Chapter 24 IPSec VPN
ISG50 User’s Guide
385
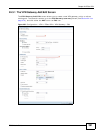
# This field is a sequential value, and it is not associated with a specific
proposal. The sequence of proposals should not affect performance
significantly.
Encryption Select which key size and encryption algorithm to use in the IKE SA. Choices
are:
DES - a 56-bit key with the DES encryption algorithm
3DES - a 168-bit key with the DES encryption algorithm
AES128 - a 128-bit key with the AES encryption algorithm
AES192 - a 192-bit key with the AES encryption algorithm
AES256 - a 256-bit key with the AES encryption algorithm
The ISG50 and the remote IPSec router must use the same key size and
encryption algorithm. Longer keys require more processing power, resulting
in increased latency and decreased throughput.
Authentication Select which hash algorithm to use to authenticate packet data in the IPSec
SA. Choices are SHA1 and MD5. SHA1 is generally considered stronger than
MD5, but it is also slower.
The remote IPSec router must use the same authentication algorithm.
Key Group Select which Diffie-Hellman key group (DHx) you want to use for encryption
keys. Choices are:
DH1 - use a 768-bit random number
DH2 - use a 1024-bit random number
DH5 - use a 1536-bit random number
The longer the key, the more secure the encryption, but also the longer it
takes to encrypt and decrypt information. Both routers must use the same
DH key group.
NAT Traversal Select this if any of these conditions are satisfied.
• This IKE SA might be used to negotiate IPSec SAs that use ESP as the
active protocol.
• There are one or more NAT routers between the ISG50 and remote IPSec
router, and these routers do not support IPSec pass-thru or a similar
feature.
The remote IPSec router must also enable NAT traversal, and the NAT routers
have to forward packets with UDP port 500 and UDP 4500 headers
unchanged.
Dead Peer
Detection (DPD)
Select this check box if you want the ISG50 to make sure the remote IPSec
router is there before it transmits data through the IKE SA. The remote IPSec
router must support DPD. If there has been no traffic for at least 15 seconds,
the ISG50 sends a message to the remote IPSec router. If the remote IPSec
router responds, the ISG50 transmits the data. If the remote IPSec router
does not respond, the ISG50 shuts down the IKE SA.
If the remote IPSec router does not support DPD, see if you can use the VPN
connection connectivity check (see Section 24.2.1 on page 371).
Extended
Authentication
When multiple IPSec routers use the same VPN tunnel to connect to a single
VPN tunnel (telecommuters sharing a tunnel for example), use extended
authentication to enforce a user name and password check. This way even
though they all know the VPN tunnel’s security settings, each still has to
provide a unique user name and password.
Table 126 Configuration > VPN > IPSec VPN > VPN Gateway > Edit (continued)
LABEL DESCRIPTION