Rate Limiting
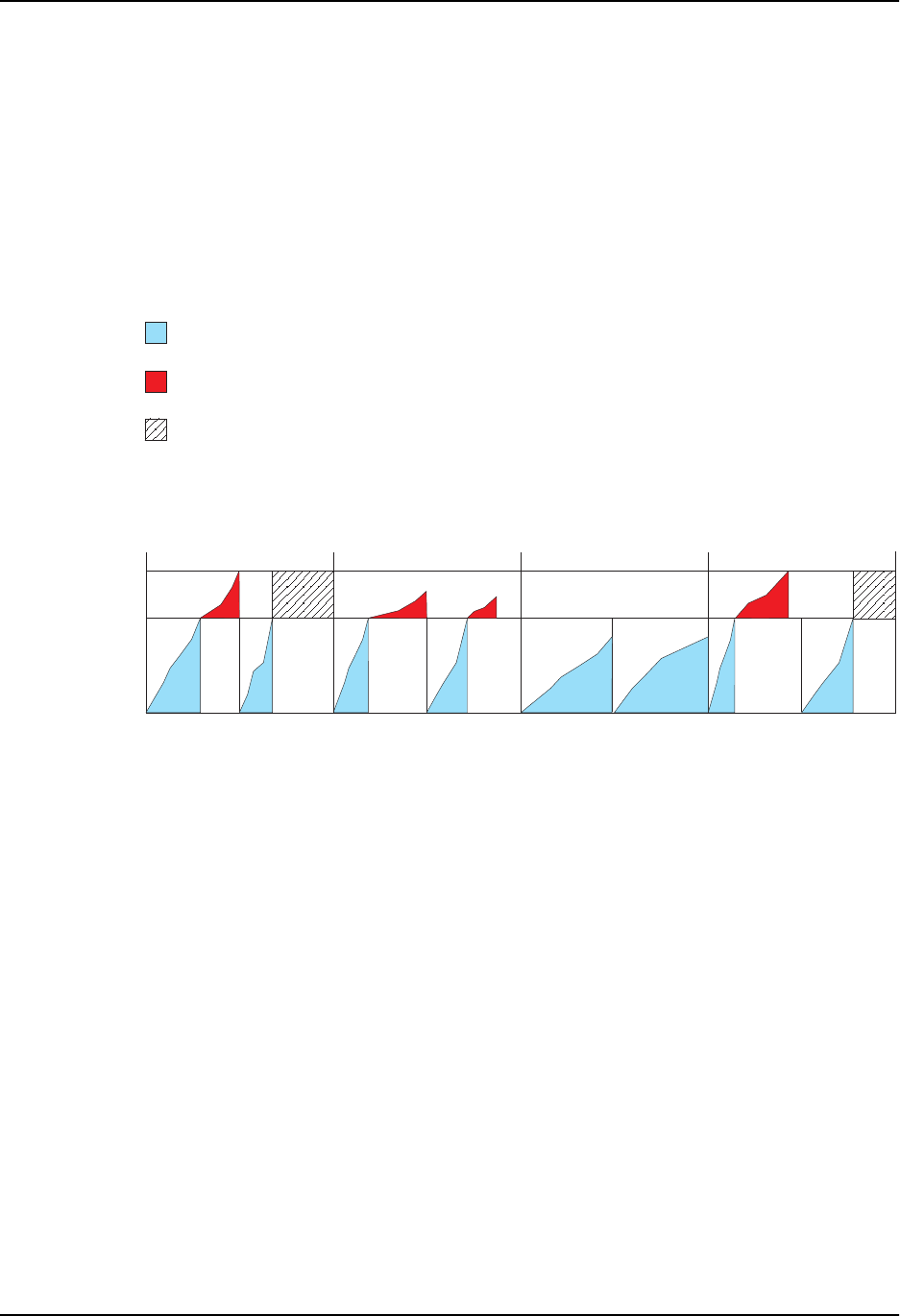
Figure 4.7 shows an example of eight Committed Time Intervals. The software drops traffic in the second and
eighth intervals because the interface receives traffic that matches the rule after the rule has already matched the
maximum number of bytes for the Normal Burst Size and Excess Burst Size.
In the third and fourth Committed Time Intervals, the rule matches the maximum number of bytes for the Normal
Burst Size, and then matches additional bytes. However, the total number of excess bytes that match the rule
over these two Committed Time Intervals is not greater than the Excess Burst Size. Therefore, the software does
not drop any of the matching traffic.
In the fifth and sixth Committed Time Intervals, the rule matches bytes but does not match even the maximum
number of Normal Burst Size bytes in either interval. As a result, the rule does not need to apply the exceed
action to any of the traffic that matches the rule in these intervals.
Normal action = change IP precedence
to 5 and forward
Exceed action = change IP precedence
to 0 and forward
Once maximum Excess Burst Size
is reached, traffic is dropped.
Committed Time
Intervals 1 and 2
Committed Time
Intervals 3 and 4
Committed Time
Intervals 5 and 6
Committed Time
Intervals 7 and 8
Figure 4.7 Traffic after the Excess Burst Size is reached is always dropped
Committed Time Interval
The Committed Time Interval specifies the granularity of the rate policing. The Committed Time Interval can be
from 1/10th second up to one second. The length depends on the ratio of the Average Rate to the Normal Burst
Size, parameters you specify when you configure a rate policy rule. The examples in the previous section all use
a Committed Time Interval of one second. Since the Normal Burst Size is equal to the Average Rate, the ratio is
1:1. Therefore, the Committed Time Interval is one second.
The one-second interval is the least granular. The 1/10th-second interval is the most granular. To obtain the
1/10th-second interval, specify a Normal Burst Size that is 1/10th the Average Rate.
Configuring Adaptive Rate Limiting
To configure Adaptive Rate Limiting, perform the following steps:
• Characterize the traffic you want to manage. You can apply Adaptive Rate Limiting to any of the following:
• All traffic (the default)
• Traffic with certain precedence values sent or received on a specific interface
• Traffic for specific source or destination IP host or network addresses
• Traffic for specific TCP/UDP applications
• Traffic from specific MAC addresses
4 - 13


















