B-22
Cisco ASA 5500 Series Configuration Guide using ASDM
Appendix B Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
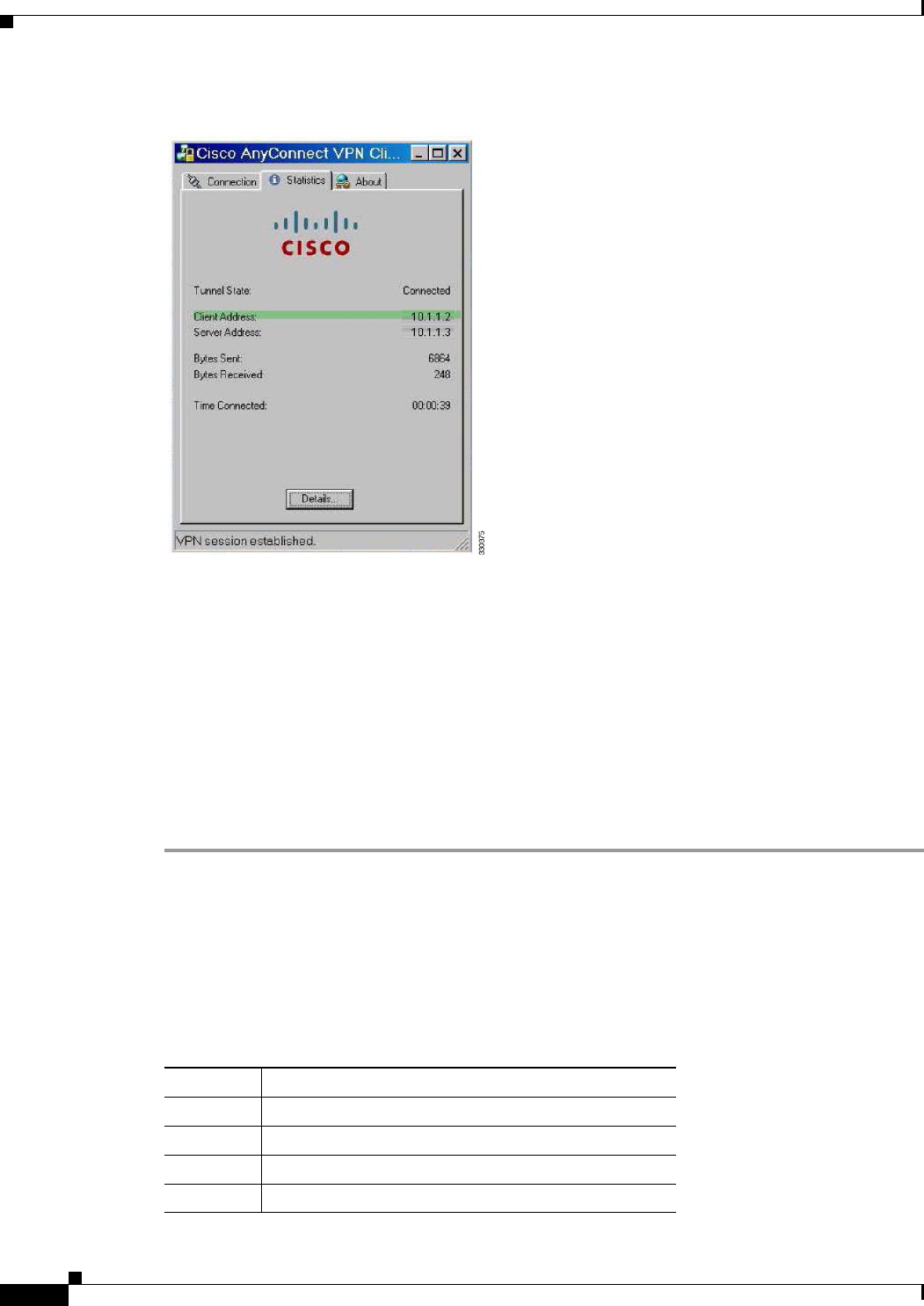
Figure B-8 AnyConnect Session Established
Step 7 Use the show vpn-sessiondb svc command to view the session details and verify the address assigned:
hostname# show vpn-sessiondb svc
Session Type: SVC
Username : web1 Index : 31
Assigned IP : 10.1.1.2 Public IP : 10.86.181.70
Protocol : Clientless SSL-Tunnel DTLS-Tunnel
Encryption : RC4 AES128 Hashing : SHA1
Bytes Tx : 304140 Bytes Rx : 470506
Group Policy : VPN_User_Group Tunnel Group : Group1_TunnelGroup
Login Time : 11:13:05 UTC Tue Aug 28 2007
Duration : 0h:01m:48s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
Enforcing Dial-in Allow or Deny Access
The following example creates an LDAP attribute map that specifies the tunneling protocols allowed by
the user. You map the allow access and deny access settings on the Dialin tab to the Cisco attribute
Tunneling-Protocol, which supports the bitmap values shown in Table B-6:
Table B-6 Bitmap Values for Cisco Tunneling-Protocol Attribute
Value Tunneling Protocol
1 PPTP
2L2TP
4
1
IPsec (IKEv1)
8
2
L2TP/IPsec