63-11
Cisco ASA 5500 Series Configuration Guide using ASDM
Chapter 63 Configuring the ASA CX Module
Configuring the ASA CX Module
• Divert traffic to the ASA CX module. See the “Redirecting Traffic to the ASA CX Module” section
on page 63-11.
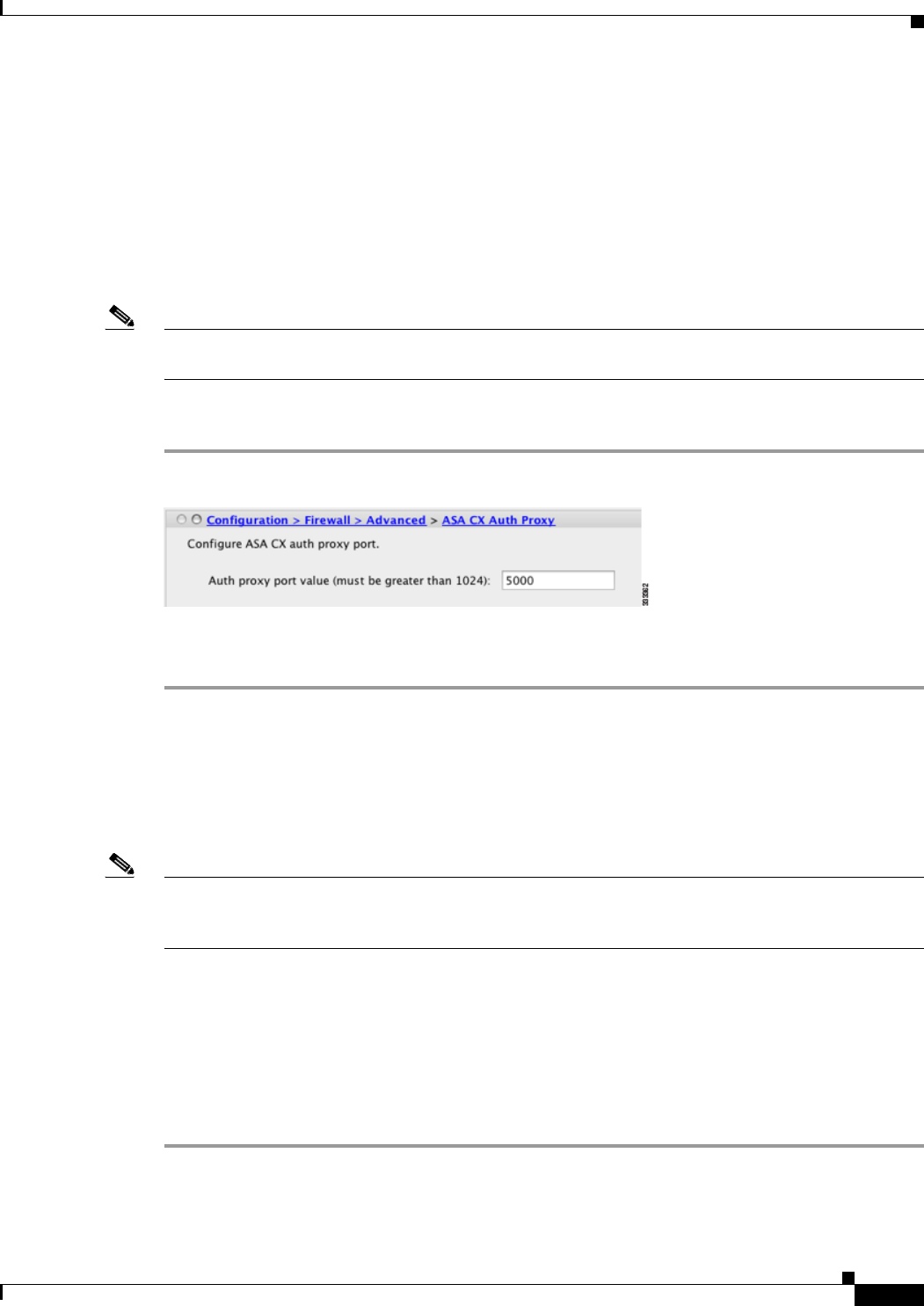
(Optional) Configuring the Authentication Proxy Port
The default authentication port is 885. To change the authentication proxy port, perform the following
steps. For more information about the authentication proxy, see the “Information About Authentication
Proxy” section on page 63-3.
Note You can also set the port as part of the ASDM startup wizard. See the “Configuring Basic ASA CX
Settings at the ASA CX CLI” section on page 63-8.
Detailed Steps
Step 1 In ASDM, choose Configuration > Firewall > Advanced > ASA CX Auth Proxy.
Step 2 Enter a port greater than 1024. The default is 885.
Step 3 Click Apply.
Redirecting Traffic to the ASA CX Module
This section identifies traffic to redirect from the ASA to the ASA CX module. Configure this policy on
the ASA.
Note When using PRSM in multiple device mode, you can configure the ASA policy for sending traffic to the
ASA CX module within PRSM, instead of using ASDM or the ASA CLI. However, PRSM has some
limitations when configuring the ASA service policy; see the ASA CX user guide for more information.
Prerequisites
If you enable the authentication proxy on the ASA using this procedure, be sure to also configure a
directory realm for authentication on the ASA CX module. See the ASA CX user guide for more
information.
Detailed Steps
Step 1 Choose Configuration > Firewall > Service Policy Rules.
