5 - 39
Certificates
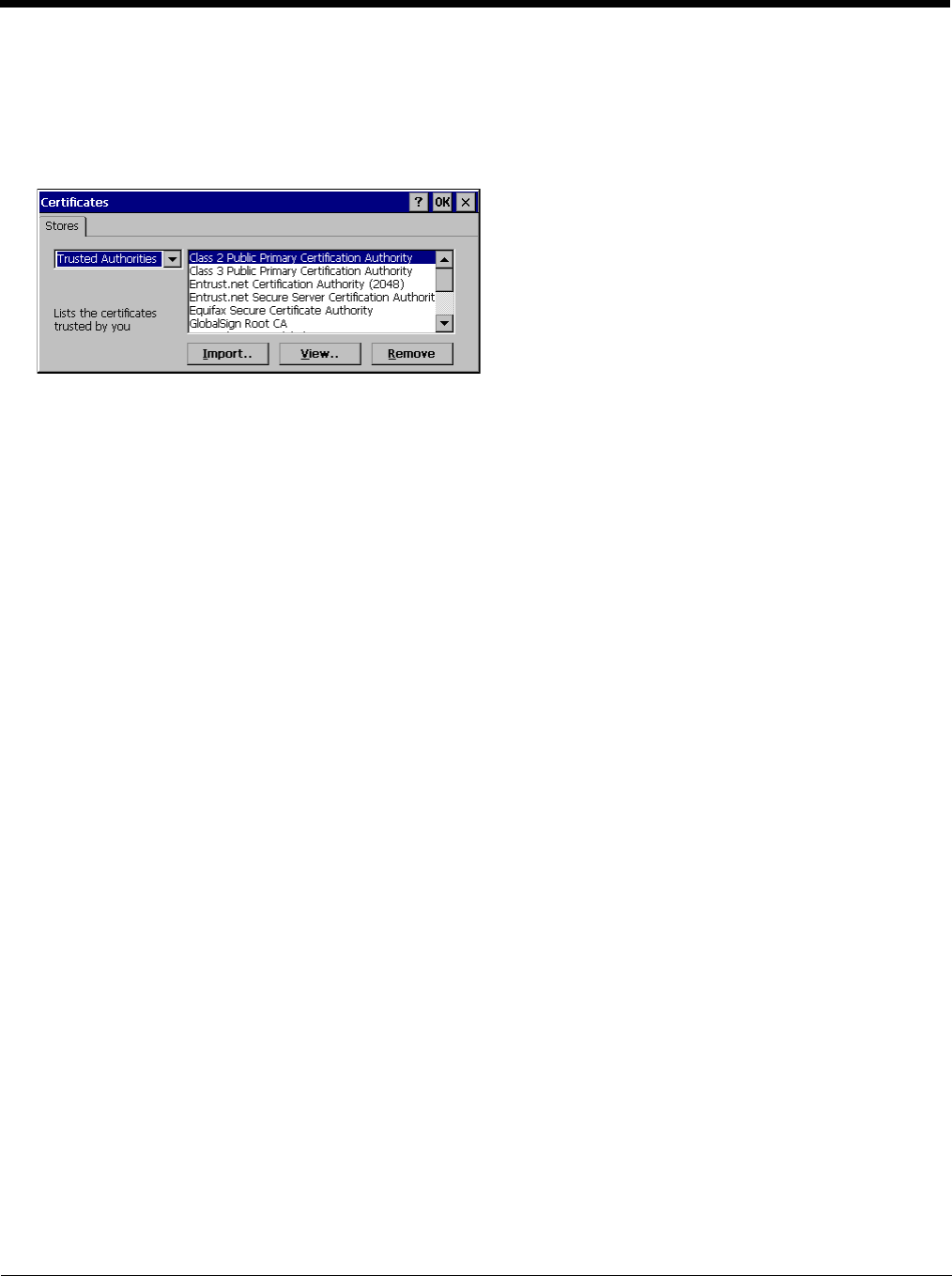
Start > Settings > Control Panel > Certificates
Manage digital certificates used for secure communication.
Note: Digital certificates are date sensitive. If the date on the Thor VM2 is incorrect, wireless authentication will fail.
The Certificates stores tab lists the certificates trusted by the Thor VM2 user.
These values may change based on the type of network security resident in the client, access point or the host system.
Tap the Import button to import a digital certificate file.
Tap t he View button to view a highlighted digital certificate.
Note: Tap the Remove button to remove highlighted certificate files.
Note: Tap the ? button and follow the instructions in the Windows CE Help file when working with trusted authorities and
digital certificates.
Data Collection
Start > Settings > Control Panel > Data Collection
The Data Collection wedge (DC Wedge) software component is the interface between data collection devices such as bar
code scanners or imagers connected to a COM port on the Thor VM2 or bar code scanners wirelessly connected via Blue-
tooth to your Thor VM2. This software component collects the data from the varied sources and presents it to applications
on your Thor VM2 in a transparent manner.
Note: When a HID enabled USB scanner is connected to the Thor VM2 the scanned data is transmitted to the active window
as keystroke messages. The data bypasses the data collection wedge. Any data handling to be applied to the
scanned data, for example strip leading or trailing characters, must be programmed into the scan engine via
configuration bar codes or handled by the application accepting the data.
Use the options on the control panels to set Thor VM2 data collection keyboard wedge parameters, enable or disable
allowed symbologies and assign scan key settings.
Assign baud rate, parity, stop bits and data bits for available COM ports.
Parameters on the Main tab and the COM tab(s) apply to this device only.
Bar code manipulation parameter settings on the Data Options (page 5-44) tab are applied to the incoming data resulting
from successful bar code scans received by the Thor VM2 for processing. The successful bar code scan data may be sent
by
• a wireless Bluetooth scanner,
• or a tethered serial scanner.
Bar Code Readers
The Thor VM2 can use the following external bar code readers:
• Tethered hand-held scanners are tethered to a serial port or a USB host port on the Thor VM2 and are configured
by scanning the engine-specific bar codes in the scanner manufacturer's programming guide. The manufacturer's
guides are usually shipped with the bar code reader.
• Wireless hand-held Bluetooth scanners are configured by scanning the engine-specific bar codes in the scanner
manufacturer's programming guide. The manufacturer's guides are usually shipped with the bar code reader.
• The body worn Bluetooth Ring Scanner module may be using a Symbol 4400 Ring Imager or a Symbol 955 Ring
Scanner. The BTRS module is configured by scanning the bar codes in the Bluetooth Ring Scanner Guide.


















