B-19
Cisco ASA 5500 Series Configuration Guide using ASDM
Appendix B Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
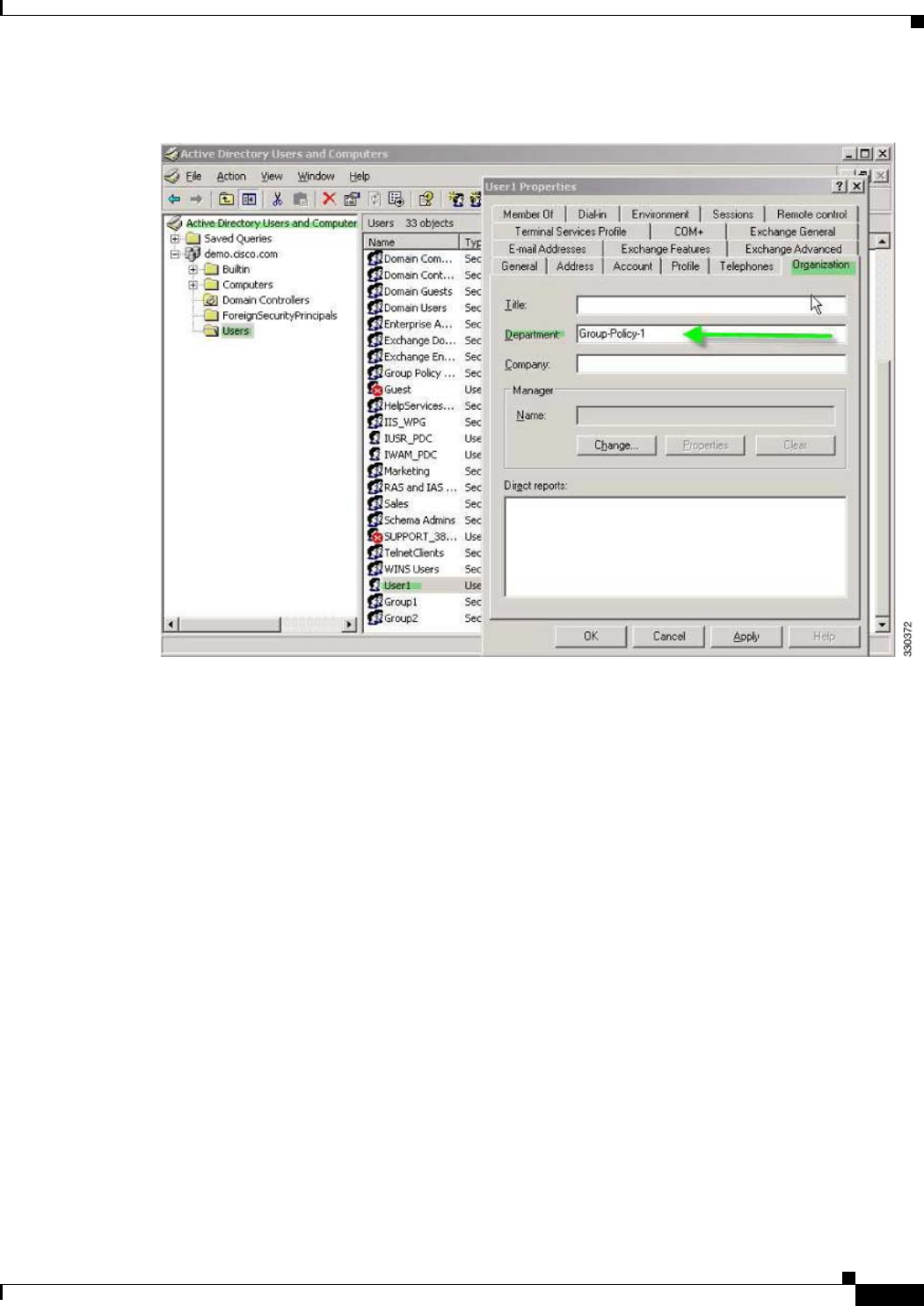
Figure B-5 AD/LDAP Department Attribute
Step 3 Define an attribute map for the LDAP configuration shown in Step 1.
The following example shows how to map the AD attribute Department to the Cisco attribute
IETF-Radius-Class.
hostname(config)# ldap attribute-map group_policy
hostname(config-ldap-attribute-map)# map-name Department IETF-Radius-Class
Step 4 Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2 in the AAA
server group MS_LDAP, and associates the attribute map group_policy that you created in Step 3:
hostname(config)# aaa-server MS_LDAP host 10.1.1.2
hostname(config-aaa-server-host)# ldap-attribute-map group_policy
Step 5 Add the new group-policy on the ASA and configure the required policy attributes that will be assigned
to the user. The following example creates Group-policy-1, the name entered in the Department field on
the server:
hostname(config)# group-policy Group-policy-1 external server-group LDAP_demo
hostname(config-aaa-server-group)#
Step 6 Establish the VPN connection as the user would, and verify that the session inherits the attributes from
Group-Policy1 (and any other applicable attributes from the default group-policy).
Step 7 Monitor the communication between the ASA and the server by enabling the debug ldap 255 command
from privileged EXEC mode. The following is sample output from this command, which has been edited
to provide the key messages:
[29] Authentication successful for user1 to 10.1.1.2
[29] Retrieving user attributes from server 10.1.1.2