Chapter 24 IPSec VPN
ISG50 User’s Guide
384
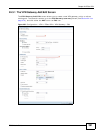
Content This field is disabled if the Peer ID Type is Any. Type the identity of the
remote IPSec router during authentication. The identity depends on the Peer
ID Type.
If the ISG50 and remote IPSec router do not use certificates,
IP - type an IP address; see the note at the end of this description.
DNS - type the domain name; you can use up to 31 ASCII characters
including spaces, although trailing spaces are truncated. This value is only
used for identification and can be any string.
E-mail - the ISG50 is identified by an e-mail address; you can use up to 31
ASCII characters including spaces, although trailing spaces are truncated.
This value is only used for identification and can be any string.
If the ISG50 and remote IPSec router use certificates, type the following
fields from the certificate used by the remote IPSec router.
IP - subject alternative name field; see the note at the end of this
description.
DNS - subject alternative name field
E-mail - subject alternative name field
Subject Name - subject name (maximum 255 ASCII characters, including
spaces)
Note: If Peer ID Type is IP, please read the rest of this section.
If you type 0.0.0.0, the ISG50 uses the IP address specified in the Secure
Gateway Address field. This is not recommended in the following
situations:
• There is a NAT router between the ISG50 and remote IPSec router.
• You want the remote IPSec router to be able to distinguish between IPSec
SA requests that come from IPSec routers with dynamic WAN IP
addresses.
In these situations, use a different IP address, or use a different Peer ID
Type.
Phase 1 Settings
SA Life Time
(Seconds)
Type the maximum number of seconds the IKE SA can last. When this time
has passed, the ISG50 and remote IPSec router have to update the
encryption and authentication keys and re-negotiate the IKE SA. This does
not affect any existing IPSec SAs, however.
Negotiation
Mode
Select the negotiation mode to use to negotiate the IKE SA. Choices are
Main - this encrypts the ISG50’s and remote IPSec router’s identities but
takes more time to establish the IKE SA
Aggressive - this is faster but does not encrypt the identities
The ISG50 and the remote IPSec router must use the same negotiation
mode.
Proposal
Add Click this to create a new entry.
Edit Select an entry and click this to be able to modify it.
Remove Select an entry and click this to delete it.
Table 126 Configuration > VPN > IPSec VPN > VPN Gateway > Edit (continued)
LABEL DESCRIPTION