88 Operation
Chapter 4 - System Configuration
interface (numbered 0 to 3), use the vap command. You can configure a name for
each interface using the description command. You can also use the
closed-system command to stop sending the SSID in beacon messages. Set any
other VAP parameters and radio setting as required before enabling the VAP
interface (with the no shutdown command). To view the current 802.11g radio
settings for the VAP interface, use the show interface wireless g [0-3] command
as shown on page 215.
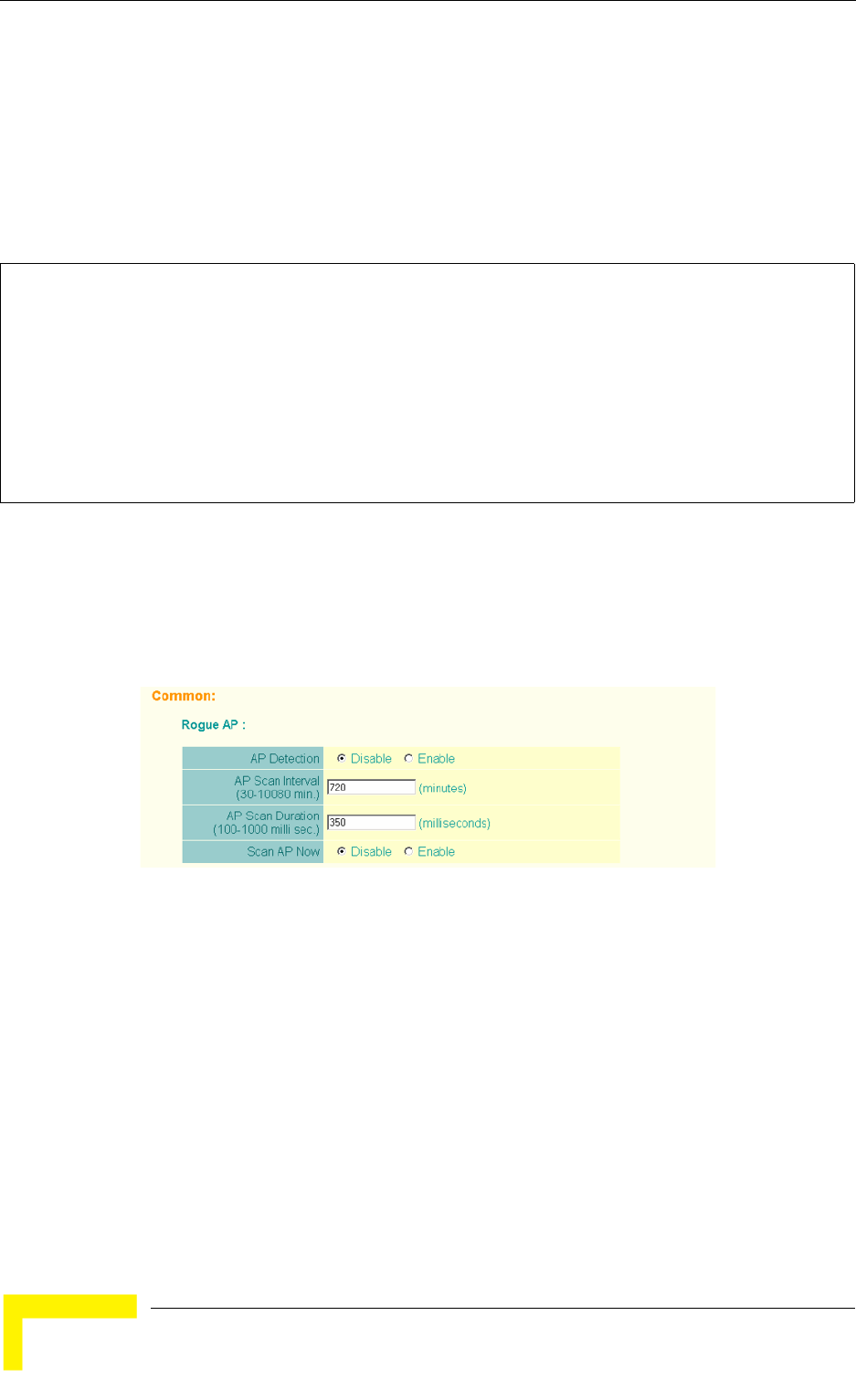
4.6.1.2 Configuring Rogue AP Detection
To configure Rouge AP detection, select the Radio Settings page, and scroll down
to the Rouge AP section.
Rogue AP – A “rogue AP” is either an AP that is not authorized to participate in the
wireless network, or an AP that does not have the correct security configuration.
Rogue APs can allow unauthorized access to the network, or fool client stations
into mistakenly associating with them and thereby blocking access to network
resources.
The AP can be configured to periodically scan all radio channels and find other
APs within range. A database of nearby APs is maintained where any rogue APs
can be identified. During a scan, Syslog messages (see “Enabling System Logging”
Enterprise AP(if-wireless g)#vap 0 215
Enterprise AP(if-wireless g: VAP[0])#description RD-AP#3 224
Enterprise AP(if-wireless g: VAP[0])#vlan-id 1 248
Enterprise AP(if-wireless g: VAP[0])#closed-system 225
Enterprise AP(if-wireless g: VAP[0])#authentication-timeout-
interval 30
226
Enterprise AP(if-wireless g: VAP[0])#association-timeout-
interval 20 226
Enterprise AP(if-wireless g: VAP[0])#max-association 32 225
Enterprise AP(if-wireless g: VAP[0])#pmksa-lifetime 900 241
Enterprise AP(if-wireless g: VAP[0])#
Figure 4-19: Rouge AP Section of Radio Settings page


















