISG50 and remote IPSec router must use the same pre-shared key.
Certificate Select this to have the ISG50 and remote IPSec router use certificates to
authenticate each other when they negotiate the IKE SA. Then select the
certificate the ISG50 uses to identify itself to the remote IPsec router.
This certificate is one of the certificates in My Certificates. If this certificate
is self-signed, import it into the remote IPsec router. If this certificate is
signed by a CA, the remote IPsec router must trust that CA.
Note: The IPSec routers must trust each other’s certificates.
The ISG50 uses one of its Trusted Certificates to authenticate the remote
IPSec router’s certificate. The trusted certificate can be a self-signed
certificate or that of a trusted CA that signed the remote IPSec router’s
certificate.