68-30
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 68 Configuring IKE, Load Balancing, and NAC
Configuring Network Admission Control Policies
• Enable Audit—Click to pass the IP address of the client to an optional audit server if the client does
not respond to a posture validation request. The audit server, such as a Trend server, uses the host
IP address to challenge the host directly to assess its health. For example, it may challenge the host
to determine whether its virus checking software is active and up-to-date. After the audit server
completes its interaction with the remote host, it passes a token to the posture validation server,
indicating the health of the remote host.
• None—Click to disable clientless authentication and audit services.
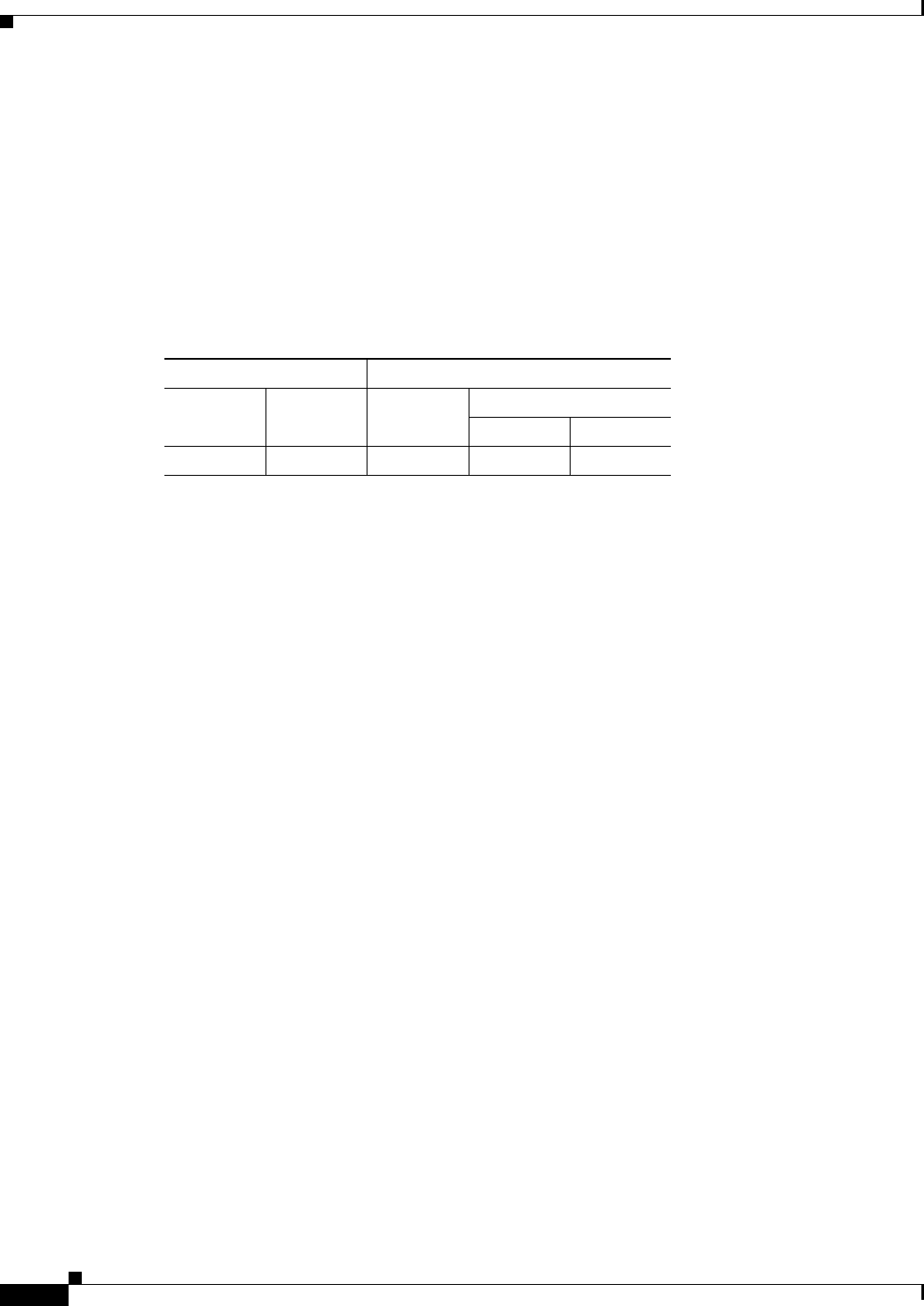
Modes
The following table shows the modes in which this feature is available:
Configuring Network Admission Control Policies
The NAC Policies table displays the Network Admission Control (NAC) policies configured on the ASA.
To add, change, or remove a NAC policy, do one of the following:
• To add a NAC policy, choose Add. The Add NAC Framework Policy dialog box opens.
• To change a NAC policy, double-click it, or select it and click Edit. The Edit NAC Framework Policy
dialog box opens.
• To remove a NAC policy, select it and click Delete.
The following sections describe NAC, its requirements, and how to assign values to the policy attributes:
• About NAC
• Uses, Requirements, and Limitations
• Fields
• What to Do Next
About NAC
NAC protects the enterprise network from intrusion and infection from worms, viruses, and rogue
applications by performing endpoint compliance and vulnerability checks as a condition for production
access to the network. We refer to these checks as posture validation. You can configure posture
validation to ensure that the anti-virus files, personal firewall rules, or intrusion protection software on
a host with an AnyConnect or Clientless SSL VPN session are up-to-date before providing access to
vulnerable hosts on the intranet. Posture validation can include the verification that the applications
running on the remote hosts are updated with the latest patches. NAC occurs only after user
authentication and the setup of the tunnel. NAC is especially useful for protecting the enterprise network
from hosts that are not subject to automatic network policy enforcement, such as home PCs.
The establishment of a tunnel between the endpoint and the ASA triggers posture validation.
Firewall Mode Security Context
Routed Transparent Single
Multiple
Context System
• — • ——


















