53-2
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 53 Configuring the TLS Proxy for Encrypted Voice Inspection
Information about the TLS Proxy for Encrypted Voice Inspection
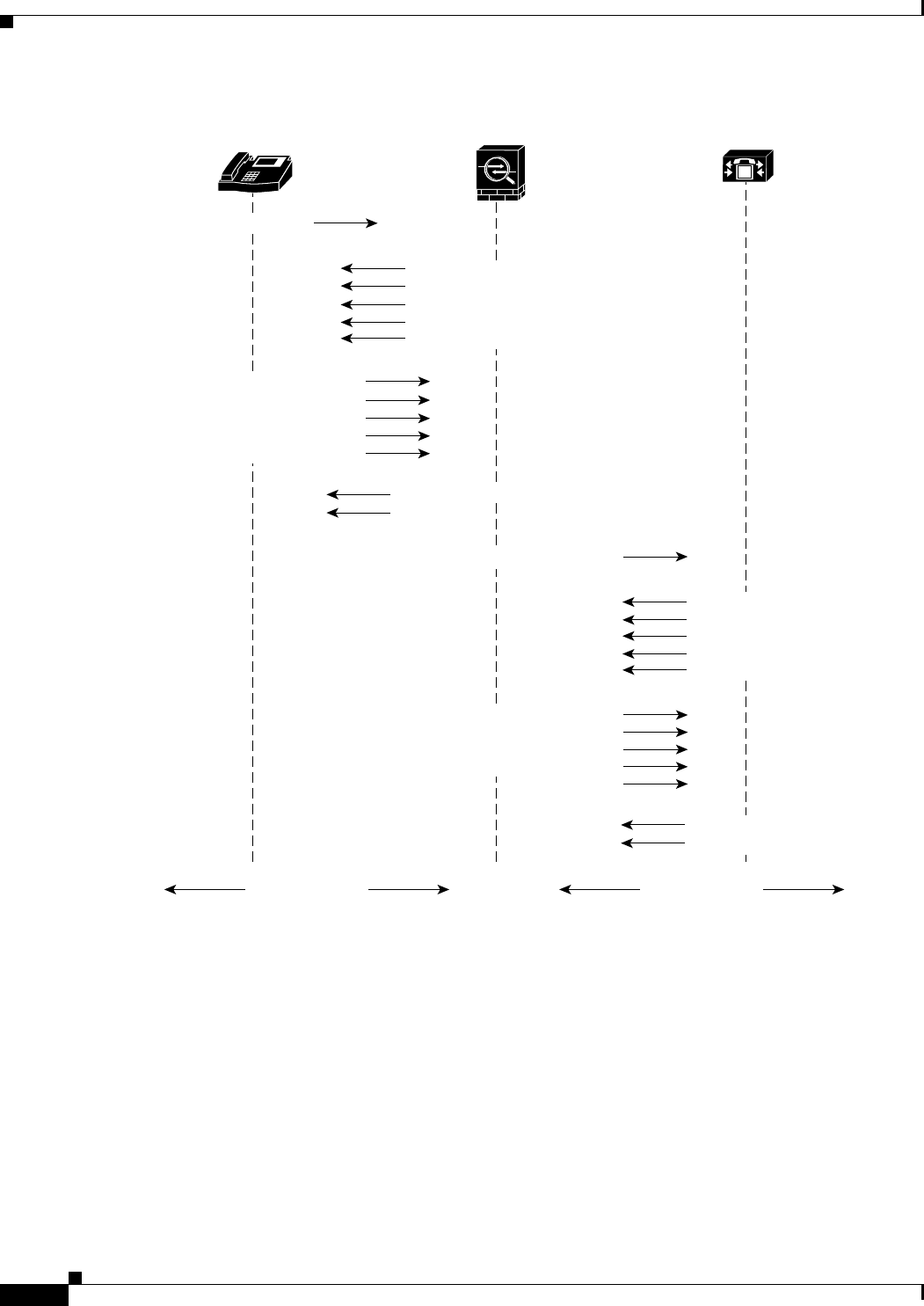
Figure 53-1 TLS Proxy Flow
Decryption and Inspection of Unified Communications Encrypted Signaling
With encrypted voice inspection, the security appliance decrypts, inspects and modifies (as needed, for
example, performing NAT fixup), and re-encrypts voice signaling traffic while all of the existing VoIP
inspection functions for Skinny and SIP protocols are preserved. Once voice signaling is decrypted, the
plaintext signaling message is passed to the existing inspection engines.
The security appliance acts as a TLS proxy between the Cisco IP Phone and Cisco UCM. The proxy is
transparent for the voice calls between the phone and theCisco UCM. Cisco IP Phones download a
Certificate Trust List from the Cisco UCM before registration which contains identities (certificates) of
the devices that the phone should trust, such as TFTP servers and Cisco UCM servers. To support server
IP
M
Client Certificate
Client Key Exchange
Certificate Verify
[Change Cipher Spec]
Finished
(Proxy) Server Hello
(Proxy) Server Certificate
(Proxy) Server Key Exchange
Certificate Request
(Proxy) Server Hello Done
(Proxy) Client Hello
(Proxy) Dynamic Client Certificate
(Proxy) Client Key Exchange
Certificate Verify
[Change Cipher Spec]
Finished
Server Hello
Server Certificate
Server Key Exchange
Certificate Request
Server Hello Done
[Change Cipher Spec]
Finished
182831
Cisco IP Phone Cisco ASA Cisco CallManager
[Change Cipher Spec]
Finished
Application Data INSPECTION Application Data
Client Hello


















