WS 2000 Use Cases 9-65
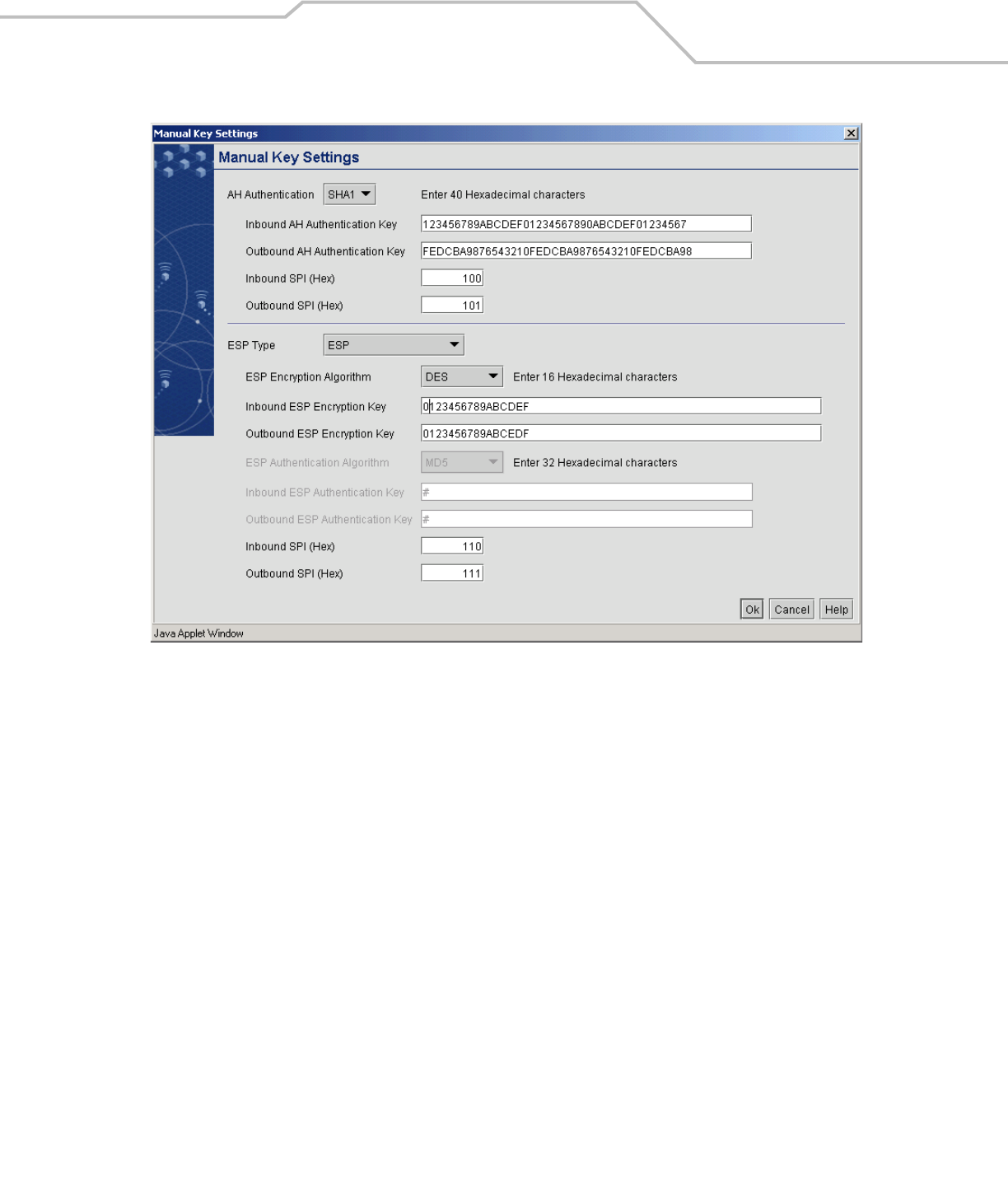
The AH Authentication protocol is used between the two WS 2000 switches to authorize initialization of the VPN tunnel.
The AH authentication method must match on both switches and the inbound key on one WS 2000 must match the outbound
key on the other. Leo selects Secure Hash Algorithm 1 or SHA1 as the method and enters inbound and outbound 40
character authentication keys.
The inbound Security Parameter Index (SPI) for this WS 2000 must match the outbound SPI from the other switch and
vice versa. Leo enters 100 for the Inbound SPI and 101 for the Outbound SPI.
The Encapsulating Security Payload or ESP is specified in the lower section. This specifies how the network packets
will be encrypted between the two ends of the VPN tunnel. Leo chooses DES encryption and specifies the Inbound ESP
Encryption Key so that it will match the Outbound ESP Encryption Key on the other WS 2000. He also specifies the
Outbound ESP Encryption Key on this WS 2000 so that it will match the Inbound ESP Encryption Key on the other switch.
Finally, the Inbound and Outbound SPI fields in the encryption section on this WS 2000 must match the Outbound and
Inbound SPIs on the other WS 2000. Leo enters 110 for the Inbound SPI and 111 for the Outbound SPI.
Leo clicks Ok to record the Manual Key Settings. Then he clicks the Apply button to confirm this configuration.
The switch is now configured!
Installing the Access Ports and Testing
The switch is now configured. Leo connects the switch’s WAN port to the VPN appliance that goes to the outside world. He
gets three laptops and sets each of them to use DHCP for IP address assignment, 802.1x EAP for user authentication, and
WPA-TKIP for data encryption over the wireless link. He uses the first laptop to connect to the engineering WLAN, the