72-60
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 72 Configuring Clientless SSL VPN
SSO Servers
You can choose from four methods when configuring SSO: Auto Signon using basic HTTP and/or
NTLMv1 authentication, HTTP Form protocol, or Computer Associates eTrust SiteMinder (formerly
Netegrity SiteMinder), or SAML, Version 1.1 Browser Post Profile.
Restrictions
The SAML Browser Artifact profile method of exchanging assertions is not supported.
The following sections describe the procedures for setting up SSO with both SiteMinder and SAML
Browser Post Profile.
• Configuring SiteMinder and SAML Browser Post Profile, page 72-60—configures SSO with basic
HTTP or NTLM authentication.
• Configuring Session Settings —configures SSO with the HTTP Form protocol.
The SSO mechanism either starts as part of the AAA process (HTTP Forms) or just after successful user
authentication to either a AAA server (SiteMinder) or a SAML Browser Post Profile server. In these
cases, the clientless SSL VPN server running on the ASA acts as a proxy for the user to the
authenticating server. When a user logs in, the clientless SSL VPN server sends an SSO authentication
request, including username and password, to the authenticating server using HTTPS.
If the authenticating server approves the authentication request, it returns an SSO authentication cookie
to the clientless SSL VPN server. This cookie is kept on the ASA on behalf of the user and used to
authenticate the user to secure websites within the domain protected by the SSO server.
Configuring SiteMinder and SAML Browser Post Profile
SSO authentication with SiteMinder or with SAML Browser Post Profile is separate from AAA and
occurs after the AAA process completes. To set up SiteMinder SSO for a user or group, you must first
configure a AAA server (RADIUS, LDAP and so forth). After the AAA server authenticates the user,
the clientless SSL VPN server uses HTTPS to send an authentication request to the SiteMinder SSO
server.
In addition to configuring the ASA, for SiteMinder SSO, you also must configure your CA SiteMinder
Policy Server with the Cisco authentication scheme. See Adding the Cisco Authentication Scheme to
SiteMinder.
For SAML Browser Post Profile you must configure a Web Agent (Protected Resource URL) for
authentication.
Detailed Steps
Use the SAML server documentation provided by the server software vendor to configure the SAML
server in Relying Party mode. The following fields are displayed:
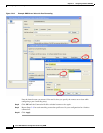
• Server Name—Display only. Displays the names of configured SSO Servers. The minimum number
of characters is 4, and the maximum is 31.
• Authentication Type—Display only. Displays the type of SSO server. The ASA currently supports
the SiteMinder type and the SAML Browser Post Profile type.
• URL—Display only. Displays the SSO server URL to which the ASA makes SSO authentication
requests.
• Secret Key—Display only. Displays the secret key used to encrypt authentication communications
with the SSO server. The key can be comprised of any regular or shifted alphanumeric character.
There is no minimum or maximum number of characters.