Chapter 7: Configuring the Embedded Authentication Server (EAS)
206
About Certificates
Certificates encrypt communication between the internal RADIUS server,
RADIUS clients, and the supplicants and HTTPS clients.
There are two types of certificates:
The trusted certificate authority (CA) certificate (commonly referred to
as the “root certificate” or “root cert”) is the public key. Trusted CA
certificates can be in *.PEM format or *.CER format. They can contain
several trusted CAs but should be kept to a maximum file size of 2Kb.
The server certificate (sometimes referred to as the client certificate) is
the private key. Server certificates can be in either PKCS12 (*.P12/
*.PFX) or *.PEM format.
Understanding
Which Access
Points Need
Certificates
The next table summarizes when an access point needs to have a CA
certificate and/or a server certificate installed on it.
Understanding
Which
Certificates Are
Installed by
Default
Your access point comes from the factory with a unique server certificate
with a unique common name and passphrase. It also comes with a trusted
CA certificate that supports clients running the TLS authentication type.
These certificates support the secure web browser interface and provide
basic security for all authentication types.
Allied Telesyn can provide the service of acting as a certificate authority
and can issue certificates. For more information, contact your local ATI
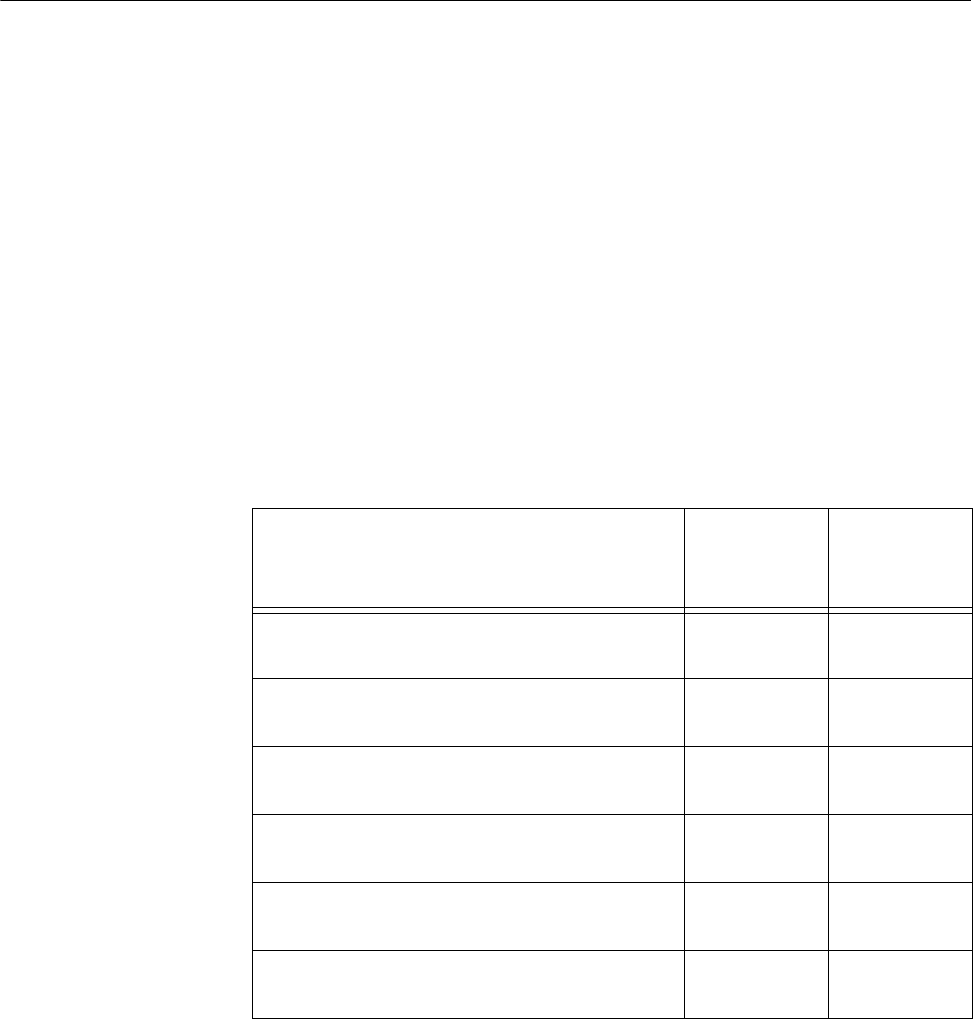
Table 57. Access Points and Certificates
Access Point
CA
Certificate
Needed
Server
Certificate
Needed
If you want to use the secure web browser
(HTTPS) on this access point
No Yes
If this access point is an authentication
server in your 802.1x-enabled network
Yes Yes
If this access point is a supplicant
EAP-TTLS client
Yes No
If this access point is a supplicant
EAP-TLS client
Yes Yes
If this access point is a backup RADIUS
server
No Yes
If the child access point is using SWAP
and is an authenticator access point
No No


















