B-2
Cisco ASA 5500 Series Configuration Guide using ASDM
Appendix B Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
For LDAP servers, any attribute name can be used to set the group policy for the session. The LDAP
attribute map that you configure on the ASA maps the LDAP attribute to the Cisco attribute
IETF-Radius-Class.
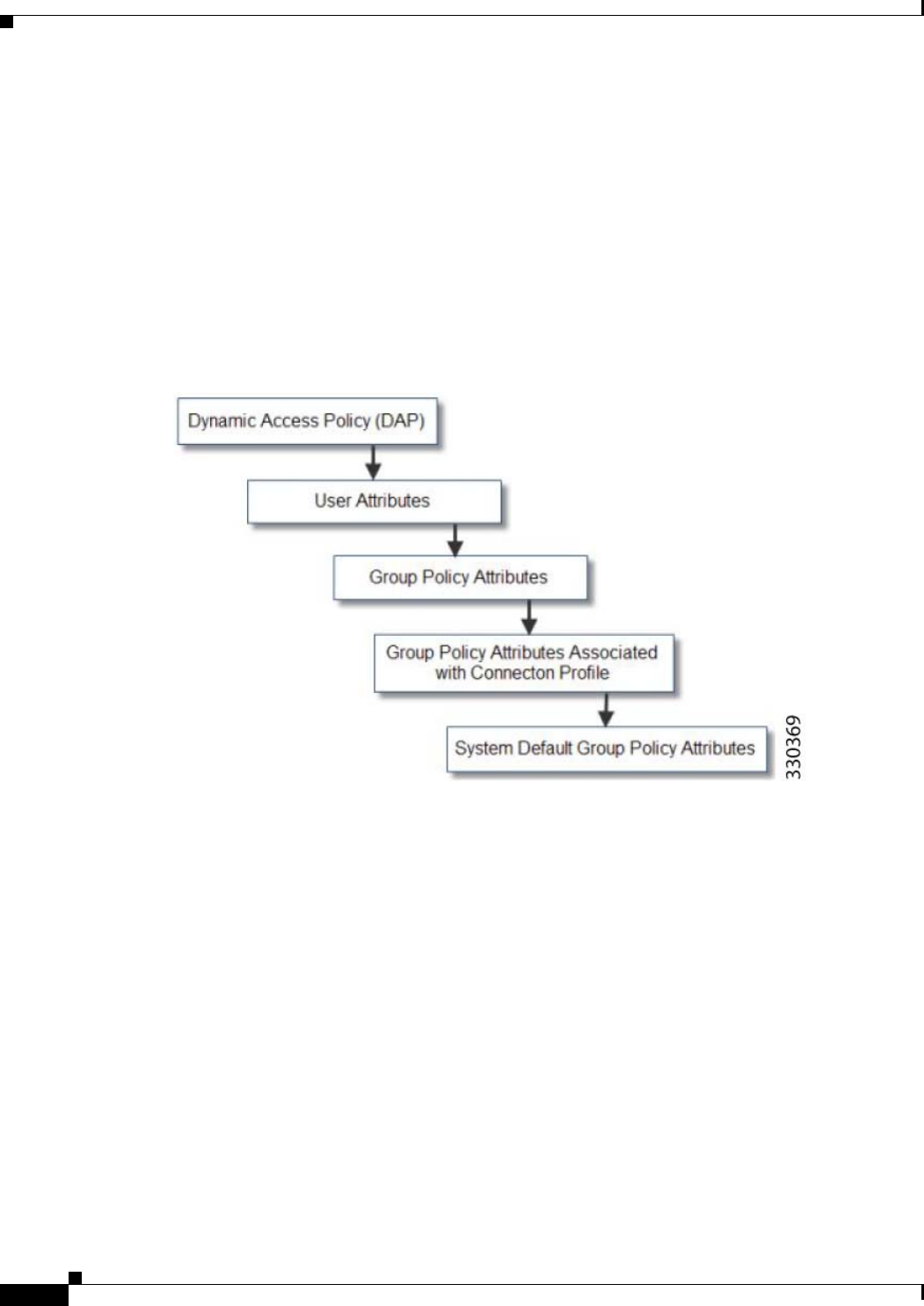
4. Group policy assigned by the Connection Profile (called tunnel-group in the CLI)—The Connection
Profile has the preliminary settings for the connection, and includes a default group policy applied
to the user before authentication. All users connecting to the ASA initially belong to this group,
which provides any attributes that are missing from the DAP, user attributes returned by the server,
or the group policy assigned to the user.
5. Default group policy assigned by the ASA (DfltGrpPolicy)—System default attributes provide any
values that are missing from the DAP, user attributes, group policy, or connection profile.
Figure B-1 Policy Enforcement Flow
Configuring an External LDAP Server
The VPN 3000 concentrator and the ASA/PIX 7.0 software required a Cisco LDAP schema for
authorization operations. Beginning with Version 7.1.x, the ASA performs authentication and
authorization using the native LDAP schema, and the Cisco schema is no longer needed.
You configure authorization (permission policy) using an LDAP attribute map. For examples, see the
“Active Directory/LDAP VPN Remote Access Authorization Examples” section on page B-16.
This section describes the structure, schema, and attributes of an LDAP server and includes the following
topics:
• Organizing the ASA for LDAP Operations, page B-3
• Defining the ASA LDAP Configuration, page B-5
• Active Directory/LDAP VPN Remote Access Authorization Examples, page B-16
The specific steps of these processes vary, depending on which type of LDAP server that you are using.


















